Editor’s note: This report was authored by Gautham Ashok.
Key Points
“Sinobi” data-leak site postings surged 306%, making it a top three ransomware group in Q4.
“Clop” returned with a vulnerability-led campaign, exploiting CVE-2025-61882 to drive a short, high-volume wave of data theft extortion. Such mass exploitation of zero days in widely deployed enterprise software is a recurring risk for organizations.
Data-leak site activity dipped after Q3’s record numbers, but the overall landscape volatility remains high.
The late surge of “LockBit 5.0” suggests temporary re-centralization around high volume groups; however, the landscape will likely continue to fragment across sectors and geographies.
In the final quarter of 2025 (Q4 2025), established groups like “Qilin” and “Akira” maintained their leadership positions, while newer operators like “Sinobi” gained traction.
In addition, the number of data-leak site posts increased by 50% between Q3 and Q4 2025, and was up 40% from Q4 2024, despite fewer active groups this quarter.
We assess with moderate confidence that this reflects short-term consolidation, where higher-output groups attacked more organizations as weaker operators lost momentum.
Regardless of which groups rise or fall quarter to quarter, the sustained increase in data-leak site posts emphasizes that ransomware remains a persistent, growing threat even as individual group names come and go.
The quarter was characterized by the following developments:
Sinobi’s rapid expansion: Listings attributed to Sinobi rose 306%, making it Q4's third-most active group. This increase likely reflects affiliate migration from declining operations like “Lynx” ransomware.
Clop’s operational resurgence: After minimal Q3 activity, “Clop” claimed 116 victims through mass exploitation of a widely used enterprise resource planning (ERP) solution software platform.
Sectoral variations: Traditional high-value sectors—professional, scientific, and technical services (PSTS), manufacturing, and health care—remained the most affected industries, while retail trade experienced a 152% spike, likely driven by opportunistic holiday-season targeting.
By analyzing the drivers behind these trends and their downstream impact across industries, this report provides organizations with actionable insights to stay ahead of both established and emerging ransomware threats.
Silent Operator: Sinobi Rises to Q4 Prominence
Sinobi’s data-leak site listings rose 306% in Q4, making Sinobi the third-most active ransomware group in Q4, behind only Qilin and Akira. Sinobi emerged in July 2025 and is likely a rebrand or offshoot of “Lynx” ransomware.i For security teams, this means detections used to disrupt Lynx intrusions should remain effective for Sinobi, as long as they’re engineered around the group’s tactics, techniques, and procedures (TTPs).
Like many ransomware groups, Sinobi’s advantage isn’t its novelty. Instead, it’s disciplined Living-off-the-Land (LotL) execution that hides in plain sight. Rather than deploying signatured malware, affiliates use tools that already exist in Windows environments: PowerShell for privilege escalation and lateral movement, and legitimate remote administration software for persistence. Sinobi intrusions also feature repeatable patterns, including creation of new administrator accounts, exploitation of endpoint vulnerabilities, and Rclone-based data exfiltration.
Many EDR tools are optimized to catch “known bad” binaries, so LotL activity can look like routine administration unless detections are finely tuned to anomalous behavior. The net effect is delay: Teams may not recognize the intrusion until data theft is underway. At that point, speed becomes key. Containment must happen in minutes, not hours, to prevent intrusions from becoming extortion events.
Sinobi’s Q4 surge and sustained month-over-month output (see Figure 1) also indicate rapid affiliate migration from Lynx. The group's shared technical heritage likely creates a frictionless transition for affiliates, as operators familiar with Lynx's infrastructure would face little difficulty when switching to Sinobi. Unlike Qilin and “DragonForce,” Sinobi has no known presence on cybercriminal forums for recruitment activity. This limited footprint reduces threat intelligence visibility into how Sinobi may onboard affiliates and evolve its tool set, which, in turn, makes the group harder to profile. For organizations, prioritize TTP-based detections and continuous validation over group-specific tracking, as even highly visible groups can change rapidly.
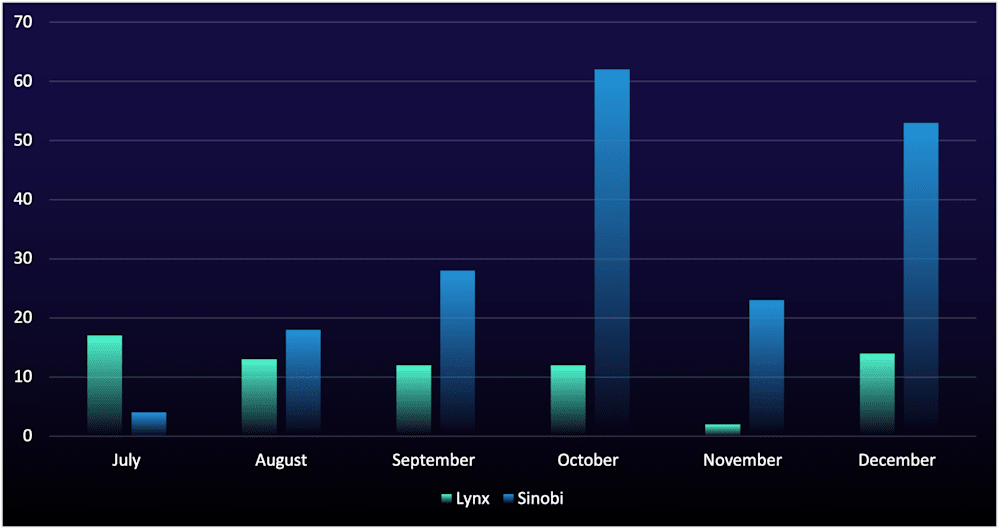
Figure 1: Number of compromised organizations listed on Sinobi and Lynx data-leak sites, Q3 and Q4 2025
Step Up Your Defenses Against Sinobi
Sinobi relies heavily on legitimate administration. Focus on hardening remote access with phishing-resistant MFA and conditional access. Detect behaviors that reliably separate attackers from routine IT activity: suspicious interactive PowerShell, new admin account creation or privilege changes, security tool tampering, and Rclone-based exfiltration. Pair these detections with fast, agentic AI-powered containment actions to shrink attacker dwell time and limit their reach within networks.
Clop’s Latest Campaign Mirrors Historical Patterns
Clop re-emerged after minimal activity in Q3, rising from one organization listed in Q3 to 116 in Q4. This surge was driven by the group’s mass exploitation of CVE-2025-61882—a pre-authentication, internet-reachable remote code execution (RCE) flaw—in Oracle EBusiness Suite (EBS). Exploitation required no user interaction and no credentials and targeted a high-value platform that centralizes sensitive corporate data.
Attackers sent specially crafted HTTP requests to achieve code execution on the targeted servers, using server-side request forgery (SSRF) to force vulnerable servers to download and run malicious code. Following exploitation, Clop operators used reverse-shell commands (such as /dev/tcp) to gain control of compromised servers. The campaign created simultaneous exposure across enterprises and service providers that run the impacted software on customers’ behalf.
What differentiates Clop from other ransomware groups is its planned, vulnerability-led campaigns and focus on software supply chains, often built around high-impact zero-days. Clop doesn’t run continuous, opportunistic operations; instead, its affiliates invest resources in finding or acquiring zero-day vulnerabilities in internet-exposed platforms that handle sensitive data and are widely deployed across enterprises. We have previously noted that the most coveted zero-days are for enterprise and networking platforms. This is due to their versatility, profitability, and cascading impact, fueled by the cybercriminal ecosystem that enables buying, selling, and brokering zero-days.
This Q3 campaign also matched Clop’s signature surge-and-dormancy cadence. Limited activity in late October, a sharp spike through November, then a rapid drop-off in December (see Figure 2) mirrors prior Clop operations against widely deployed enterprise platforms, where Clop weaponized application-layer flaws to compromise victims at scale, prioritized data theft and extortion, and then went quiet.
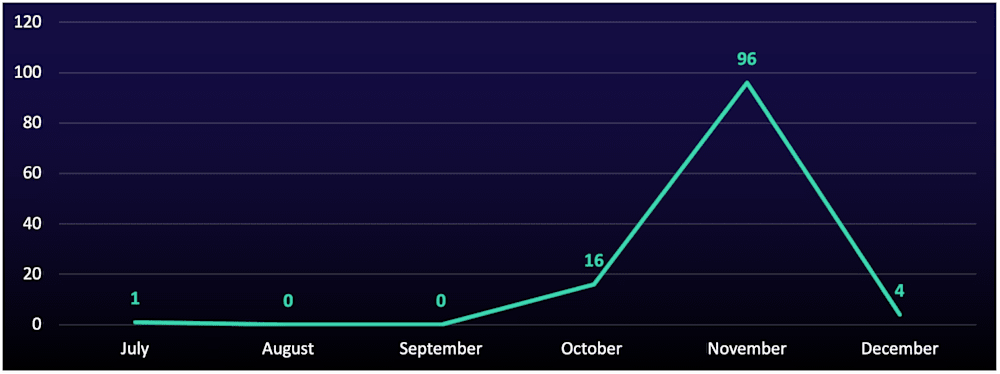
Figure 2: Number of Clop ransomware victims from July to December 2025
This model creates software supply-chain risk, where zero-day flaws can invalidate even mature perimeter and endpoint assumptions. Once a zero-day exploit becomes available, mass exploitation can follow within hours. That speed widens the visibility gap for endpoint-led defenses: EDR tools may catch post-exploitation actions, but they cannot see the initial code execution inside the application process.
Step Up Your Defenses Against Clop
Clop campaigns test defense-in-depth (DiD), not just patching speed. Maintain a current inventory of internet-facing software components and any externally exposed managed file transfer (MFT) platforms. Pre-stage an emergency patch workflow so patches can move from release to deployment quickly. When immediate patching is not possible, reduce exposure with controls that match Clop’s exploitation style: strict IP allowlisting to administrative and application endpoints, and segmentation that prevents an MFT application server from directly reaching file shares, identity systems, and backup infrastructure.
Because Clop operations are typically exfiltration-first, prioritize controls that detect and disrupt data theft from application servers. Extend logging to the data Clop goes after—ERP exports, finance tables, and file repositories connected to MFT software—so security teams can detect staging and outbound movement before the leak-site timer starts
The Current Landscape: New Groups and Top Trends
Data-Leak Sites Pull Back After Q3 Record High
After hitting a record 84 active data-leak sites in Q3, the ecosystem contracted in Q4, with the number of active data-leak sites falling to 77 (see Figure 3).
This decrease doesn’t mean reduced ransomware risk. Rather, it indicates short-term concentration, where fewer groups generated more volume. In other words, Q4 reflects a momentary re-centralization of activity into higher-output operations, not a meaningful collapse of the ecosystem.
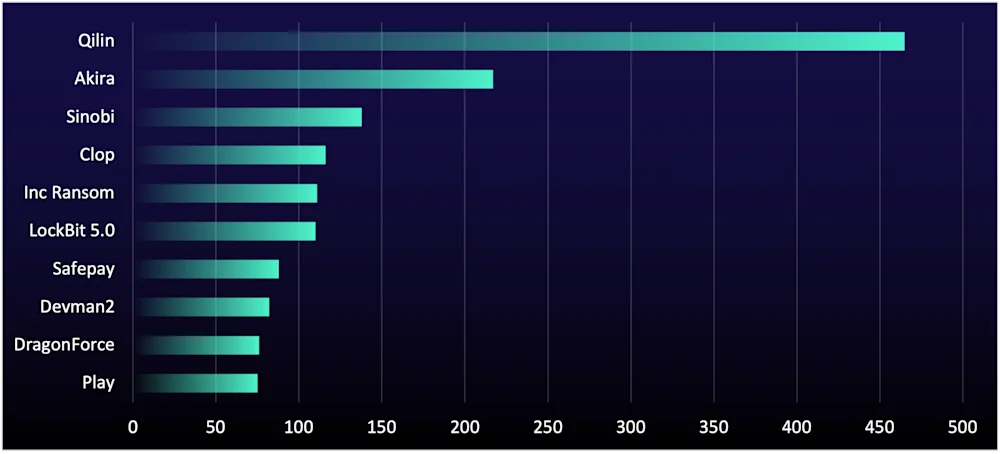
Figure 3: Active data-leak sites from Q1 2022 to Q4 2025
When dominant groups emerge, affiliates often consolidate around them, with mid-tier groups losing momentum quickly. That said, affiliates routinely splinter, rebrand, and launch new leak sites after short peaks, and leak-site counts can rebound quickly as smaller groups re-emerge or new operators appear. As we’ve previously noted, fragmentation is a defining feature of the ransomware landscape, so group churn is to be expected.
The key takeaway for organizations is to defend against techniques, and not just track data-leak sites. Groups may disband, affiliate rosters may churn, and tools may get slicker, but attack patterns stay stubbornly familiar quarter after quarter. If security teams can reliably detect and disrupt credential-based access, LotL-based lateral movement, privilege escalation, and data exfiltration, then networks will remain resilient to whichever dominant group of the quarter. The priority is to keep detections tuned and contain fast enough that intrusions don’t become extortion events.
Qilin Holds Firm, While LockBit 5.0 Sees Late Surge into the Top Ten
Top-tier ransomware-as-a-service (RaaS) programs are optimizing for speed and cross-environment execution, which is compressing time-to-impact for defenders. In Q4, Qilin remained the clear frontrunner in terms of organizations impacted (see Figure 4), with its performance supported by investments in automation, customization, and advanced features. These capabilities don’t just increase victim counts, they enable affiliates to move faster, tailor deployment to the environment, and sustain operations long enough to succeed against well-defended enterprises.
Automation accelerates the attack chain (from initial foothold to lateral movement and deployment), while customization helps affiliates tailor execution, evade controls, and maximize operational disruption. Organizations should expect faster breakout times and higher blast radius when Qilin attacks an environment, making rapid detection correlation and automated containment essential.

Figure 4: Number of compromised organizations listed on data-leak sites by ransomware groups, Q4 2025
Meanwhile, the return of LockBit 5.0 was one of Q4’s biggest shifts, driven by a late-quarter spike that saw the group list 110 organizations in December alone. This output signals a group that can scale execution quickly, convert intrusions into impact, and sustain an affiliate pipeline capable of operating at volume.
LockBit 5.0 offers modular variants for Windows, Linux, and VMware ESXi, alongside features designed to speed execution and reduce defender visibility, i.e. stronger obfuscation and evasion, the ability to disable security tools, and log clearing. LockBit 5.0 is disproportionately dangerous for large enterprises given its ESXi capability, as bulk virtual machine (VM) encryption can disrupt critical applications, shared services, and operational workloads.
This modularity also likely explains the affiliate surge behind December’s volume. LockBit 5.0 can accommodate different levels of affiliate maturity without forcing every operator into the same technical path:
Less sophisticated affiliates can still make money in Windows-heavy environments where credential abuse and remote execution are familiar.
More experienced operators can focus on Linux-based tech stacks and high-value application backends.
The most technical operators can pursue ESXi or hypervisor-centric operations, which are harder but yield the highest leverage by knocking out entire VM fleets quickly.
In other words, LockBit’s platform design increases the addressable market of affiliates: It gives mid-tier operators a reliable playbook while giving elite teams a route to maximum blast radius. For defenders, LockBit 5.0’s resurgence signals ransomware programs are optimizing for cross-environment execution.
PSTS Attacks Remain Dominant as Threat Actors Hit the Supply Chain
In Q4, posts impacting the PSTS sector on data-leak sites jumped 77% (from 415 in Q3 to 736 in Q4), making it the fastest-expanding industry vertical (see Figure 5). Even if your own sector wasn’t heavily affected, it’s likely your business relies on PSTS firms such as law firms, consultants, accountants, and engineering partners.
These relationships create a data and access supply chain that attackers love to exploit. When PSTS organizations are impacted, exposure expands through shared documents, privileged support access, or integrations.
Two Q4 dynamics likely amplified PSTS exposure: Firstly, Clop’s vulnerability-led campaign against a widely deployed enterprise platform produced downstream impact across service firms that run, administer, or support client ERP environments; and secondly, Akira’s repeated exploitation of SonicWall SSL VPN weaknesses created a reliable path into service providers with complex remote access and decentralized IT.
This risk grows when security debt related to mergers and acquisitions (M&A) leaves inherited VPN infrastructure unpatched, privileged access sprawling across subsidiaries, and logging or endpoint controls uneven. In these conditions, a compromise in a smaller acquired environment can become a stepping stone into larger enterprise networks.
Retail trade experienced a spike in attacks in Q4, which fits the same supply-chain picture. Retail trade posts rose 152% (58 in Q3 to 146 in Q4), aligning with predictable holiday-season targeting. However, this surge also connects to the wider PSTS story. Retailers depend heavily on PSTS partners for legal support, payment and e-commerce consulting, digital agencies, logistics advisory, and outsourced IT.
Attackers don’t have to choose between retail trade and PSTS: Compromising a PSTS provider can be an efficient route into retail trade while creating parallel opportunities across the provider’s broader client base. For defenders, this means third-party access paths and vendor incident response readiness should be treated as core ransomware controls, not compliance checkboxes.
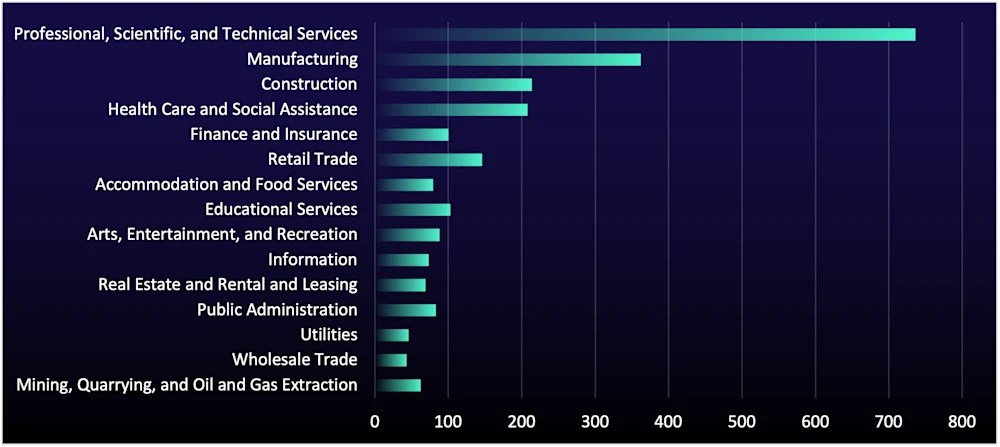
Figure 5: Number of organizations listed on data-leak sites, by sector, in Q4 2025
Big Markets Stay in the Crosshairs, Smaller Markets Spike and Fade
In Q4, geographic victim trends reinforced a consistent pattern: Targeting remains stable at the top and volatile below. For instance, the US remained the most-affected market, with its data-leak site listings even increasing by 51% (from 897 in Q3 to 1,359 in Q4). Treat these numbers as baseline reality, not a new signal. Large, digitally exposed economies with high payment potential and mature commercial ecosystems stay near the top because they offer both scale and dependable monetization.
Below the top tier, country rankings are far less stable quarter to quarter. Smaller markets are common staging points for ransomware groups. In these countries, spikes are often campaign artifacts rather than a durable geographic strategy. A single vulnerability wave—or one ransomware group shifting focus—can push a country into the top ten only for it to disappear the next quarter. Thailand illustrates this churn, with listings surging in Q3 largely due to activity from “Devman2,” then dropping out of the top ten in Q4.
This quarter’s jump in posts targeting the UAE (see Figure 6) should be read through the same lens, with a clear enterprise relevance filter. Targeted organizations rose from 7 to 41 listings, which is meaningful if you operate there. For multinationals with UAE subsidiaries, the takeaway is to prioritize security parity across regions, since smaller offices and regional IT stacks are frequently less monitored and can become a backdoor into the global environment. For organizations without a footprint in the region, the UAE spike is best interpreted as another example of opportunistic targeting. It reinforces the broader point that country-level volatility is often the output of transient campaigns, while the top markets remain persistently attractive year-round.
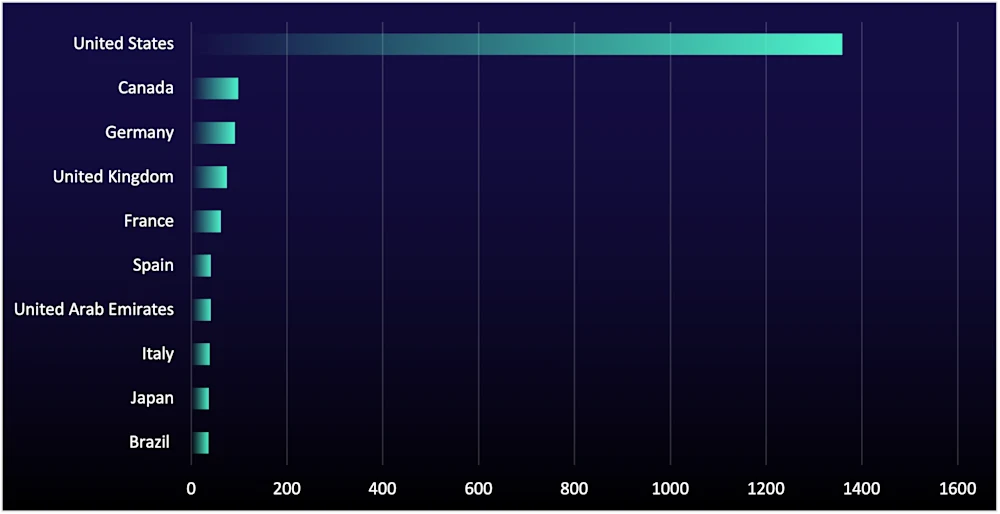
Figure 6: Number of organizations listed on data-leak sites by country, Q4 2025
Step Up Your Defenses Against Ransomware
ReliaQuest’s Approach
ReliaQuest GreyMatter uses agentic AI to optimize security operations, empowering customers to accelerate threat detection, containment, investigation, and response to ransomware incidents. GreyMatter Workflows enables greater customized automation, supporting rapid, repeatable containment actions when breakout times are short.
GreyMatter Transit can detect threats as data moves between its source and storage, aligning with the quarter’s emphasis on exfiltration-led extortion seen in Clop-style campaigns and ransomware operations that prioritize data theft before, or instead of, encryption.
Using GreyMatter’s detection rules alongside the following GreyMatter Automated Response Playbooks, organizations can contain ransomware threats in as little as five minutes:
Reset Passwords and Terminate Sessions: Force password resets and revoke active sessions to cut off credential-based access used by ransomware operations like Sinobi and stop continued lateral movement after initial access.
Isolate Host: Immediately disconnect compromised hosts from the network to prevent data staging and exfiltration (for example, Rclone activity) and contain spread before ransomware deployment impacts additional systems.
Disable User: Disable compromised accounts to block privilege escalation and persistence and minimize the likelihood of attackers transitioning from reconnaissance and data theft to encryption.
Your Action Plan
Q4 ransomware activity was driven by the continued success of established tactics. Vulnerability-led mass compromise by threat actors remains effective because it exploits persistent weaknesses. Threat actors rely on this method, because organizations are frequently slow to patch, don’t enforce strong access controls, and struggle to detect data exfiltration early. To improve resilience against these threats, prioritize the following steps:
Harden Remote-Access Controls: Prioritize remote-access paths, especially VPN and administrative access. Enforce phishing-resistant MFA and strict conditional access to reduce credential-driven intrusions associated with LotL tactics and VPN exploitation activity against exposed edge devices.
Strengthen Data Exfiltration Monitoring: Treat exfiltration as the primary extortion lever for the ransomware groups highlighted in this report. Tune detections for bulk transfers and common tooling such as Rclone. Alert on unusual outbound volume from ERP and application servers—a critical step for data theft campaigns that don’t rely on widespread encryption.
Secure High-Impact Shared Infrastructure: Protect systems that turn ransomware into an enterprise-wide outage. Focus hardening and monitoring on virtualization platforms such as VMware ESXi, identity, and backups, because ESXi targeting can rapidly expand blast radius across large, virtualized networks.
Key Takeaways
In Q4, the ransomware landscape continued to shift, but largely through the scaling of proven tactics rather than the introduction of new ones. Established leaders such as Qilin and Akira maintained their dominance. While victim listings rose sharply from Q3, fewer groups posted victims, indicating short-term consolidation around higher-output groups. We assess this consolidation is unlikely to persist over the long term, given the ransomware ecosystem’s tendency to fragment and churn. Q4 also highlighted how quickly ransomware momentum can change. Sinobi’s rapid rise alongside Lynx’s decline points to affiliate migration, while Clop’s return reinforces the recurring cycle of vulnerability-led mass compromise followed by periods of inactivity. LockBit 5.0’s late surge in Q4 and cross-platform capabilities suggest well-resourced programs can scale rapidly when conditions are favorable. Meanwhile, sectoral and geographical metrics outside the largest markets remain volatile, implying continued opportunistic shifts.