Editor’s note: This report was authored by Hayden Evans
Key Points
“Scattered Spider” announced plans to launch a ransomware-as-a-service (RaaS) offering, while “LockBit” returned with "LockBit 5.0" and announced critical infrastructure as a target.
The number of unique data-leak sites hit an all-time high of 81 in Q3 2025, as smaller ransomware groups have filled the gaps left by larger ones. This fragmentation has led to unpredictable attack patterns, affecting sectors and regions not traditionally targeted.
Organizations worldwide face a growing ransomware threat, as new groups emerge and existing ones adopt more aggressive tactics. To counter these threats, organizations must segment networks, patch public-facing vulnerabilities, and enforce strict access controls for VPNs and RDP.
Ransomware threats reached a tipping point in Q3 2025, driven by major developments across the ecosystem. The hacking collective “Scattered Spider” teased its first ransomware-as-a-service (RaaS) offering, while long-standing ransomware operator “LockBit” announced its intent to target critical infrastructure through its new affiliate program. Meanwhile, a powerful alliance between leading ransomware groups has raised the stakes for organizations worldwide. Adding to the tumult, the number of data-leak sites hit a record high, with emerging groups expanding into new regions and industries.
While the number of organizations listed on data-leak sites for extortion remained steady compared to Q2 2025, this quarter was defined by significant developments reshaping the ransomware ecosystem.
Scattered Spider teases its first RaaS: “ShinySp1d3r RaaS” marks the first major RaaS from English-speaking cybercriminals.
LockBit eyes critical infrastructure: LockBit releases its “LockBit 5.0” affiliate program, allowing affiliates to target sectors typically off-limits under RaaS rules.
New alliances between ransomware giants: “DragonForce,” “Qilin,” and LockBit form a partnership poised to escalate attacks.
Ransomware spreads globally: The number of active data-leak sites hit an all-time high of 81, driving attacks into new regions like Thailand, which saw a 69% surge in listings fueled by the newly emerged “Devman2” group.
The ransomware threat has reached unprecedented levels—with a record number of data-leak sites, major collaborations, and expansion by emerging groups putting organizations across all industries and regions at risk. This report highlights the critical shifts in ransomware every CISO must know.
Q3 Warning Signs: What to Expect from Ransomware in Q4
Scattered Spider Teases First English-Led Ransomware Service
Scattered Spider alluded to the ongoing development of its first RaaS offering, ShinySp1d3r RaaS, which combines its notorious social engineering expertise with disruptive encryption.
In late August 2025, the English-speaking collective shared an image of its ransom note on Telegram (see Figure 1), claiming it will be “the best RaaS to ever live.” ShinySp1d3r RaaS puts organizations at risk of both data theft and encryption by the group. This announcement even signals a ramp in efforts from Q3 2025, when the group collaborated with “ShinyHunters,” a breach-and-leak group, to steal data from Salesforce systems, and Q2 2025, when it targeted retail, insurance, and aviation companies to deploy DragonForce ransomware.
This service has not yet been formally released, but if it is, it will mark a major shift for English-speaking, West-based cybercriminals, who have traditionally relied on Russian-speaking ransomware providers like DragonForce, “ALPHV,” and “RansomHub” that are often hesitant to collaborate with English speakers or demand a deposit as a sign of trust due to operational security concerns.
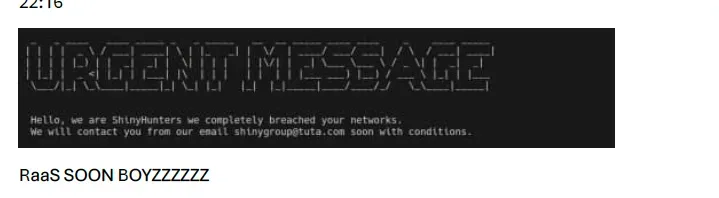
Figure 1: Scattered Spider hints at RaaS development on Telegram
Although several members of the group have been arrestedi, Scattered Spider will continue to operate and develop this service. The group is unstructured and made up of transient members, primarily teenagers who are drawn to cybercrime through online communities and forums.
Step Up Your Defenses Against Scattered Spider
Scattered Spider exploits weak help-desk policies by bypassing identity verification for password and MFA resets. To prevent this, enforce strict verification policies for help-desk staff and test their effectiveness with red team exercises using social engineering tactics.
LockBit Returns: Critical Infrastructure in the Crosshairs
LockBit, one of the most notorious and successful ransomware groups in recent years, marked its return from dormancy on September 3, 2025 by announcing "LockBit 5.0," a new version of its affiliate service, on the dark web forum “RAMP.”
The announcement, timed to coincide with the 6th anniversary of its affiliate program, revealed the group’s intent to target critical infrastructure (see Figure 2)—a notable shift, as ransomware groups typically avoid such targets to evade heightened scrutiny from law enforcement. This caution has been particularly prevalent since the May 2021 Colonial Pipeline attack by the DarkSide group, which led to the seizure of its cryptocurrency and the group’s eventual shutdown.

Figure 2: LockBit announces return and critical infrastructure targeting (translated from Russian)
LockBit 5.0 has introduced expanded targeting capabilities, allowing affiliates to attack sectors traditionally avoided by RaaS programs. This shift puts organizations in previously low-risk industries at heightened risk, with the group listing these sectors as permissible targets unless an agreement is reached with the FBI. This aggressive stance appears to be driven by the group’s leader, potentially as retaliation for prior law enforcement actions (see below).
In early 2024, law enforcement dealt a significant blow to LockBit by seizing infrastructure, arresting members, and issuing a warrant for its leader. If the group manages to rebuild its trust among affiliates, it could reemerge as a dominant ransomware threat, driven by financial motives and by a desire for revenge against law enforcement crackdowns.
Sectors that LockBit affiliates are now permitted to target
“It is permissible to attack critical infrastructure such as nuclear power plants, thermal power plants, hydroelectric power plants, and other similar organizations.*
*These authorizations remain in effect until an agreement is reached between the FBI and LockBit not to attack certain categories of targets. If you are reading this and these rules have not changed, then the FBI has not yet approached us for this agreement and they are quite comfortable with the authorizations to attack the above categories of organizations.”
Step Up Your Defenses Against LockBit
LockBit is eyeing critical infrastructure that commonly involves operational technology (OT) systems. Use the Purdue Model to segment OT systems from the IT network. Create separate security zones for each layer, with strict access controls and firewalls between IT (Levels 4–5) and OT (Levels 0–3). This limits ransomware from spreading between networks and reduces the impact of attacks.
RaaS Giants LockBit, DragonForce, Qilin Unite to Escalate Global Attacks
This quarter, the newly returned LockBit formed a coalition with prominent RaaS groups DragonForce and Qilin (see Figure 3), a partnership poised to drive more frequent and effective ransomware attacks. Announced shortly after LockBit’s return, the collaboration is expected to facilitate the sharing of techniques, resources, and infrastructure, strengthening each group’s operational capabilities. This alliance could help restore LockBit’s reputation among affiliates following last year’s takedown, potentially triggering a surge in attacks on critical infrastructure and expanding the threat to sectors previously considered low risk.
Similar partnerships have proven transformative in the past—such as in 2020, when LockBit joined forces with the Maze ransomware group. That collaboration introduced double extortion tactics, combining system encryption with data theft to heighten pressure on victims, and used Maze’s data-leak site to amplify impact.

Figure 3: DragonForce announces partnership with Qilin and LockBit
The Current Landscape: New Groups and Top Trends
Data-Leak Sites Hit a Record 81 in Q3 2025
The number of active data-leak sites soared to a record-breaking 81 in Q3 2025, leaving almost no sector or country untouched. Ransomware groups’ unique targeting preferences and techniques are making attacks increasingly unpredictable and harder to defend against (see Figure 4).
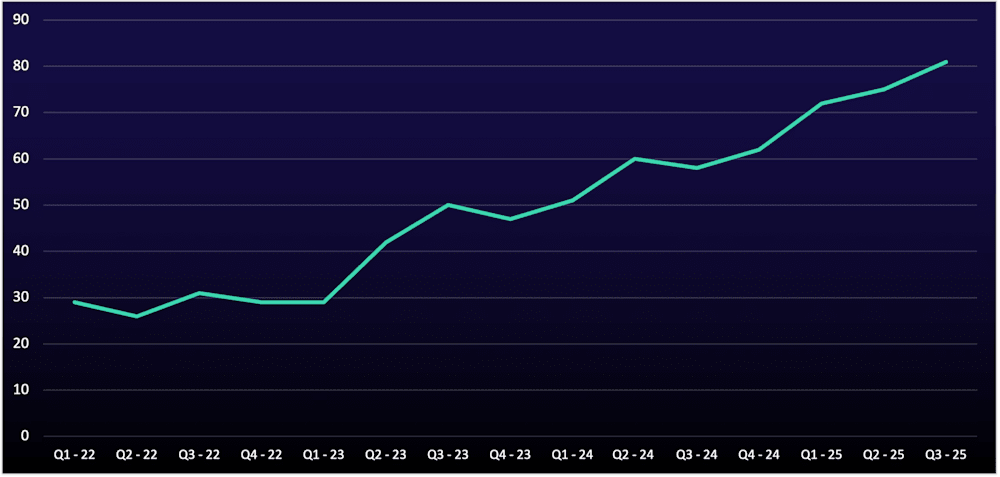
Figure 4: Active data-leak sites from Q1 2022–Q3 2025
The number of active data-leak sites tends to rise and fall with the activity of dominant ransomware groups. After LockBit’s decline in early 2024, sites increased from 51 to 60 as smaller groups filled the gap. A similar trend followed RansomHub’s disappearance in early 2025, with sites rising from 72 to 81.
Unless a dominant group centralizes ransomware affiliates (such as the previously discussed cartel), active data-leak sites will likely continue growing as cybercriminals launch their own operations. It’s also realistically possible that newly formed groups focus on targeting small- and medium-sized businesses (SMBs), which have less funding for security measures, even if the payoff is lower.
Emerging Groups Drive 31% Rise in Health Care Attacks
By Q3 2025, newly emerged groups like “Beast,” “The Gentlemen,” and “Cephalus” fueled a 31% surge in attacks on organizations in the health care sector, surpassing established names like Qilin and Inc Ransom and showcasing that smaller groups, collectively, can be just as destructive as their prominent counterparts. This sharp increase follows the brief relief in Q2 2025, when health care listings dropped due to the absence of the previously dominant group RansomHub.
Meanwhile, the top-targeted sectors in Q3—professional, scientific, and technical services (PSTS), manufacturing, and construction—stayed the same. PSTS saw a 17% increase in listings, while manufacturing and construction dropped by 5% and 19%, respectively. The reasons for these changes aren’t clear but reflect the opportunistic nature of ransomware groups.
These sectors are frequently targeted because they hold sensitive data like intellectual property and financial records, have outdated systems or limited security budgets, and include many smaller businesses with weaker cybersecurity measures, making them easy and profitable targets for attackers. This continued targeting of organizations in the PSTS, manufacturing, and construction sectors will almost certainly remain in the long term (beyond one year).
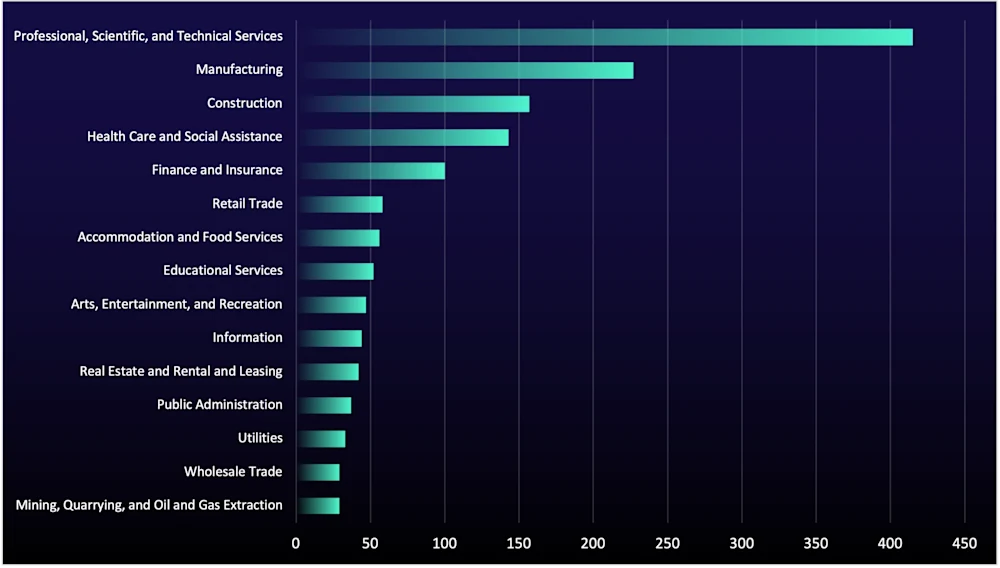
Figure 5: Number of organizations listed on data-leak sites, by sector, in Q3 2025
69% Spike in Attacks Targeted at Thailand
While the US remains the top target for ransomware groups, lesser-known groups that emerged in Q3 have expanded beyond traditional hotspots like the US and Europe to countries such as Egypt, Thailand, and Colombia, likely to evade detection, incident response measures, and law enforcement scrutiny—a trend previously observed in 2021 after US disruptions forced actors to shift away from high-profile targets.ii
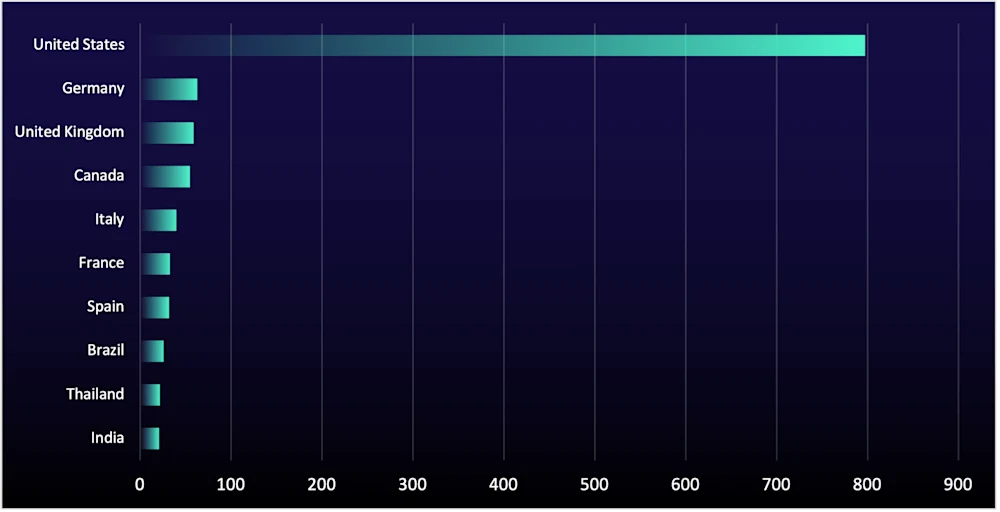
Figure 6: Number of organizations listed on data-leak sites by country, Q3 2025
Thailand saw a record 69% increase in data-leak site appearances from Q2 to Q3 2025, driven by the emergence of “Devman2.” Successor to “Devman,” this group, appearing for the first time this quarter, has already listed over 25% of Thailand's organizations. Historically, Thailand averaged 5 to 10 listings per quarter, but this jumped to 22 in Q3 2025.
Countries like Thailand with rapidly growing digital economies (projected to reach $140.3 billion in 2025) face heightened risksiii as ransomware groups exploit security gaps. Expanding infrastructure and limited cybersecurity measuresiv make these regions attractive targets.
The US, however, remains the top target due to high payouts, a large number of potential victims, and the prevalence of cyber insurance that often covers ransomware paymentsv. Ransomware groups analyze stolen data, including insurance policies, to maximize extortion payments. Meanwhile, lenient enforcement in countries like Russia allows these groups to operate without consequences.
Qilin Holds Top Spot, Sets Record High
RaaS group Qilin reached its highest number of listed organizations in a quarter in Q3 2025, driven by business-like operations and aggressive recruiting efforts, including website banner advertisements on dark web forums (see Figure 7).

Figure 7: Qilin advertisement banner
Qilin’s success shows that ransomware groups succeed by running like businesses, with organized practices, recruiting, and efficient operations. For example, they partner with initial access brokers (IABs) to get VPN access, allowing faster and more coordinated attacks that can bypass EDR detection.
Not far behind are “Akira,” Inc Ransom, and “Play,” who remain major threats due to their reliance on tried-and-true techniques, such as exploiting unpatched vulnerabilities in internet-connected software. These groups demonstrate how basic security gaps—like unmanaged or unknown assets—can provide attackers with quick access to networks, enabling them to move laterally in as little as six minutes while evading detection as seen in Akira’s recent campaign of targeting SonicWall devices.
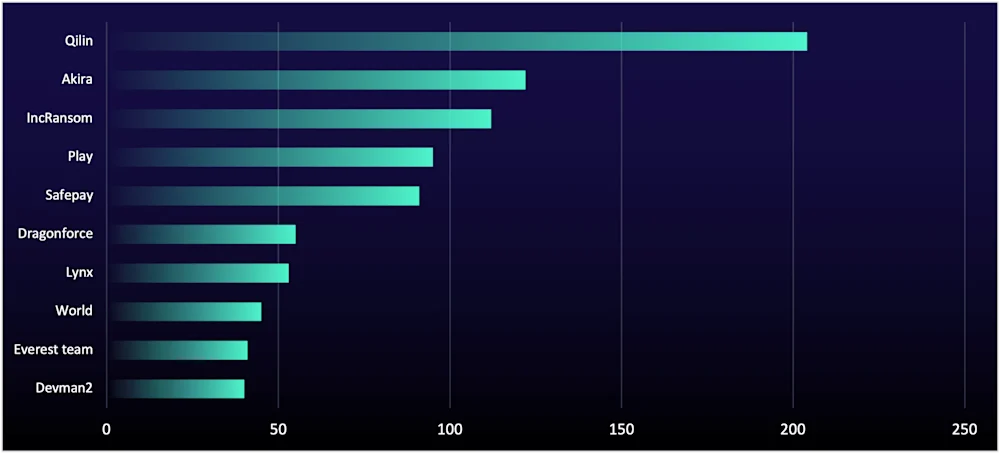
Figure 8: Number of data-leak site posts by group, Q3 2025
Group To Watch
Name: The Gentlemen
Type: RaaS Group
Emergence: September 2025
Victimology: The group has targeted sectors like health care, construction, and manufacturing across multiple countries, focusing on the US but also hitting Mexico, Colombia, Thailand, and other less commonly targeted countries compared to leading RaaS groups.
Highlight: Appearing at the end of Q3 2025, The Gentlemen has already listed 35 organizations on its data-leak site. With an enticing 90/10 profit split for affiliates, the group will almost certainly continue to gain traction.
Step Up Your Defenses Against Ransomware
ReliaQuest’s Approach
Counter the threat of ransomware with ReliaQuest GreyMatter, the agentic AI security operations platform that empowers organizations to detect, investigate, and respond to threats faster by automating routine tasks. Features like GreyMatter Workflows enable custom automation, while GreyMatter Transit detects threats as data moves between its source and storage. Using our detection rules alongside GreyMatter Automated Response Playbooks, organizations can perform remediation without manual interference to contain threats in as little as five minutes. To safeguard against ransomware, integrate these Playbooks:
Block Hash: Counter the deployment of ransomware or malicious tools by blocking file hashes before execution
Isolate Host: Infected hosts can provide initial access to RaaS affiliates, restrict their access to critical resources by isolating the host before damage can be done.
Disable User: RaaS affiliates are increasingly gaining access by simply authenticating to RDP or VPNs, revoke their access by disabling compromised accounts.
Your Action Plan
This report reveals that ransomware remains one of the most critical threats to organizations worldwide, and it outlines three crucial steps they should take now to strengthen their defenses against these attacks.
Restrict RDP and Remote Access: Use device-based certificates to block attackers using stolen VPN credentials from IABs. Limit RDP access to essential accounts and hosts, enforce network segmentation to restrict access to authorized sources, and ensure users fully log out of sessions when not in use. Ransomware affiliates often gain access through exposed RDP and VPN portals, making stronger authentication measures critical to preventing intrusions.
File Containment Restrictions: Encryption by ransomware groups such as Akira are increasingly performed remotely over SMB. Implement file containment protection in EDRs to identify and block remote attacks.
Patch Public Applications: Prioritize fixing vulnerabilities in public-facing software like VPNs to prevent ransomware groups from exploiting them. If patching isn’t immediately possible, create a fallback plan to remove the vulnerable device from the public internet and implement temporary solutions.
Key Takeaways
As we reflect on Q3 2025, the ransomware landscape has undergone a dramatic transformation. With the fall of once-dominant groups like RansomHub, smaller, fragmented ransomware actors have surged, introducing unique and unpredictable targeting patterns. Meanwhile, top ransomware groups continue to operate at lightning speed, exploiting critical vulnerabilities to seize valuable organizational data.
Looking ahead to the rest of 2025 and beyond, ransomware is gaining unprecedented interest among English-speaking cybercriminals, fueled by Scattered Spider’s teased development of a major RaaS service. Meanwhile, LockBit is breaking new ground by authorizing attacks on sectors previously considered off-limits in retaliation against law enforcement actions. Its coalition with leading ransomware groups highlights the growing sophistication and escalating danger ransomware poses to organizations worldwide. The threat landscape is shifting rapidly, and ransomware is set to become an even greater challenge for defenders.


