Author name: Gautham Ashok
Key Points
The average breakout time for the last three months was 18 minutes, with one attack clocking in at just six minutes.
Drive-by compromises accounted for 34% of initial access techniques this reporting period, driven by an ongoing “Oyster” (aka Broomstick) malware campaign. Oyster appeared as the top malware threat.
Server Message Block (SMB) abuse for lateral movement spiked to 29% of incidents, with ransomware operators like “Akira” increasingly using SMB for remote encryption operations to bypass endpoint protections.
Incidents involving unauthorized keyboard, video, and mouse over IP (IP-KVM) devices grew by 328%. These attacks circumvent endpoint protections and significantly limit visibility.
GLOBAL ransomware’s AI-powered negotiation tools and Oyster’s SEO poisoning campaigns show how AI and automation allow threat actors to scale and refine their operations with greater efficiency, necessitating equally rapid responses.
Many successful attacks exploit overlooked vulnerabilities and poor security hygiene, not advanced techniques.
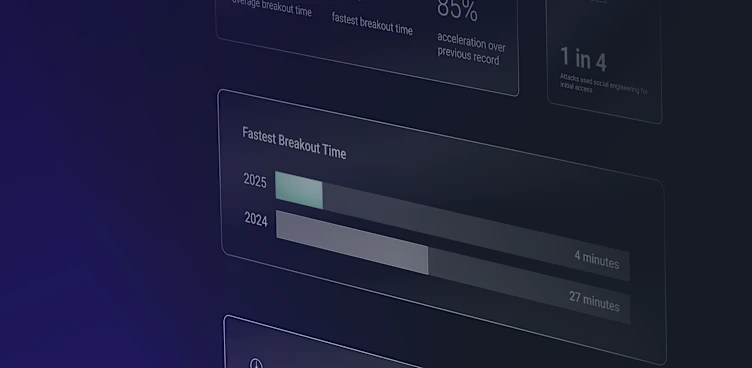
Attackers are continually getting faster: The average breakout time—the period from initial access to lateral movement—dropped to 18 minutes this reporting period (June 1 to August 31, 2025).
And the numbers just keep getting lower. In 2024, the single lowest breakout time we recorded was 27 minutes. In one incident this reporting period, “Akira” ransomware operators initiated lateral movement within just six minutes of compromising a SonicWall VPN, demonstrating just how fast threat actors can move.
The clock is ticking for defenders to close detection gaps and fully leverage automation, as attackers exploit every second. Staying ahead demands a proactive, adaptive approach to security.
This report highlights how attackers are refining their tactics to exploit weaknesses in corporate defenses. We cover “Oyster” malware’s use of search engine optimization (SEO) poisoning, the surge in keyboard, video, and mouse over IP (IP-KVM) device abuse, and the shift toward Server Message Block (SMB)-based ransomware encryption. Read on to find out:
How threat actors are escalating their speed and precision, forcing defenders to act faster than ever to contain and respond to threats.
How attackers are adopting innovative methods to bypass traditional defenses, pushing organizations to rethink their security strategies.
How adversaries use AI and automation to supercharge attacks, shortening reaction time even further.
This report arms CISOs with the critical intelligence and actionable strategies needed to outpace attackers, dismantle evolving threats, and fortify defenses against today’s fastest moving and most sophisticated adversaries.
Top Tactics Targeting Enterprise Environments
This section dives into select MITRE tactics and techniques, revealing the latest trends in attacker methods and the driving forces behind their popularity.

Figure 1: Top MITRE ATT&CK initial access techniques in true-positive incidents (% of total) during reporting period
While drive-by compromise remains the dominant initial access tactic, USB-based attacks are surging, with incidents linked to “Gamarue” malware on the rise.
In this reporting period, drive-by compromise appeared in 34% of incidents—a slight dip from 41% in the previous three months.
Despite this decrease, attackers are doubling down, conducting an ongoing campaign involving Oyster malware (aka Broomstick; see below). Using malvertising and SEO poisoning, Oyster lures victims into downloading trojanized tools.
USB-based malware is thriving because of weak policy enforcement and inconsistent endpoint controls. It’s easy to overlook the dangers of plugging in unvetted USBs, and attackers exploit this to infiltrate corporate networks.
USBs and Gamarue: A Case Study in Clever Tactics, Automation, and Necessity
Invisible to the Average User: Gamarue hides its malicious Dynamic Link Libraries (DLLs) so well that most employees wouldn’t know they’re infected. The infection trigger—a malicious LNK file—disguises itself as a legitimate file already present on the USB, making it even harder to spot.
Doesn’t Need Your Permission: Without USB autorun disabled, Gamarue auto-executes the moment it’s plugged in, requiring zero user interaction. This automation allows for quick, stealthy propagation.
Unavoidable in High-Security Settings: In industries requiring air-gapped networks or limited internet access, USBs are essential for transferring data. Attackers exploit this, turning portable drives into reliable entry points.
The continued success of USB-based malware like Gamarue exposes a critical weakness in enterprise security strategies. Attackers exploit the implicit trust placed in USB devices, using automation and stealth to bypass defenses and establish footholds.
But it’s not just about technology—employee awareness is key. Training simulations demonstrate the risks of unvetted USBs, helping employees understand how a single mistake could lead to a network-wide compromise. USB security policies are non-negotiable, ensure enterprise-wide buy-in to close this critical gap.
Rundll32 Powers 11% of Defense Evasion Tactics

Figure 2: Top MITRE ATT&CK defense evasion techniques in true-positive incidents (% of total) during reporting period
Two of the most impactful malware campaigns right now—Gamarue andOyster—are weaponizing the legitimate Rundll32 tool to evade detection and maintain persistence.
Rundll32.exe, a trusted Windows system binary, has become a favorite for attackers. This reporting period, system binary proxy execution via Rundll32 shot up dramatically, after failing to even make the top 15 defense evasion tactics during the last reporting period.
Gamarue uses Rundll32 to execute malicious DLLs hidden on USB devices, bypassing file-based detection and stealthily spreading across networks.
The Oyster campaign takes this tactic a step further, using Rundll32 to execute DLLs like “twain_96.dll” via scheduled tasks that mimic legitimate activity. This tactic evades security controls and disguises malicious files to resemble trusted system files.
Oyster alone is linked to 48% of incidents involving the "Match Legitimate Name or Location" sub-technique, making its payloads harder to spot and mitigate.
RDP Holds Its Ground While SMB Encryption Tactics More Than Double

Figure 3: Top MITRE ATT&CK lateral movement techniques in true-positive incidents (% of total) during reporting period
RDP remains the go-to tool for attackers, accounting for more than half of lateral movement activity this reporting period. However, the sharp rise of SMB-based ransomware operations—from 10% to 29%—is the trend to watch.
Originally designed to provide IT teams with remote access, RDP has become a favorite for threat actors due to its widespread use and inherent vulnerabilities. Attackers exploit RDP in multiple ways: through social engineering campaigns tricking users into installing malicious RDP tools or by directly targeting exposed RDP servers left unsecured on the internet. Once inside, attackers can move quickly to compromise critical systems like Active Directory (AD) servers.
Meanwhile, ransomware groups like Akira are weaponizing SMB, a legitimate protocol used for file sharing across networks, to execute remote file encryption. Using compromised credentials, attackers access shared files on a network via a single compromised host, often through unmanaged devices or VPNs. By encrypting data remotely, they bypass endpoint protections entirely, operating quietly and efficiently within the network. This highlights a critical flaw in endpoint-focused defenses: Attacks don’t stop at the endpoint, and neither should your defenses.
Both RDP and SMB share a dangerous similarity: They exploit trusted tools to infiltrate and disrupt operations. Whether it’s RDP or SMB enabling lateral movement, attackers are using these methods to bypass defenses and maximize impact.
Step Up Your Defenses
Harden USB Device Policies: Disable USB autorun features on all endpoints to prevent malware like Gamarue from auto-executing when devices are connected. Enforce USB controls with device allowlists and endpoint monitoring configured to detect and block unauthorized removable media. This stops attackers from using disguised USB malware to propagate and establish persistence through trusted binaries like rundll32.exe.
Prevent Unauthorized RDP Tools: Enforce Application Control policies to prevent the installation or execution of unauthorized RDP tools like QuickAssist, which attackers often use for lateral movement or remote access. By restricting these tools, organizations can prevent threat actors from impersonating IT help desks or distributing malicious RDP tools to gain unauthorized access to internal systems.
Strengthen RDP and SMB Defenses: Enforce multifactor authentication (MFA) on all RDP sessions and monitor for unusual login patterns or lateral movement activity. Harden SMB file share permissions and block traffic from unmanaged devices to mitigate ransomware operators, like Akira, from using SMB for remote encryption. These measures help to reduce the risk of large-scale data encryption and operational disruptions.
Oyster Sweeps Away the Competition

Figure 4: Top malware in true-positive incidents (% of total) during reporting period
Oyster took the spotlight this reporting period, skyrocketing to 45% of true-positive customer incidents—a massive leap from just 2.17% last reporting period—and taking its place as the top malware threat.
This surge is likely the result of a shift in cybercriminal priorities. Now, IT administrators are in the firing line. Compromising an IT admin is like hitting the jackpot, giving attackers a golden ticket to organizations’ critical systems, sensitive data, and entire infrastructure.
What’s more, AI and automation are supercharging Oyster’s SEO poisoning campaigns, so attackers can easily craft convincing fake pages at scale. What used to be a time-consuming, manual process is now automated. As such, cybercriminals can mimic legitimate tools and lure victims more efficiently, just like we’ve seen in automation-driven phishing campaigns.
In their ongoing campaign, Oyster operators use malvertising to distribute trojanized versions of legitimate IT tools like PuTTY (a popular remote connection tool used by network administrators) via fake websites such as “puttysystems[.]com.” These tools, signed with stolen certificates, deploy a malicious DLL (twain_96.dll) to install the Oyster backdoor. The malware establishes persistence through scheduled tasks and uses trusted binaries like rundll32.exe to evade detection, ensuring long-term access.
Akira Ramps Up Activity
While Oyster dominated, activity linked to Akira—the name of the ransomware group and the malware it deploys—gained momentum, likely driven by the campaign detailed in the previous section.
In the Akira attacks, the threat actors targeted unmanaged systems lacking EDR sensors and exploited policy misconfigurations that allowed encryption routines to succeed despite detection.
In one notable incident, ransomware operators completed encryption operations within 19 minutes of initial login.
This demonstrates the pace at which attackers can escalate from access to impact and aligns with previous ReliaQuest reporting, which found that unmanaged devices were one of the top five critical security control failures that led to security breaches in 2024.
The new reality is that attackers are encrypting data remotely before most defenses can even react. That’s why automation is non-negotiable.
Without it, the average mean time to contain (MTTC) threats sits at a sluggish 11.99 hours. With automated containment efforts, that number drops to a game-changing 4.49 minutes. The faster you act, the less damage attackers can do.
Step Up Your Defenses
Restrict Software Downloads: Attackers often use trojanized IT tools like PuTTY to distribute malware. Block unapproved downloads by preventing IT staff from downloading software directly from webpages. Instead, provide verified software through a secure, company-controlled portal to minimize the risk of malicious payloads entering the environment.
Monitor IT Tools: Ensure active endpoint monitoring of unauthorized IT tools, especially on administrator systems, as malicious versions of IT tools are often signed with stolen certificates.
Track IT Administrator Activity: IT administrator accounts are high-value targets for lateral movement and privilege abuse. Actively track these accounts, with a focus on unauthorized network access attempts, MFA fraud, device changes, and abnormal command executions.
ReliaQuest Investigates: 328% Jump in IP-KVM Device Usage
We observed a 328% spike in incidents involving unauthorized IP-KVM devices this reporting period. These devices, powered by open-source software, give IT professionals a cost-effective solution for remote server access and virtual storage. However, even the most secure systems can be compromised if paired with unauthorized or vulnerable IP-KVM devices.
Industries like health care often rely on IP-KVM devices to securely manage patient data and sensitive medical equipment in real time. These tools allow IT teams to troubleshoot and access servers remotely without disrupting critical operations.
But this convenience comes at a steep price: IP-KVMs operate externally, leaving little software footprint and bypassing traditional detection methods, turning them into a serious defender blind spot.
Who Uses IP-KVMs?
Nation-State Actors: 56.7% of detected cases involved North Korean operatives exploiting IP-KVMs like TinyPilot, as they seamlessly emulate hardware. These devices allow attackers to infiltrate networks where endpoint visibility is limited, such as bring your own device (BYOD) environments.
Outsourcers: Individuals who use IP-KVMs to manage multiple jobs across different companies. This introduces risks as it circumvents corporate controls to boost productivity.
Employees (Accidental Insiders): IP-KVMs are gaining popularity among staff for practical reasons like remote access to corporate machines or bypassing company software restrictions. While not malicious, these actions expand the attack surface and create opportunities for accidental insider threats.
Accidental insider threats are especially concerning. Employees may be unaware that introducing unauthorized devices opens pathways for attackers to gain out-of-band access to sensitive systems. Once these devices are in place, attackers can reboot servers, install backdoors, steal data, or hijack virtual storage—all while remaining undetected by traditional EDR systems.
Case Study
In August 2025, ReliaQuest alerted on an unauthorized JetKVM device connected to a corporate workstation. The device was mounted twice within a short time as a USB virtual media drive by an authenticated user.
The workstation was connected to an external IP address identified as a VPN proxy, which is often used to mask malicious activity and could indicate the system was being misused as part of an attacker’s infrastructure. Connections from the host to a suspicious cloud-hosted domain were also detected.
ReliaQuest GreyMatter identified the device, blocked further activity and provided detailed data on the JetKVM hardware. Using this information, controls were implemented to block this type of KVM device entirely, ensuring similar unauthorized connections are prevented in the future.
Step Up Your Defenses
Enforce Real-Time Hardware Monitoring: Deploy real-time hardware monitoring solutions, such as Armis, to detect and block unauthorized devices like IP-KVMs at the physical layer. These tools identify hardware signatures and connections that traditional EDRs can’t.
Harden Network and Device Visibility: Use network access control (NAC) to identify and block suspicious IP-KVM devices, ensuring all connected hardware is authorized and monitored. This reduces the risk of attackers or unauthorized users exploiting IP-KVMs to gain covert access to sensitive systems.
Implement BYOD Security Policies: In BYOD environments, enforce security protocols, such as endpoint monitoring, device registration, and restricted access to sensitive systems, to risks introduced by personal devices. Unauthorized IP-KVM devices in BYOD setups can bypass traditional security controls, so implement these policies to minimize the attack surface.
Lumma Dominates, Diversification Expands Challenges

Infostealer activity declined by 67% this reporting period, largely due to the law enforcement takedown of “Lumma’s” infrastructure in May 2025. Despite this, Lumma remained the top infostealer, accounting for 54% of incidents.
Lumma’s operators quickly adapted after the takedown by distributing their malware through fake software cracks, serial key generators, and “ClickFix” techniques like fake CAPTCHA pages, leveraging platforms such as GitHub and social media to target unsuspecting users.
We recently analyzed a ClickFix campaign that used fraudulent CAPTCHA prompts to trick users into copying and pasting malicious commands. Although this campaign was attributed to “Luna Moth,” the similarities between its tactics and those commonly used by Lumma suggest it’s plausible that Lumma could adopt similar techniques in the future.
However, the disruption created space for other malware to grab market share. Here’s how the competition is shaping up:
“Acreed”: Focuses on high-value software-as-a-service (SaaS) credentials, which provide attackers with direct access to email, storage, and project management platforms. These accounts often serve as a launchpad for lateral movement within organizations.
“Vidar”: Uses RC4 encryption and unconventional platforms like TikTok to distribute its payloads, allowing it to thrive in less-monitored environments where enterprise-grade visibility is lacking.
“Stealc”: Packs modular capabilities like file extraction, screenshot capture, and geofencing bypass. This makes it a top choice for attackers targeting cloud storage, financial records, and proprietary documents.
The decline in numbers may seem like a win, but as Lumma continues to dominate, emerging players are filling the void with advanced capabilities, forcing defenders to tackle a broader range of tactics and tools.
Step Up Your Defenses
Enhance SaaS and Cloud Environment Protections: Implement access controls for SaaS accounts and cloud platforms, such as enforcing MFA and limiting access to critical accounts. Regularly audit permissions and monitor for anomalous behavior within these environments.
Limit Third-Party Integration Risk: Review and restrict third-party integrations in SaaS environments so only essential services have access to sensitive data. Use token-based authentication with granular permissions to minimize the impact of credential theft. Regularly rotate API keys and enforce expiration policies to reduce exposure.
Implement Geo-Fencing for Malware Communications: Configure network-based geo-fencing to block outbound connections to high-risk regions often associated with command-and-control (C2) servers. Use DNS filtering to prevent infostealers from establishing external communication channels, disrupting their ability to exfiltrate data or download additional payloads.
Qilin Stays Top as Ransomware Environment Slows Down

Figure 6: Number of organizations listed on ransomware data-leak sites, by site, during reporting period
Ransomware activity saw a 4.52% decline in overall victims listed on data-leak sites this reporting period. Akira, “SafePay,” and “Play” experienced slower growth, with victim counts falling by 9.42%, 23.14%, and35.54% respectively.
At first glance, this decline may suggest the threat is cooling—but the numbers reveal a more complex story: Ransomware groups are adapting by splintering into smaller groups, leveraging older vulnerabilities, and turning to AI to accelerate and enhance attacks.
At the top of the ransomware ecosystem, “Qilin” retained its position, driven by a campaign targeting Fortinet FortiGate vulnerabilities (CVE-2024-55591 and CVE-2024-21762). Similarly, Akira exploited SonicWall SSL VPN vulnerabilities (CVE-2024-40766) and used Bring Your Own Vulnerable Driver (BYOVD) attacks to disable security controls. In one incident, Akira operators initiated lateral movement within just six minutes after exploiting a SonicWall VPN, underscoring the speed and precision characterizing today’s attacks.
These two campaigns highlight a troubling reality: attackers are exploiting older vulnerabilities in internet-facing devices to infiltrate networks. This isn’t about sophisticated tactics—it’s about foundational security failures. Unpatched vulnerabilities leave organizations exposed, regardless of how advanced an attacker’s methods are. Vulnerabilities in internet-facing devices, such as VPNs, remain a security control failure repeatedly seen in incidents throughout 2024. Unless these gaps are addressed, attackers will continue to exploit these weaknesses as easy entry points into corporate systems.
The Ransomware Threat Hasn’t Disappeared—It’s Fractured
Smaller, agile groups have filled the vacuum left by disbanded groups like “RansomHub.” Others, like “DragonForce,” lie low for extended periods, quietly recruiting freelancers from collapses groups before launching concerted campaigns.
One group to watch is “GLOBAL” ransomware. While it only listed 30 victims on its data-leak site this reporting period, GLOBAL’s affiliate model offers an attractive 80–85% ransom share. The group’s AI-powered tools, includinga mobile-friendly management panel; an offline payload builder for Windows, Linux, and VMware ESXi; and an AI-powered negotiation chatbot, enable attackers to personalize ransom demands, manipulate victims with precision, and streamline operations. GLOBAL’s aggressive affiliate-driven model and AI capabilities likely position it for significant growth in the short to medium term.
Ultimately, If the numbers show anything, it’s that ransomware is evolving. Attackers are finding smarter, more efficient ways to bypass defenses, leveraging older vulnerabilities and trusted tools to move quickly.

Figure 7: Organizations listed on ransomware data-leak sites, by sector, during this reporting period vs. the last reporting period
Most industries saw a decline in ransomware victim counts, but the health care and social assistance sector experienced a 38% increase, and the utilities sector recorded a staggering 84% surge compared to the previous reporting period. Both sectors present unique technical and operational vulnerabilities that make them attractive targets for ransomware campaigns. Health care organizations depend heavily on interconnected IT systems for patient care, medical records, and diagnostics, making availability critical. The urgency to maintain operations, combined with sensitive patient data governed by strict regulations, creates a strong incentive to pay ransoms.
Similarly, utilities are critical national infrastructure. Attacks on industrial control systems (ICS) can disrupt essential services on a massive scale. Many utilities lack robust cybersecurity measures for operational technology (OT), leaving them vulnerable to ransomware groups that exploit the pressure to restore functionality.
It's realistically possible that ransomware groups like Qilin, which targeted 26 utility companies during this reporting period, increased its focus on the utilities sector during the summer months to capitalize on peak demand. Disruptions during high-demand periods amplify the financial, operational, and reputational pressures on victims, increasing the likelihood of ransom payments.
Step Up Your Defenses
Harden SMB File Share Permissions: Restrict access to SMB file shares by enforcing least privilege policies and ensuring network shares are accessible only to authorized users. Implement monitoring tools to detect unusual SMB activity like remote encryption operations and block traffic from unmanaged devices to mitigate lateral movement threats.
Use Risk-Based Authentication: Adjust access requirements dynamically based on user behavior, device, and location.
Mitigate BYOVD Attacks: Deploy endpoint protection tools that can detect and block vulnerable driver loads and kernel exploit attempts. Regularly audit driver usage across systems and disable outdated or unnecessary drivers to reduce the attack surface for techniques like BYOVD.
Key Takeaways and What’s Next
A few consistent themes have emerged across this report that reveal the shifting and increasingly complex threat landscape. Attackers are exploiting foundational security gaps—like unpatched vulnerabilities in internet-facing devices—and leveraging trusted tools like RDP, SMB, and rundll32.exe to bypass defenses.
The takeaway is clear: Many successful attacks stem not from cutting-edge techniques, but from neglecting well-known vulnerabilities and basic security hygiene.
Automation and AI are emerging as critical enablers, evident in GLOBAL ransomware’s AI-powered negotiation tools and Oyster’s SEO poisoning campaigns. These tools allow attackers to scale and refine their operations with greater efficiency.
Adaptability is another recurring trend, with smaller ransomware groups filling the void left by disbanded major players, infostealer operators like Lumma diversifying their distribution tactics, and attackers continuously evolving their social engineering strategies.
As attackers innovate, organizations must stay vigilant. Three major forecasts highlight what’s next on the threat horizon:
A Pearl in the Ransomware Oyster: This convergence of automation supercharging SEO poisoning attacks, smarter targeting, and trusted binaries like rundll32.exe will position Oyster as a critical gateway for future ransomware activity.
Detection and mitigation must become top priorities for defenders as attackers increasingly adopt AI and automation to scale campaigns and reduce the time between initial access and ransomware deployment. Similar to Akira’s use of SEO poisoning to distribute tools like “DBeaver” and “ManageEngine,” Oyster’s efficiency and adaptability will likely make it a key player in ransomware deployment.
IP-KVM Devices Ripe for Exploitation: Unauthorized IP-KVM devices will remain a significant enabler for attacks in enterprise environments.
Their hardware-level access to systems, reliance on open-source software and ability to bypass EDR solutions create blind spots for defenders. These devices are likely to become increasingly attractive to cybercriminals seeking covert access by evading software-based defenses, lateral movement, persistent access, and privilege escalation.
Lumma Infrastructure Shift to Pay Off: Lumma’s shift to Russia-based hosting services and departure from Cloudflare-based obfuscation has bolstered its resilience against takedowns.
By relying on hosting providers perceived as less likely to cooperate with law enforcement, Lumma’s operators ensure the malware remains available and reliable across criminal marketplaces. This stability will make Lumma an increasingly attractive option for cybercriminals who depend on consistent access to tools for harvesting credentials. For businesses, this means escalating risks as Lumma becomes the infostealer of choice across diverse threat actor groups.