Editor’s note: This report was authored by Thassanai McCabe.
Key Points
Attackers scaled up trust exploitation, led by “BaoLoader” malware, which abused code-signing certificates instead of relying on novel exploits.
Initial access remained human-driven, with spearphishing links, spearphishing attachments, and drive-by compromise dominating entry points.
Defense evasion techniques remained fragmented, with the command obfuscation sub-technique rising as attackers increasingly weaponized legitimate system utilities.
Meanwhile, ransomware groups continued to exploit patched-but-unremediated internet-facing vulnerabilities; and victims in the professional, scientific, and technical services (PSTS) sector rose by 57%, reinforcing third-party risk as a critical gateway.
Between September 1 and November 30, 2025 (“the reporting period”), “BaoLoader” malware dominated the threat landscape—not by stealing code-signing certificates, but by manufacturing legitimacy at scale. This surge in BaoLoader activity drove all three top initial access techniques during this period: spearphishing links, spearphishing attachments, and drive-by compromise.
Attackers this reporting period leaned heavily on trust exploitation, sidelining zero-day exploits. Malware like “ClickFix” and “Maverick,” ranked second and third in prevalence, followed similar patterns, exploiting human behavior and web-based credential theft. Defense evasion techniques remained fragmented, with command obfuscation emerging as the top sub-technique.
Ransomware victim counts declined for the second consecutive period, though groups like “Qilin” and “Akira” continued to thrive by exploiting known vulnerabilities in internet-facing devices. However, the professional, scientific, and technical services (PSTS) firms bucked the trend, with victim counts jumping 57%. This suggests that trusted partners have been increasingly attractive entry vectors for attackers in recent months. Read on to find out:
How BaoLoader surged by manufacturing legitimacy at scale, blending into normal enterprise activity through code-signing, malvertising, and trusted-tool abuse.
What the three-way tie in defense evasion reveals about attackers' agile methods and how to anticipate their next move.
How ransomware groups are thriving by exploiting your oldest vulnerabilities, not by using zero-days.
BaoLoader Leads a Shift Towards Trust-Based Malware
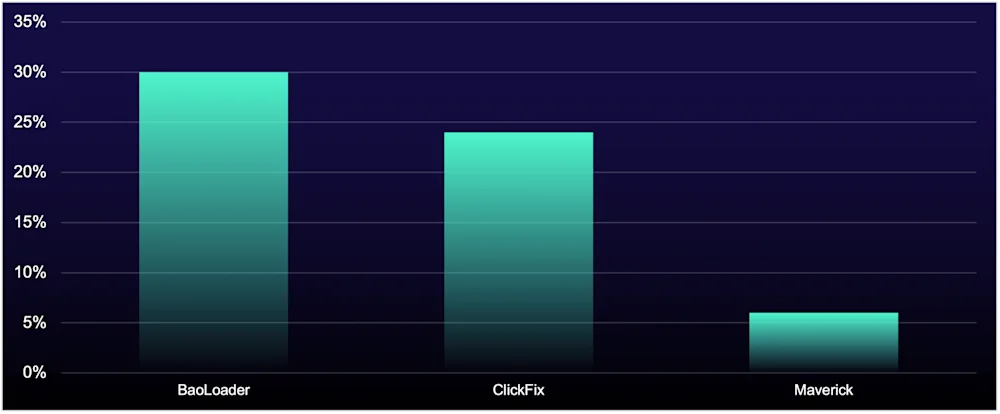
Figure 1: Top malware in true-positive incidents (% of total) during reporting period
Three malware families shaped this reporting period: BaoLoader led incident volume, ClickFix jumped to second place, and Maverick entered the top three for the first time. Meanwhile, last period's top threats—“Oyster/Broomstick” and Akira—dropped out of the top three positions but remain active threats.
The appearance of these three malware families—all using social engineering and exploiting trust—drives the patterns we’ve observed in initial access and defense evasion this reporting period. Organizations face threats that look legitimate at every stage: legitimate-looking ads, legitimate-looking software, and legitimate system utilities performing malicious tasks. This means that the focus of defense must shift from recognizing what is explicitly malicious to identifying what is behaviorally anomalous.
BaoLoader dominated this reporting period by blending into normal enterprise activity—making it particularly dangerous. It commonly abuses node.exe to run malicious JavaScript for reconnaissance, in-memory command execution, and backdoor access. For persistence, it leans on scheduled tasks that appear routine, increasing its chances of surviving standard triage and remediation.
On the network side, BaoLoader often routes command-and-control (C2) traffic through legitimate cloud services, disguising outbound traffic as normal business activity and undermining reputation-based blocking. Post-installation, it chains together fileless, multi-stage execution using built-in tools like PowerShell, often with heavy obfuscation. As such, BaoLoader is able to bypass signature-led controls and “known bad” lists, forcing defenders to rely on behavioral detections, process lineage, and identity-aware monitoring. Its aggressive promotion via malvertising further elevates risk by exposing users searching for productivity tools to infection—turning any employee into a potential entry point.
ClickFix, a deceptive social engineering technique, climbed from third to second place this reporting period due to its unique method of execution. While many social engineering threats like Baloader focus on tricking a user into opening a malicious file, ClickFix innovates by instructing the user to run the malicious code themselves, directly. It coaches them to paste obfuscated commands (typically PowerShell) into legitimate Windows tools like the Run or File Explorer dialogs. This tactic effectively makes the user the execution tool, bypassing preventive controls that are designed to inspect files rather than user-initiated commands. More convincing lures, bolstered by AI-assisted content and embedded videos, likely contributed to its continued rise.
Maverick, a Brazil-targeting banking trojan, specializes in credential theft via browser monitoring, overlay phishing, keylogging, and screenshots. Delivered through social engineering campaigns, Maverick’s effective deception—combined with fileless execution and code similarities to the “Coyote” trojan—makes it a growing concern, especially for financial institutions.
Infostealers Fade in Prevalence, but Vidar Evolves
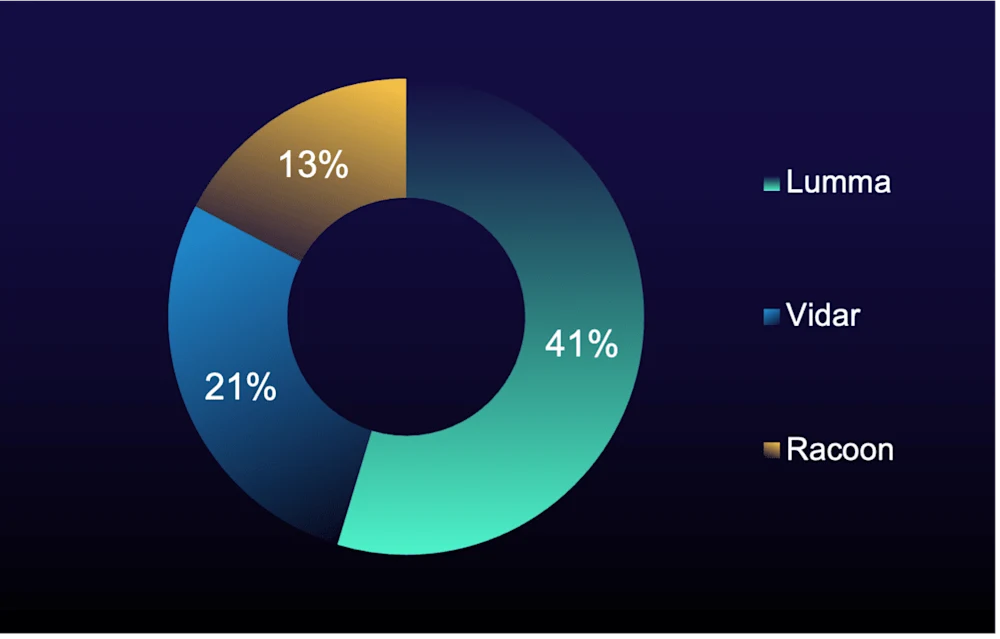
Figure 2: Top malware (% of total) in true positive incidents during reporting period
Overall infostealer activity has been in sharp decline—down 67% last reporting period and another 69% this period following “Lumma” infrastructure takedowns. However, "Vidar 2.0” is driving increased organizational risk by shifting its focus from consumer browser credentials to enterprise cloud credentials and authentication keys often cached on unmanaged or personal devices.
This evolution changes how attackers gain entry into corporate environments. Compromised credentials from home or Bring Your Own Vulnerable Driver (BYOD) systems can provide direct access to production cloud infrastructure, effectively bypassing traditional endpoint-based security controls since the initial compromise occurs outside the managed estate.
Lower infostealer volume doesn’t equal lower enterprise risk. Vidar 2.0’s focus on enterprise targets reinforces the need to extend identity and cloud access controls beyond managed endpoints. This shift has immediate implications for BYOD strategies, conditional access policies, identity governance, and third-party access oversight. Organizations must treat this as an identity-first challenge and assume that credentials can be stolen from unmanaged devices and design access controls accordingly.
Step Up Your Defenses
Your Action Plan
Control Software Installation Through Approved Channels: BaoLoader typically masquerades as PDF editors and productivity tools. Prevent users from downloading and installing software directly from emails or web searches. Instead, provide approved applications through a company-controlled software portal or app store to eliminate the risk of employees unknowingly executing malware disguised as legitimate software.
Monitor Node.js and Legitimate Process Abuse: Implement detections for Node.js processes executing JavaScript files from non-standard directories (e.g., AppData\Local\Temp and AppData\Local\Programs). Establish baseline behavior for legitimate administrative utilities like msiexec and regsvr32. Focus on identifying obfuscated PowerShell and JavaScript chains that weaponize these trusted system binaries.
Combat Social Engineering at the User Level: Provide user awareness training that highlights the risks associated with software download and urgency-based social engineering tactics used by BaoLoader and ClickFix. Establish clear procedures for employees to verify software requests before execution, particularly for attachments mimicking legitimate productivity tools.
Treat Personal Devices as Untrusted: With Vidar 2.0 targeting enterprise cloud credentials, enforce strict authentication controls for BYOD and remote devices. Implement conditional access policies that require phishing-resistant multifactor authentication (MFA) for corporate resources accessed from unmanaged personal endpoints. Monitor for suspicious authentication patterns from personal devices, where infostealers typically operate.
Top Tactics Targeting Enterprise Environment
This section dives into select MITRE tactics and techniques, shedding light on the latest trends in attacker methods and the forces driving their adoption.
ClickFix, BaoLoader, and Maverick: The Human Element as Ground Zero
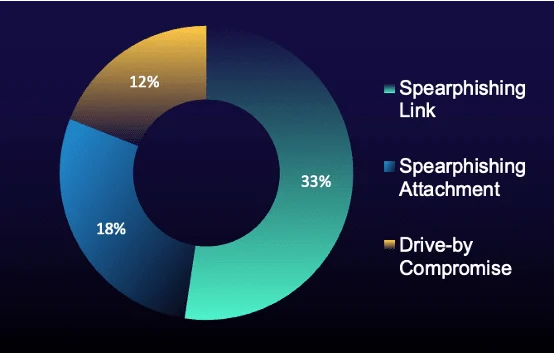
Figure 3: Top MITRE ATT&CK initial access techniques in true-positive incidents (% of total) during reporting period
Spearphishing and drive-by compromise continued to jostle for top spot this reporting period. Although these techniques regularly compete for the lead, their persistence shows the need for defenders to concentrate their efforts on combatting them.
Replication through removable media, which ranked third last period, dropped out of the top three—a sign that its prior spike was an anomaly, not the start of a new trend.
Both spearphishing links and drive-by compromise share a common denominator: They exploit human behavior and trust. Rather than requiring sophisticated zero-day exploits, attackers use psychology—curiosity about a link, trust in a familiar website, or the lure of free productivity tools.
AI-assisted content generation can amplify these attacks, allowing threat actors to create more convincing lures and scale campaigns more efficiently. To counter this, organizations must address the human element through defense-in-depth strategies that combine technical controls with robust security awareness programs.
How BaoLoader Turns Legitimate Certificates into Attack Vectors
Attackers don't need zero-days when they can manufacture trust itself. BaoLoader proves that relying solely on certificate trust or reputation is no longer enough. When attackers can legitimately purchase the keys to the kingdom, organizations need detections that go beyond credentials and focus on behavior.
Operating quietly for years by systematically abusing the code-signing trust model, BaoLoader activity surged dramatically this period—and for good reason. This modular loader malware exploits all three of the most prevalent initial access techniques observed, suggesting its operators have either scaled their infrastructure or shifted to more aggressive tactics.
Weaponizing Legitimacy: Unlike typical malware that steals or forges certificates, BaoLoader's operators took a more audacious approach: They registered legitimate businesses in Panama and Malaysia specifically to purchase valid code-signing certificates from major certificate authorities. Over seven years, they've obtained at least 26 certificates, consistently rebranding their malicious software under innocuous names like "AppSuite-PDF," "PDF Editor," "ManualFinder," and "OneStart." With these certificates, their malware appears trustworthy to both users and security tools, allowing them to operate largely undetected while being dismissed as merely potentially unwanted programs (PUPs). BaoLoader is distributed through multiple vectors—including malvertising, spearphishing attachments, and compromised websites—making it particularly challenging for defenders to track and block.
The Surge: When public disclosure led certificate authorities to revoke compromised certificates, BaoLoader operators adapted quickly. Evidence suggests they registered new companies and obtained fresh certificates from multiple issuers to keep their campaigns running.
What Does a Three-Way Evasion Tie Mean for Defenders?
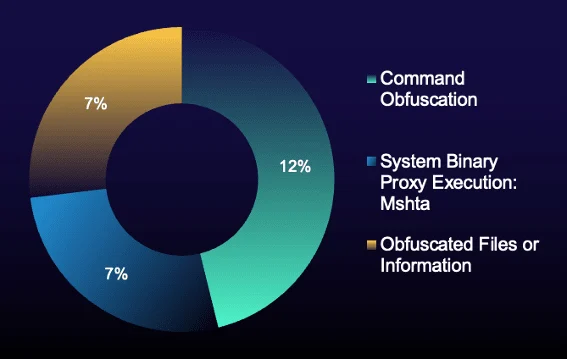
Figure 4: Top MITRE ATT&CK defense evasion techniques in true-positive incidents (% of total) during reporting period
Defense evasion techniques showed volatility this reporting period compared to initial access methods. No single technique dominates; instead, a three-way split persists, similar to the previous reporting period. This signals that attackers are probing multiple weak points—ready with alternatives if one gap closes—and exploiting these gaps at speed.
While the distribution at the top remains fragmented—reflecting last period's 11%, 8%, 7% split—the techniques have shifted, with Rundll32 dropping from first place and command obfuscation rising to the top.
The prevalence of command obfuscation and obfuscated files this period directly correlates with BaoLoader activity. BaoLoader uses heavily encoded JavaScript and PowerShell chains that weaponize legitimate utilities like msiexec and regsvr32. Because these tools handle routine administrative tasks, they're inherently trusted by security systems, which makes abuse harder to detect without behavioral monitoring.
ClickFix malware also contributes to the prominence of the command obfuscation and system binary proxy execution via Mshta sub-techniques through its distinct approach: It mimics legitimate troubleshooting tools to trick users into executing malicious .hta files disguised as system fixes. Once executed, these .hta files use Mshta (a legitimate Windows utility for running HTML applications) to execute obfuscated commands that deploy infostealers, remote-access trojans (RATs), and ransomware.
Both BaoLoader and ClickFix highlight why system binary proxy execution remains attractive. Attackers abuse tools essential to daily operations, making it impractical to block them entirely. Instead, defenders must focus on detecting anomalous behavior in legitimate processes to best neutralize these threats.
RDP's Decline Doesn't Reduce Its Risk
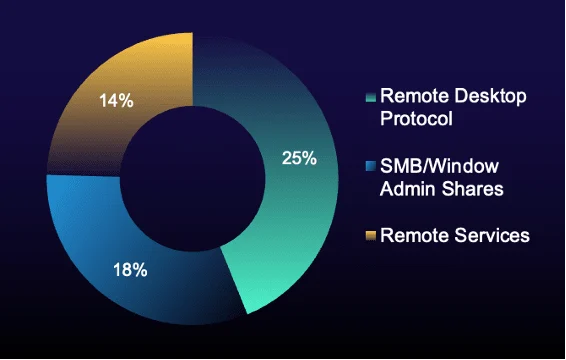
Figure 5: Top MITRE ATT&CK lateral movement techniques in true-positive incidents (% of total) during reporting period
While RDP retained its position as the top lateral movement technique this reporting period, its prevalence dropped by more than half—from 54% to 25%. A similar decline was also observed in SMB/Windows Admin Shares usage.
RDP remains attractive because it's everywhere in enterprise environments and provides authenticated, legitimate-looking access once credentials are compromised. This reporting period’s top malware directly feed this technique: BaoLoader and Maverick both target credential theft, while ClickFix tricks users into exposing authentication details or installing remote-access tools. Once attackers authenticate via RDP, they can escalate privileges, disable security tools, and move toward high-value targets like domain controllers—often within minutes.
As long as remote access remains essential for business operations, attackers will continue to exploit it—particularly when credentials are readily available through malware like BaoLoader, Maverick, and ClickFix. To counter this, organizations must prioritize credential protection and anomalous authentication monitoring, not just focus on endpoint security.
Step Up Your Defenses
How ReliaQuest Helps You Stay Ahead
GreyMatter addresses the speed at which trusted utilities are weaponized, commands are obfuscated, and RDP is exploited. By using agentic AI, it detects anomalies as they occur. Combined with Automated Respond Playbooks, GreyMatter enables rapid containment and remediation, empowering defenders to respond to trust-based attacks, including ad fraud, credential theft, and ransomware deployment, before they escalate.
Your Action Plan
Prioritize Phishing Defense: Implement robust email filtering, URL analysis, and user training to minimize click-throughs on malicious links. Equip users with tools to verify URLs and report suspicious messages.
Hunt for Command Obfuscation Techniques: Attackers are heavily encoding PowerShell and JavaScript to bypass detection. Monitor for Base64-encoded scripts, unusual character patterns in command-line arguments, and legitimate utilities like msiexec and regsvr32 being weaponized through obfuscated chains.
Audit and Enforce Endpoint Security: Ensure endpoint controls (e.g., EDR tools) are actively monitoring for unauthorized IT tools, lateral movement activity, and obfuscated scripts. Early detection of evasion techniques like Mshta and SMBexec is critical to preventing deeper compromise.
Ransomware Groups Thrive on Patch Delays, Not Zero-Day
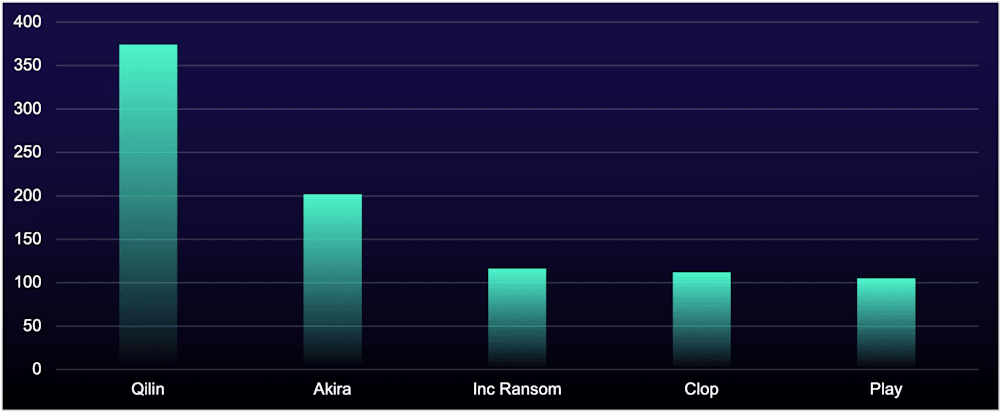
Figure 6: Number of organizations listed on ransomware data-leak sites, by site, during reporting period
Ransomware victim counts on data-leak sites have declined for the second consecutive period. However, established groups like Qilin, Akira, and “Inc Ransom” continue to successfully target organizations through well-documented vulnerabilities in internet-facing devices—not sophisticated zero-days, but preventable security gaps.
The pattern is remarkably consistent: known CVEs, patches available within days, yet mass exploitation occurring months later. Qilin exploited firewall vulnerabilities CVE-2024-21762 and CVE-2024-55591 throughout the reporting period, with activity surging to 188 victims in October alone. Patches were available since early 2025, yet tens of thousands of internet-facing devices remained vulnerable—fueling Qilin's dominance as this period's top ransomware threat.
Akira followed the same playbook with the VPN/firewall vulnerability CVE-2024-40766. Despite patches being available since August 2024, organizations delayed deployment, allowing Akira to chain the vulnerability with credential abuse for rapid ransomware deployment. This persistent exploitation drove a major surge from July through August 2025 into this reporting period, prompting a CISA and FBI joint advisory update on November 13, 2025.
The decline in overall victim numbers may reflect improved defenses in some organizations, but these cases prove that many environments remain vulnerable. These groups aren't developing novel techniques—they're simply outlasting quarterly patch cycles on edge devices. Organizations must treat internet-facing infrastructure as critical assets requiring emergency patching protocols, not routine maintenance schedules, to eliminate these preventable attack vectors.
The Affiliate Model and AI Continue to Reshape the Landscape
Despite the decline in victim numbers, ransomware-as-a-service (RaaS) operations are evolving to keep affiliates active. Groups now integrate AI-driven negotiation chatbots that handle victim communication 24/7, mobile management panels for campaign oversight, and competitive profit splits (70–85%). This automation lowers the technical expertise and time commitment required, allowing less sophisticated affiliates to manage multiple campaigns simultaneously. These innovations help explain why ransomware remains persistent, even as defenses improve.
The data shows fewer victims overall, yet groups like Qilin posted record numbers and ransomware pressure remains unrelenting. This persistence is driven by evolution in the ransomware-as-a-service business model itself. Groups now integrate AI-driven negotiation chatbots handling victim communication 24/7, mobile management panels for campaign oversight, and competitive profit splits of 70–85%. This automation reduces the technical expertise and time commitment required, allowing less sophisticated affiliates to manage multiple campaigns simultaneously. Ransomware remains persistent not only because attacks are more sophisticated, but because the business model is becoming more efficient and accessible.
Sector Targeting Largely Unchanged
While overall ransomware victim counts dropped this period, the top five targeted sectors remained unchanged: PSTS, manufacturing, health care, technology, and construction. Notably, victims in the PSTS sector have increased by 57%, even though total ransomware activity on the sector has dropped.
PSTS firms—such as law, accounting, and consulting—are attractive targets because they manage sensitive data for multiple clients yet often lack enterprise-grade security. A single breach can expose dozens of client environments, making these firms high-value gateways into corporate networks.
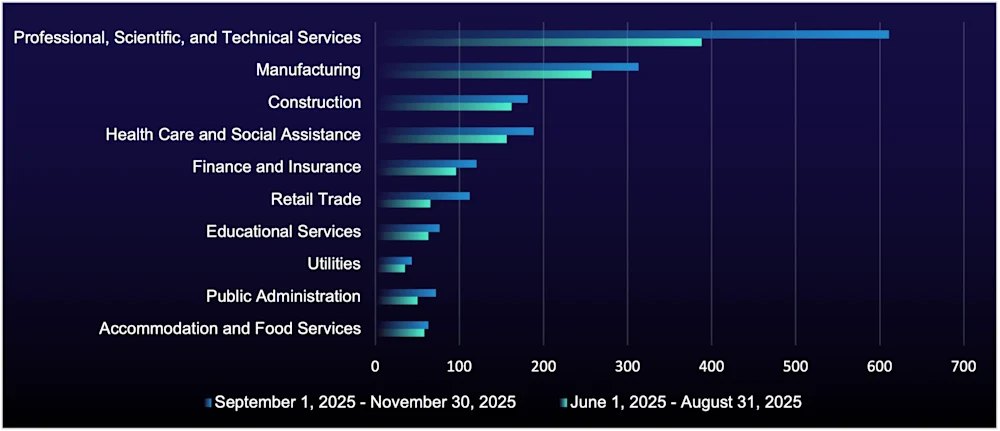
Figure 7: Organizations listed on ransomware data-leak sites, by sector, during this reporting period vs. the last reporting period
Step Up Your Defenses
How ReliaQuest Helps You Stay Ahead
GreyMatter Discover identifies exposed vulnerabilities and misconfigurations in real time, helping organizations proactively reduce their attack surface. Its agentic AI detects lateral movement and anomalous activity, flagging ransomware attempts early in the kill chain. Combined with Automated Response Playbooks, GreyMatter facilitates rapid containment and remediation, preventing attackers from exploiting unpatched systems or scaling their operations.
Your Action Plan
Prioritize Third-Party Risk Management: PSTS organizations are the highest-risk ransomware entry points. Conduct rigorous security assessments for these providers, applying the same standards used for internal systems. Require evidence of endpoint protection, network segmentation, and incident response capabilities. Establish contractual obligations for breach notification timelines and security control verification.
Patch Internet-Facing Devices Immediately: Unpatched VPNs, firewalls, and remote-access solutions remain the most exploited initial access method. Prioritize patching these appliances, and if patching isn't immediately possible, isolate vulnerable systems or implement compensating network controls until remediation is complete.
Test Backup Recovery During High-Pressure Periods: Ransomware groups often time their attacks to coincide with critical operational cycles—holiday seasons, fiscal year-ends, tax periods. Validate that backup systems and recovery procedures perform effectively under pressure. Schedule tabletop exercises during slower periods to ensure teams can restore operations when downtime costs are highest.
Key Takeaways and What’s Next
This report highlights how established attack techniques remain effective through evolving execution.
Initial Access Consistency: Spearphishing, drive-by compromise, and RDP continue as dominant initial access and lateral movement techniques, while ransomware groups successfully exploit known vulnerabilities. However, the malware and tactics using these techniques—led by BaoLoader, ClickFix, and Maverick—have shifted, favoring trust exploitation and social engineering over technical sophistication.
Continued Malware Volatility: This period's top malware families—BaoLoader, ClickFix, and Maverick—differ significantly from last period's leaders (Oyster/Broomstick and Akira). While core techniques remain stable, the specific malware exploiting them changes rapidly, which will likely persist in 2026. Organizations must focus detection on behavioral patterns such as obfuscated commands, legitimate process abuse, and credential theft rather than relying on malware signatures that quickly become outdated.
Defense Evasion Rotation: Defense evasion techniques show higher volatility than initial access methods. Command obfuscation led this period, replacing Rundll32 from last quarter, yet the fragmented distribution remains consistent. Attackers probe multiple evasion methods simultaneously; therefore, top-ranking techniques are likely to vary between reporting periods. Defenders shouldn't over-rotate on this reporting period’s top techniques but should instead prioritize building capabilities to detect the entire range of evasion tactics, including obfuscation, system binary proxy execution, and Dynamic Link Library (DLL) manipulation.






