Editor’s note: This report was authored by John Dilgen.
Key Points
Ransomware platforms built on automation, customization, and advanced tooling likely attract the most skilled affiliates and appear to create the most successful ransomware-as-a-service (RaaS) groups, judging from data-leak site victim counts.
Automation is the most adopted and effective factor: 80% of the RaaS groups we analyzed have some automation and AI in their platforms. The speed of attacks has dramatically increased—average breakout time is now just 18 minutes—and defenders have significantly less time to react.
Based on these factors, we hypothesize that emerging ransomware groups “The Gentlemen” and “DragonForce” are likely poised for success by offering the advanced features that market leaders like “Qilin” advertise.
Organizations should focus on countering the common tactics that drive ransomware groups’ success, such as fighting automation with automated responses and using network segmentation to limit the impact of customized attacks.
In the competitive ransomware-as-a-service (RaaS) ecosystem, a group’s success—defined here as victim count on its data-leak sitei—depends on the sophistication of its platform and its unique offerings. Such bespoke platforms attract the most skilled affiliates, who can often bypass stronger defenses to compromise higher-revenue organizations, increasing the likelihood of a successful extortion payment.
To understand what makes a RaaS group successful, ReliaQuest identified a three-factor model built on workflow automation, advanced tooling, and attack customization. Our research, based on an analysis of RaaS recruitment posts on the dark web, indicates that platforms offering these capabilities tend to attract elite affiliates and execute more effective attacks. We tested this theory against the market's current leaders and used it to hypothesize the next wave of major players, finding that emerging groups “The Gentlemen” and “DragonForce” are likely to become significant threats.
By breaking down the likely success formula for dominant ransomware groups, this report delivers the critical intelligence and actionable defenses organizations need to counter their evolving tactics, including:
A breakdown of the RaaS success model, detailing how automation, customization, and advanced tools are reshaping the threat landscape.
Profiles of the RaaS A-list, analyzing why groups like “Qilin” seem to succeed while others like “Medusa” appear to falter.
An inside look at the "ones to watch," explaining the capabilities of emerging threats like “The Gentlemen” and “DragonForce.”
An actionable plan to counter these advanced tactics with defensive automation, network segmentation, and layered security.
The RaaS Recipe for Success
What separates a dominant ransomware group from a dozen aspirers? Our research into RaaS recruitment posts from currently active groups on the Russian-language cybercriminal forum “RAMP” points to a recipe for success, built on three key ingredients: workflow automation, tailored attack customization, and advanced tooling. Let’s breaks down what these capabilities are and why they give top-tier RaaS groups a decisive edge.
The Need for Speed: Automation Likely Fueling a Faster Attack Chain
Automation is almost certainly increasing the speed of ransomware attacks, with 80% of the RaaS groups we analyzed now offering automation or AI within their platform. According to RaaS advertising forum posts, these capabilities include automatic EDR and antivirus detection, alongside features to automatically kill software that prevents ransomware execution. This focus on speed is reflected in the average breakout time—the time it takes an attacker to move to additional hosts after initial access—dropping from 48 minutes in 2024 to just 18 minutes between June and August 2025.
Automation, and the speed it offers, ultimately makes attacks more likely to succeed: Attackers can quickly compromise more endpoints, giving defenders less time to alert, analyze, and contain before ransomware deployment. This shrinking window is especially dangerous, given our customer data indicates that the mean time to contain (MTTC) attacks for security teams relying solely on manual strategies is eight hours. This delay could lead to significant data theft and business downtime and highlights the need for defensive automations that keep pace with attackers.
Attackers’ Choice: How Customization Shapes the Attack
Customization, now offered by 60% of the RaaS groups we analyzed, drives success by allowing affiliates to dynamically change how the ransomware operates during an attack.
A common option is the ability to prioritize the strength or speed of encryption. Stronger encryption makes it harder for organizations to restore data without paying the ransom, but faster encryption can affect more files within the environment before defenders can contain the threat, greatly complicating and extending the recovery process. This flexibility could provide a key strategic advantage, allowing affiliates to tailor their attack for maximum impact—whether prioritizing unbreakable encryption for a high-value system or rapid, widespread impact across a large network—to best compel an extortion payment.
An Arsenal of Advantage: The Role of Advanced Tooling
The most successful RaaS groups—those with the most victims listed on their data-leak sites—also offer their affiliates access to advanced tools and features, but only 50% of the groups we looked at currently provide these capabilities.
As such, fewer than half of the RaaS groups analyzed can provide the complete trifecta of capabilities needed to attract the elite talent that is most likely to compromise heavily defended organizations and secure large extortion payments. For example, top-tier groups typically offer scripts that can bypass and disable EDR and antivirus tools on a compromised endpoint, as well as tools for deleting an organization’s backups during ransomware deployment. Bypassing common defense tools helps prevent containment and detection efforts, ensuring more endpoints can be encrypted. Meanwhile, deleting backups prevents an organization from restoring its systems, increasing the likelihood of an extortion payment.
Profiles in Profitability: The RaaS A-List
Qilin exemplifies the RaaS recipe for success, rising to become the most dominant ransomware group in the second and third quarters of 2025 (in terms of data-leak site victim count). This success is highly likely driven by its platform offering the market's strongest combination of automation, customization, and advanced features. By providing such a powerful toolkit, Qilin likely attracts a higher number of skilled affiliates, who in turn probably execute more successful attacks against well-defended targets. This cycle of attracting top talent and achieving results has cemented Qilin’s position at the top of the ransomware charts, demonstrating how a sophisticated offering creates a more formidable threat that is much harder for businesses to defend against.
Qilin has advertised the following advanced capabilities for its ransomware in its RAMP dark web recruitment posts.
Capability | Specific RaaS Platform Offering | Significance |
Automation | It can reboot the host in Safe Mode with an automatic login to execute its files. | Safe Mode is an operating system mode that starts a computer with minimal software running. Executing ransomware in this mode helps bypass many defense and logging tools, preventing detection and containment. |
It automatically selects the encryption mode based on file size. | Ensures the best balance of speed and strength during file encryption. Smaller files, which will not impact encryption speed, are fully encrypted to prevent remediation, while larger files are only partially encrypted to ensure all hosts and files on the network can be encrypted before containment. | |
Customization | The platform offers four unique encryption modes that prioritize speed, strength, or a balance of both. | Allows the operator to choose a balance between encryption speed and strength, with options for full, fast, percentage-based, or file path-based encryption. |
It gives affiliates the ability to distribute a custom file over the network. | Operators can include their own malware, such as scripts for persistence or remote access. These scripts can ensure access to a machine even after the ransomware has been remediated, enabling additional data theft or ransomware deployment. | |
Advanced Tools | It provides a proven default configuration for ransomware deployment. | Provides less-experienced teams with a ransomware configuration that has been proven successful in multiple environments. |
The ransomware is designed to delete backups and system logs automatically. | Ensures the organization cannot circumvent extortion by reverting to backups and prevents detection and investigation efforts, as many are based on system logs. |
Once the most successful ransomware group, “LockBit” has been struggling to regain the top spot since recent law enforcement disruptions. In June 2025, the group announced “LockBit 5.0,” a new version of its ransomware that appears to represent an attempt to reclaim its position by fully embracing the RaaS recipe for success. According to security research into this new iteration, this version offers many advanced capabilities, likely to compel more affiliates to join and drive the group back toward the top
Capability | Specific RaaS Platform Offering | Significance |
Automation | According to forum comments from probable affiliates, the group is likely adding AI into its ransomware to create capabilities similar to those of AI-enhanced malware “PromptLock.” | Uses AI to add randomization to the ransomware execution methods, so tactics are unique per deployment and previous attack patterns cannot be used for defense. |
Customization | The platform offers customization options that allow an affiliate to target specific directories and file types.ii | Allows the attacker to prioritize the most sensitive data within an environment. Critical data is encrypted quickly to cause the greatest damage. |
Advanced Tools | It includes a feature for the termination of security services on a compromised host.iii | Disables security tools so they cannot alert or contain the malware. |
The ransomware is also capable of patching Event Tracing for Windows (ETW) to prevent logging. iv | Causes Windows logging to fail, stopping any detections or investigation |
Medusa Misses the Mark: Why RaaS Groups Might Falter
Medusa is a well-established group that struggles in comparison to the top groups. While the group has named over 300 organizations on its data-leak site since 2024, the average number of organizations it named each month has recently dropped to 7, down from 18, while Qilin averages almost 60 organizations a month.
Medusa fails to advertise or offer the key success factors of automation and customization.
While it provides some tools, such as AV bypass and brute-force capabilities, these are common offerings and are not as advanced as those of top-tier groups.
Not providing the complete trifecta of capabilities probably prevents Medusa from attracting elite talent, ensuring that while it remains active, it will likely never become a leading threat.
Predicting the Next Wave of Top RaaS Groups
Applying the success model from established groups, we’ve hypothesized which emerging RaaS operations will probably succeed. Our analysis indicates that groups like The Gentlemen and DragonForce, which offer advanced capabilities, are likely to become significant threats, unlike groups like “Chaos” and “Nova,” which lack these factors.
The Gentlemen: A New Threat Arriving Fully Armed
First observed in September 2025, The Gentlemen is a new RaaS group that has already established a significant presence. Its advanced capabilities mirroring those of top groups—including automation, customization, and advanced tools—have likely driven its success, naming over 30 organizations on its data-leak site in its first month alone. By exhibiting the key indicators of a successful RaaS operation from its inception in its RAMP posts, The Gentlemen provides strong support for our model and represents a probable sophisticated threat.
Capability | Specific RaaS Platform Offering | Significance |
Automation | The platform features an automatic selection of the encryption mode to balance speed and strength. | Like the offering from Qilin, this feature provides an optimal balance of speed and strength during file encryption to ensure maximum impact. |
The ransomware performs an automatic discovery of network endpoints to enable faster spreading. | Allows the ransomware to spread faster to additional endpoints and lock more machines, ultimately causing more operational downtime and increasing the chances of an extortion payment. | |
Customization | The platform allows affiliates to set priority encryption by file or network path to target critical data first. | Similar to LockBit, this allows for the prioritization of critical data, ensuring maximum damage is inflicted as quickly as possible. |
Customization options allow for the exclusion of specific hosts from encryption, protecting attacker-controlled machines. | Causes the ransomware to ignore attacker-controlled virtual machines (VMs), which are used for persistence and to deploy the ransomware across the network in more advanced attacks. | |
Advanced Tools | The ransomware is capable of complete self-destruction, a process that includes deleting its own files, logs, and backups. | Like offerings from both Qilin and LockBit, these features—including log and backup deletion—help ensure that the ransomware cannot be detected, remediated, or investigated for future defensive purposes. |
The group’s advanced toolset includes EDR-killer and lateral movement tools to compromise sophisticated networks. | These tools enhance an affiliate’s ability to compromise sophisticated networks, ultimately allowing for faster and more successful attacks against larger organizations. |
DragonForce: An Emerging Threat Forged in Automation
DragonForce is another RaaS group emerging as a top player, offering advanced capabilities combined with aggressive recruitment efforts—exemplified by one of the most detailed recruitment posts online (see Figure 1)—to drive its success.
In 2025, these methods helped it double its average monthly DLS listings from 8 in 2024 to 16.
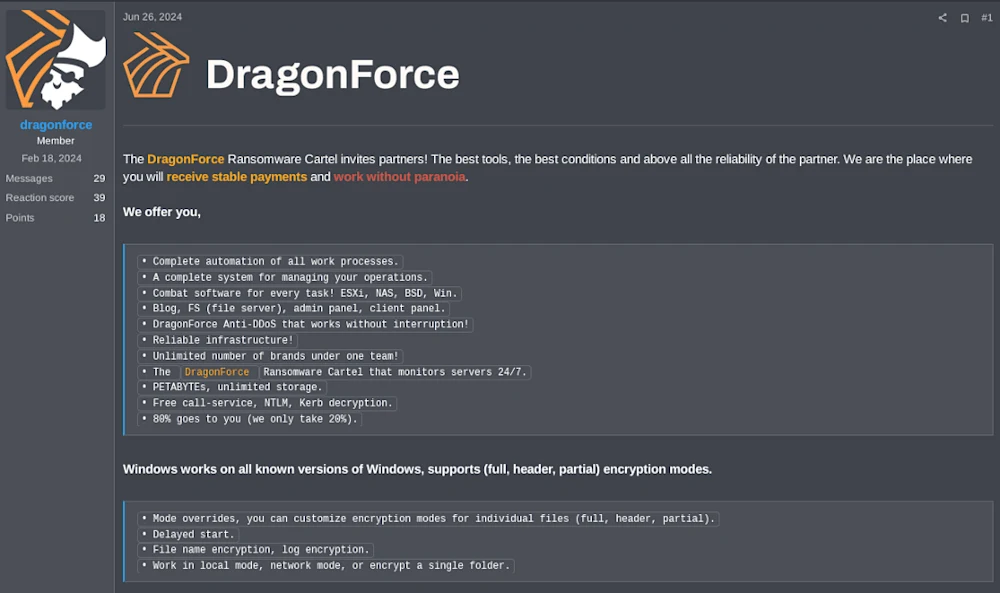
Figure 1: DragonForce's dark web forum recruitment post on RAMP
Chaos and Nova Appear Destined to Fizzle
Failing to offer the three key factors, or providing only weak implementations, probably prevents groups from recruiting skilled affiliates and highly likely results in fewer successful attacks. Based on this, we theorize that Chaos and Nova RaaS operations are unlikely to be successful. Here are the reasons why:
Chaos only offers some automation and AI through chat agents that assist with extortion negotiations, but these do not have a direct impact on the ransomware’s capabilities.
Nova offers AI chatbots for negotiations with some automation and tools but nothing advanced, like network discovery, encryption modes, or EDR killers.
The lack of these offerings is highly likely the reason they have failed to compromise organizations in the same volume. Chaos and Nova list an average of two and six organizations a month, respectively.
While no ransomware groups can be ignored, security resources are limited and decisions on prioritization must be made. Ultimately, this analysis allows defenders direct their limited resources against the sophisticated emerging threats that follow our recipe for success, without completely disregarding the minor players.
Defend Against Tactics, Not Names
The volatility of the ransomware landscape, with numerous groups emerging and disappearing quickly, often leaves organizations unsure of how to defend against these ever-changing threats. However, our research indicates that the key factors of success remain largely the same across groups. Organizations should place less importance on each individual group and more on the ecosystem as a whole and the tactics, techniques, and procedures (TTPs) shared among them. Specifically, organizations should prioritize defense measures that counter how RaaS groups use automation, customization, and advanced tools.
ReliaQuest’s Approach
Accelerate your defense against RaaS groups and ransomware with ReliaQuest GreyMatter. Our agentic AI security operations platform automates routine security work, empowering your team to detect, investigate, and respond to threats with greater speed.
Automation
To counter the speed and automation that RaaS groups use to move to other hosts within a network, GreyMatter offers Automated Response Playbooks. While defenders cannot react fast enough to manually contain an outbreak, Automated Response Playbooks automatically trigger within minutes of a detection. This contains the threat and provides defenders the critical time needed to investigate and remediate the infection.
Customization
GreyMatter Workflows help organizations counter the customization attackers are including in their ransomware deployments. For example, attackers often prioritize the encryption of critical hosts that store the most important data and spread other custom malware designed to establish persistence alongside the ransomware. These workflows can be configured to automatically identify alerts on critical hosts or the presence of high-severity malware and rapidly prevent encryption.
Advanced Tools and Features
Some of the most common tools offered by ransomware groups are EDR killers and log manipulators or disablers, which prevent detection, investigation, and remediation. These tools obfuscate, change, or delete records of malicious activity before security tools can analyze them. GreyMatter Transit helps organizations prevent this by detecting threats as data flows from source to storage. This allows for faster alerting before the logs can be changed, keeping your team ahead of the evolving ransomware landscape.
Slash your MTTC to under five minutes—a critical defense against ransomware—by deploying GreyMatter’s Automated Response Playbooks alongside our detections. For rapid incident response, integrate these key actions:
Isolate Host: Instantly disconnects a compromised host from the network to contain ransomware, stop lateral movement, and allow for safe investigation.
Disable User: Halts unauthorized activity and prevents further damage by disabling compromised user accounts.
Reset Passwords & Terminate Sessions: Immediately revokes an attacker's access by invalidating stolen credentials and ending all active user sessions.
Your Action Plan
Our analysis indicates that the most successful RaaS groups are driven by a combination of automation, customization, and advanced tooling. To counter these evolving threats, organizations must adopt strategies that directly neutralize these advantages. The following three steps are crucial for strengthening your defenses.
Fight Automation with Automation: RaaS groups now use automation to reduce breakout times to as little as 18 minutes, making manual intervention too slow. Implement automated containment and response plays to keep pace with attackers. These workflows should automatically isolate hosts, block malicious files, and disable compromised accounts quickly after a critical detection, containing the threat before ransomware can be deployed.
Limit the Impact of Customization with Segmentation: RaaS platforms allow affiliates to customize attacks to prioritize critical data and deploy custom malware for persistence. Enforce strict network segmentation to create barriers that slow attackers down and contain the blast radius. By preventing easy access to high-value targets, segmentation neutralizes the effectiveness of customized attack paths.
Build a Layered Defense Against Advanced Tools: Top-tier RaaS groups provide affiliates with tools to disable EDR and delete security logs, rendering single lines of defense obsolete. Build a defense-in-depth strategy to ensure visibility. Use log forwarders to move security logs off hosts before they can be altered or deleted. Additionally, layer endpoint and EDR logging and create specific alerts to detect attempts to disable these tools—an early warning that allows organizations to contain an attack and minimize the scope of remediation.


