Cybersecurity has evolved from an IT challenge to a data challenge. The exponential growth of logs, alerts, and telemetry generated across countless sources has overwhelmed traditional cybersecurity tools, with SIEM systems bearing the brunt of this data deluge. Each year, SIEMs ingest more data sources, leading to bloated systems, spiraling costs, and operational inefficiencies. Meanwhile, cyber attackers are achieving lateral movement in just 18 minutes, leaving security operations teams struggling to keep pace.
Once seen as the solution to fragmented cybersecurity tools and sprawling data, the limitations of SIEMs are now evident: slow threat detection, high ingest costs, and complex data management. Security operations teams must rethink their approach. The answer lies in detecting before data is stored— directly at the source or as close to it as possible. There needs to be a fundamental shift in the way we use traditional detection pipelines in order to achieve faster, more effective threat detection.
The Problem with SIEMs
Latency and Delays
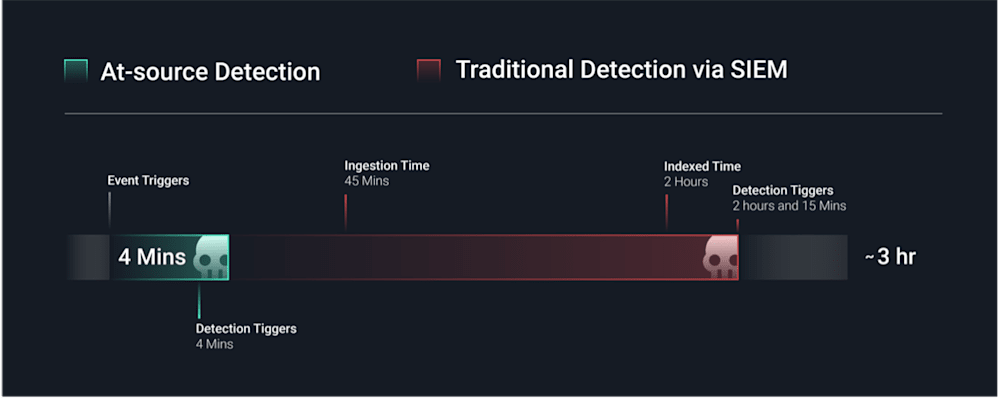
SIEMs introduce latency from ingesting, parsing, indexing, and correlating data—a process that could delay detection by up to three hours. Misconfigurations and scheduled alerting exacerbate these delays, putting teams on the back foot when detecting emerging threats.
Operational Complexity
Managing diverse log sources, parsing fields, and writing individual detection rules for multiple technologies requires significant resources. For overstretched teams, this complexity leads to inefficiencies and threats slipping through the cracks.
Lack of Agility
SIEMs rely on rigid data structures, making it difficult to adapt to new technologies or update detection rules. Manual migrations disrupt detection coverage, leaving gaps in protection and slowing response times.
Rising Costs
Constantly feeding vast amounts of data into a SIEM comes at a high price, with the overwhelming majority of enterprise companies ingesting over 1TB of data daily. This approach strains budgets while failing to deliver faster detection.
A Better Approach: Detecting Threats at the Source or in Transit
Faster Detection
Identify threats the moment they surface—whether directly at the source or as data moves across your environment. Detecting data before it is stored minimizes reliance on SIEMs for detection, enabling faster detection and response times.
Simplified Operations
Detection at the source or in transit eliminates the need to wait for storage or centralized processing. This simplifies operations, reduces configuration challenges, and frees your team to focus on proactive, strategic security efforts.
Lower Costs
By filtering and analyzing data before it is stored, it leaves only high-value events to be sent to your SIEM or storage. This reduces ingestion and licensing costs while preventing unnecessary data from clogging expensive platforms.
Where to Start: The Key to At-Source and In-Transit Detection
When shifting to faster, more effective detection, evaluate how different parts of your environment can benefit from at-source and in-transit detection:
Cloud Workloads: Dynamic environments generate high event variety but often have built-
Endpoints: With high-volume, noisy telemetry, filter and detect as close to the device as possible to prevent overload and catch early-stage threats.
Network Data: Rich in business-critical activity but can quickly become overwhelming. Use in-transit detection to correlate and spot lateral movement before logs reach your system.
The right approach combines both—detecting threats as close to the point of origin as possible and continuing to analyze as data moves through your pipeline. This gives you the flexibility to adapt as your architecture, tooling, and risk profile evolve.
How GreyMatter Makes It Possible
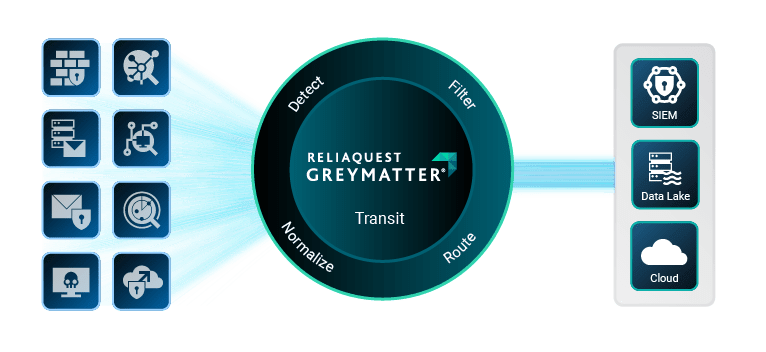
The ReliaQuest GreyMatter agentic AI security operations platform enables proactive threat detection—both at the source and in transit—before data lands in storage or SIEM. GreyMatter connects across cloud, endpoint, and network environments, leveraging bi-directional APIs and in-pipeline analytics for early, actionable insights.
For your security operations team, that means:
Faster Detection: GreyMatter applies detection logic at the source and as it moves through your pipeline, eliminating delays from ingest, parsing, and indexing. Threats surface in minutes, not hours.
Lean Data Storage: Filter and prioritize events in transit, ensuring only high-value data reaches your SIEM. This reduces storage demands and controls costs.
Centralized, Flexible Deployment: Manage detection logic centrally in GreyMatter, making it simple to adapt to new data sources or swap tools—without reconfiguring your environment.
Simplified Architecture: GreyMatter’s modular design integrates directly with your existing tools, enabling detection without disrupting coverage or adding complexity.
SIEM Optimization: GreyMatter Transit filters out noise and routes nonrelevent telemetry away from SIEM, ensuring only actionable, high value events are ingested. This frees up your SIEM to focus on deep threat investigations and advanced analytics—boosting performance while reducing clutter.
Lower Costs: Detecting threats at the source and in transit means less redundant data sent to SIEM, reducing licensing and storage costs.
Why SIEMs Need a Supporting Role—Not Center Stage
SIEMs excel at deep investigations and complex analytics, but their legacy, storage-first design can slow you down when speed matters most.
Instead of sending every event to your SIEM, leverage at-source and in-transit detection to identify threats early and filter out noise before it hits your platform. Complementary solutions like data lakes can manage long-term retention, while your SIEM can focus on high-value threat analysis and advanced investigations.
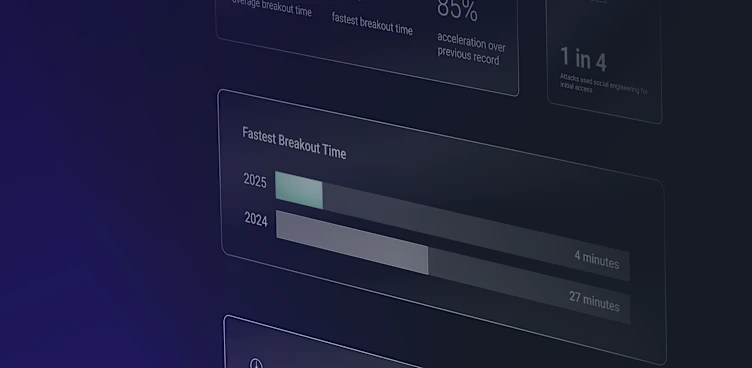
92% Faster Threat Detection with At-Source and In-Transit Detection
A ReliaQuest customer reduced SIEM ingest by 860GB per day across cloud and endpoint data, saving 43% on licensing utilization and costs while accelerating MTTD by 55 minutes, or 92%. By detecting threats at the source, the customer achieved faster response times and cut SIEM costs without sacrificing detection coverage.
The Time to Rethink SIEM Strategy Is Now
As cyber threats evolve, yesterday’s SIEM strategies are no longer enough— security operations teams must prioritize speed and scalability in their detection strategies. GreyMatter empowers teams to detect and respond to threats faster, reduce costs, and streamline operations, giving them the edge to stay ahead of attackers.