Explaining Threat Detection
Threat detection is what puts companies on even playing fields with attackers, revealing malicious activity and insider threats so security teams can block them before they turn into breaches.
Without effective threat detection, organizations are flying blind in the face of serious threats to their sensitive data. Advanced and proactive threat detection mechanisms are quickly overtaking insufficient traditional techniques, and are strong enough to help security operations centers (SOC) catch insider attacks, advanced persistent threats, ransomware, AI-powered exploits, and more.
Internal and External Threat Intelligence
Today’s cybersecurity threat detection mechanisms span internal and external sources, bringing both known and unknown risks to light to prevent cyberattacks.
Internal (In-house)
SIEMs
Data lakes
Endpoint detection and response (EDR)
Forward proxy detection
IAM and MFA solutions
Email security tools
Firewalls
Intrusion Detection Systems (IDS)
External
Open-source threat intelligence feeds
ISACs, ISAOs
Government agencies like CISA
Commercial threat feeds
Dark web
Social media
All contribute to the detection process and tell SOCs what cyber threats look like, where they come from, and what they can do.
The Threat Detection Process
Analysts scour logs, advisories, and all available telemetries for signs of malicious behavior. Once a threat is caught, the next steps include:
Creating an alert: Security teams enrich notifications with additional context and build the attack story piece by piece. This can take a long time for SOCs still orchestrating threat intelligence by hand. But only by correlating these various signals can relevant, worthwhile alerts be created. These then drive SOC behavior.
Threat containment: Now, your team is ready to move. Threat containment involves stopping the danger from spreading as quickly as possible: limiting network access, quarantining infected systems, leveraging firewalls.
Incident response: At this point, it’s time to root the problem out. Incident response means eradicating the problem completely – neutralizing ransomware, for instance – and getting everything to a pre-incident state (backups, decrypting data, re-establishing communication channels).
Types of Threat Detection
The face of cybersecurity threat detection is changing as the landscape does. There are now several types, and each brings different things to the table. They reflect an overall evolution from “standard practice” threat research to more advanced, proactive methods of determining risk.
Traditional Threat Detection Tools
Traditional threat detection software means a range of different tools – SIEMs, EDR, Cloud, etc. - that does your dirty work and give you the threat data you need. What SOCs end up with is multiple data streams coming from multiple places, and a big, siloed mess on their hands. Now they are left with the task of normalizing the data, removing false positives, enriching alerts, eliminating duplicates, and orchestrating everything into action. This technology-by-technology approach is slow, disjointed, and inefficient.
Not only does it result in detection lags (as your SOCs run back and forth aggregating the data from multiple sources), but it can also create coverage gaps. The end result? More work for less payout.
Advanced Threat Detection Methods
Advanced threat detection methods start to bring everything together. They reach across tools and domains to create a single source of truth where threat intelligence is concerned. Here, cutting-edge technologies like machine learning and AI come into play in real-time. They identify complex threats earlier in the lifecycle, offering things like:
Anomaly Detection: Behavioral analytics show when actions deviate from the standard baseline
Risk-based Detection: Risk profiles generated from user and asset data detect unwanted gaps
For example, if there is significantly more data being transferred from a system than is usual, advanced threat detection software will catch it, flagging it for further investigation. In a traditional approach, out-of-the-norm behavior like this might go unnoticed. After all, busy SOCs have enough on their plates hunting down hundreds of alerts a day from multiple, unconnected sources.
Proactive Threat Detection Techniques
Proactive threat detection techniques take threat finding to the next level. This isn’t setting a trap and seeing how it goes. It’s making sure your traps are optimized, strategized, and tracked.
This means creating your own comprehensive detection library, rather than relying on one-off detections. It means testing and validating your detections to make they don’t trigger too many false positives. And it means strategically deploying detections based on how you want to catch your threats – and what you’re up against:
Email or Endpoint Tool: Catch potential threats where they originate to cut costs and increase scalability
SIEM or Data Lake: Better for complex, custom, or compliance-driven detections
And finally, it means tracking the success of your detections against frameworks like MITRE ATT&CK and establishing KPIs to proactively keep pushing ahead. This all leads to detections that work right the first time, promoting agility, efficiency, and resilience.
The bottom line is that proactive threat detection techniques (otherwise known as “detection engineering”) are critical to your program saving you cycles – not creating more work. Fail to make these proactive adjustments ahead of time and your SOC is left picking up the pieces: more manual sifting, sorting, and waste. For a deeper dive into the proactive threat detection discussion, including:
Testing and validating detections
Deciding on the right deployment strategy
Basic, Intermediate, and Advanced detections

How Do You Create an Efficient Threat Detection Strategy?
As efficient cybersecurity threat detection strategy is comprised of four things:
Research and Build your Detection Library: A detection library is a software bank of tools and processes used to catch threats; these are the algorithms used to spot anomalies, patterns, and objects within network traffic and internal architecture. Building a comprehensive detection library suited to catching a wide range of threats is better than building one-off detections geared only to catch a certain type.
Test and Validate your Detections: Vet your detections to make sure they work – efficiently. Are they catching too many false positives? Is the logic syntax intact, or are there misplaced semicolons somewhere? Is the data properly ingested and stored? Better to repair the nets now than at the time you’re fishing.
Determine How You Will Deploy Detections: There are two key ways to do this. One, deploy on a storage solution like a SIEM or data lake: this is best for custom, compliance-driven detections. Or deploy at the source, like on an EDR or email tool: this is the fastest way and gives you the best out-of-the-box performance from your vendor-authored detections.
Measure Performance: As you go, you will refine your detections to optimize them for your particular threat environment. The only way to see how they’re doing is to track their progress. Compare against MITRE ATT&CK, monitor KPIs, and use that input to tweak and rewrite your detection logic as necessary.
The Role of AI in Threat Detection
SOCs can’t do everything by hand. To accomplish threat detection - and more specifically, advanced threat detection and proactive threat detection - at scale in a modern environment, AI/ML needs to be infused in the process.
AI for Automated Threat Detection
AI, and Agentic AI in particular, can automate a large part of the threat detection process. With AI threat detection, security teams can:
Contain threats in minutes: An automated threat detection platform instantly identifies and analyzes threats, prioritizes them, and contains them without human intervention. For example, it can go from ransomware detection to automatic removal without the need of a SOC.
Cut down on Tier 1 and Tier 2 tasks: Today’s SOCs are overwhelmed with unnecessary tasks – monitoring, investigations, enrichment. Automated threat detection tools perform low-level cybersecurity threat detection functions so teams can reserve their time for more important things, like threat hunting.
Prioritize business objectives: Even though there might be a high-priority CVE, that particular vulnerability may not be the thing causing the greatest risk to your enterprise. Automated threat detection solutions present comprehensive threat information so SOCs can quickly evaluate what is most business critical.
Essential to AI threat detection is the role of Generative AI. GenAI is used widely throughout any advanced threat detection and proactive threat detection platform to do the mundane work of human threat hunters, but faster, more accurately, and at scale.
The Benefit of AI in Threat Detection
What were once seen as benefits are all but seen as necessities now. Threat actors are leveraging AI to force-multiply the speed and success of their tactics. Without AI threat detection tools, organizations don’t stand a chance of beating threat actors at scale.
Bolstered with an AI agent, threat detection software platforms can deliver unmatched performance. And given the fact that attackers are getting faster than ever, they’ll have to.
According to recent research, it can take as little as 48 minutes for attackers to go from initial access to a lateral movement that could jeopardize data. Says Irene Fuentes McDonnel, a cyber threat researcher at ReliaQuest, “This quicker infiltration leaves organizations with even less time to respond, making automated defenses crucial in matching—and surpassing—the speed of adversaries.”
Threat Detection and Response
As we’ve seen with AI, threat detection is best served when it automatically leads into threat response. Typically, the threat detection, investigation, and response (TDIR) process is done by hand. SOCs vet the threat information, determine what’s important, and pursue it.
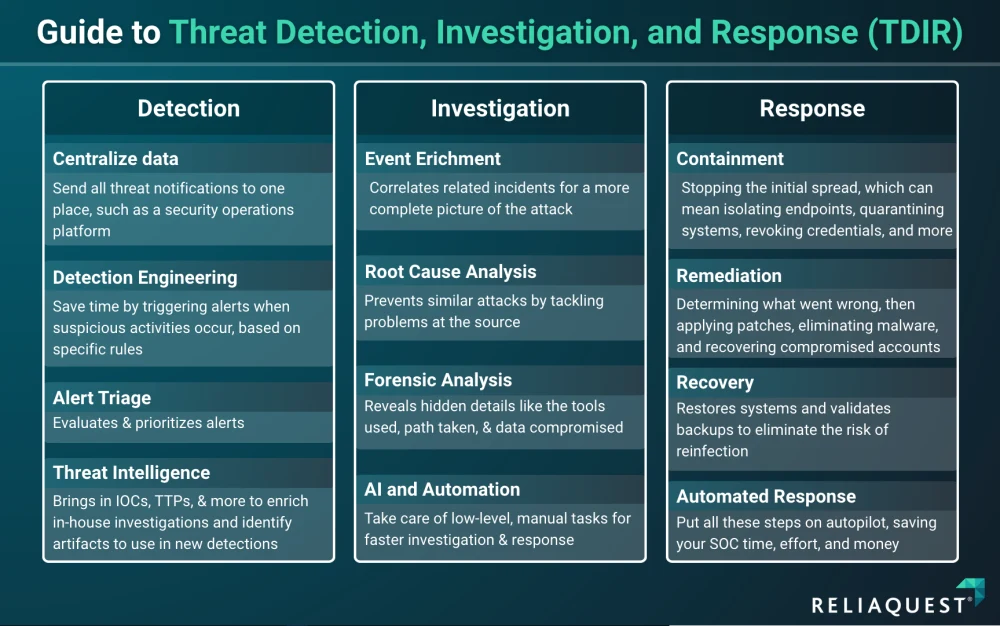
Challenges in Threat Detection
Eluding Endpoint Detection
Endpoint detection and response (EDR) is certainly helpful to detect a large swath of potential threats at the point of entry. But many confuse it with the end-all-be-all of threat detection software, and it’s not.
Unfortunately, while EDR covers a lot, there are still plenty of threats that evade endpoint detection. These include:
Email account takeover
Adversary in-the-middle
SaaS-targeted cyberattacks
As Chris Morgan, Senior Cyber Threat Analyst and ReliaQuest, states, “EDR isn’t foolproof; it can miss sophisticated threats, relies heavily on timely updates and accurate threat intelligence, and cannot monitor several physical and virtual appliances that operate outside its scope of visibility.”
What it “cannot monitor” can still lead to a data breach, making it necessary to go beyond built-in threat detection and response tools like EDR alone.
Solving the Wrong Problems
Most threat detection software on the market tackle the problem by providing one of two solutions:
A single platform to handle all your threat detection needs (EDR, SIEMs, firewalls)
Building, deploying, and managing detections for you
However, these solutions are incomplete and create additional problems.
Lack of Transparency: Many use a black-box approach, keeping organizations in the dark about how well detections are really doing.
High Cost for Data Centralization: Companies pay a high price to have all their data relocated to a central external vendor.
Siloed Rules: Even multiple detection solutions can end up causing more trouble as their inability to integrate creates siloes, additional work, and redundancies.
Poor Rule Management: Without detection engineering (or rule management), you can’t test how well your detections are performing, and you can’t improve them.
Slow Manual Workflows
The process of detection, investigation, containment, and response is never done. That’s why SOCs working manually will never get ahead.
“The problem is we drop people into the middle of all the data and ask them to do work that is mundane,” notes Brian Murphy, CEO of ReliaQuest. “[O]r we ask them to do too many things. We have to use technology to narrow those lanes a bit.”
In other words, the main challenge in threat detection today is keeping up with the rising tide of boring (yet necessary) tasks. The main solution is one that would offload those burdens while still delivering quality results – normalized, prioritized, and in real-time.
For this, security teams need proactive threat detection and response. And they need it in an AI-driven, automated platform.
Enter GreyMatter Detect.
Proactive Threat Detection and Response with GreyMatter Detect
ReliaQuest GreyMatter Detect empowers organizations to proactively detect threats wherever their data resides—at-source, in storage, or across integrated tools—while optimizing costs and enhancing efficiency. By orchestrating detection across SIEMs, data lakes, and other security tools, GreyMatter minimizes storage needs and increases visibility, transforming reactive security operations into proactive threat management.
Case studies, such as Recognize Bank, highlight measurable improvements in detection coverage, showcasing how GreyMatter addresses critical challenges, including siloed data and inefficient processes.
“On average, we’re seeing a 90% reduction in noise...at the same time, we’re increasing your threat detection capability by 250%.” - Colin O’Connor, ReliaQuest Chief Operating Officer


