Key Points
Adversaries are increasingly recruiting AI experts to automate entire attack workflows, allowing for faster, scalable operations and freeing resources for other objectives.
Recruitment of ClickFix experts to distribute malware triggered a 200% spike in ClickFix activity between March and April 2025, while mentions of Azure and Entra quadrupled from 2023 to mid-2025, reflecting growing interest in cloud exploitation.
Job-related posts on dark-web forums like "Exploit" and "RAMP" doubled from 2023 to 2024 and matched 2024's total by mid-2025, highlighting rapid recruitment growth.
Among the most in-demand skills is English-speaking social engineering, with job posts more than doubling from 2024 to 2025. Recruiters account for 87% of these postings, indicating strong demand, likely fueled by the success of groups like “Scattered Spider” in leveraging this skill for initial access attacks.
Think of job postings and platforms like LinkedIn or Indeed come to mind. But cybercriminals have their own thriving job market on the dark web. Here, “recruiters” seek specialists with cutting-edge skills, driving adversaries to upskill and act as job seekers in an ecosystem that mirrors legitimate hiring practices.
This underground job market is booming. Job-related posts on prominent cybercriminal forums like “Exploit” and “RAMP” more than doubled between 2023 and 2024. By July 2025, the number of recruitment and self-promotion posts had already matched last year’s total. The market’s rapid growth market marks a critical shift in the threat landscape: Cybercrime is becoming more organized, specialized, and efficient.
To understand which skills will be required for the attacks of the future, we analyzed hundreds of dark-web job postings from January 1, 2023, to July 31, 2025. We found that adversaries are no longer simply using large language models (LLMs) to generate malware. They’re now recruiting AI experts to automate entire operations, marking a new evolution where automation drives more efficient cyber attacks.
We highlight the most in-demand skills and their implications for the threat landscape. For example, the recent recruitment of ClickFix experts to distribute malware has led to a 200% increase in related activity. These shifts showcase how rapidly attackers adapt—and the need for equally swift defenses.
The dark-web job market offers a glimpse into the future of cybercrime. Understanding what skills attackers are recruiting for now can help organizations anticipate—and counter—their next moves. Read on for insights into:
AI-driven cybercrime: Why adversaries are recruiting experts to automate workflows and reshape cybercrime operations.
Targeting Azure (Entra ID) and IoT: How attackers are evolving their strategies to exploit these technologies for more evasive and damaging attacks.
Proactive defense strategies: Practical steps your organization can take today to proactively prepare for the next generation of cybercriminals.
What’s Next: AI Automation, Cloud Attacks, and IoT Exploits
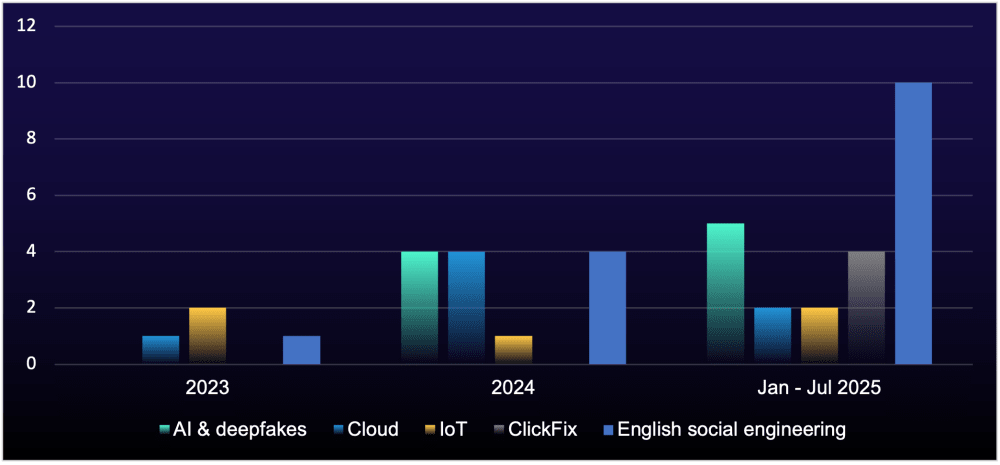
Figure 1: Emerging and trending cybercriminal job market skills by post count
Attackers are always on the hunt for fresh expertise, from AI experts to English-speaking social engineers. By analyzing skills promoted by job seekers and those requested by recruiters, we identified emerging, in-demand capabilities that go beyond the typical "pentester needed" ads associated with simply targeting Active Directory (AD) networks (see Figure 1).
Research Fueling Demand
The dark-web job market thrives on innovation, with cybercriminals often adopting techniques inspired by other adversaries or even published research that’s shared on criminal forums (see Figure 2). This cycle of innovation fuels recruitment, treating newly developed, defense-bypassing attacks as “products” to be distributed and deployed at scale among adversaries.
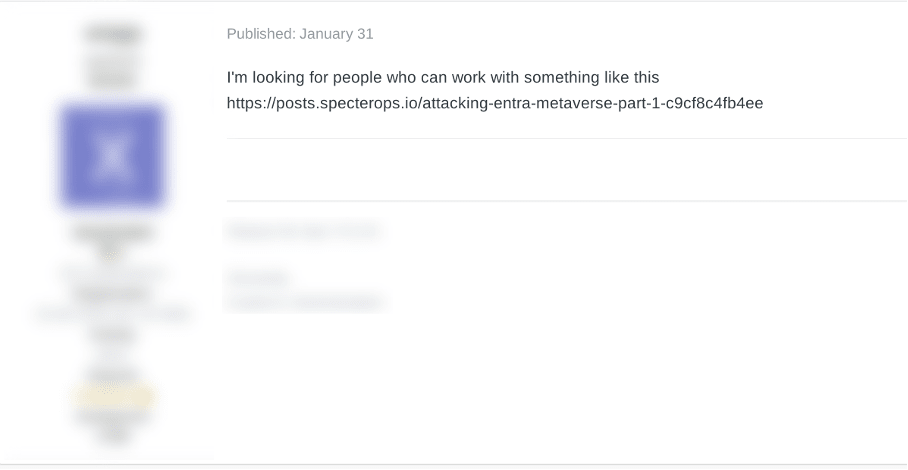
Figure 2: Exploit recruiter seeking a user to recreate an Azure attack (translated from Russian)
In this section, we explore the newly sought-after skill sets driving adversaries to upskill—skills that will likely be used to target organizations in future attacks. By understanding these trends now, organizations can better anticipate the evolving threat landscape and proactively strengthen defenses.
The Growing Threat of AI Automation and Deepfake Impersonation
Since Q3 2024, attackers have been recruiting AI experts to automate their operations, marking a shift from using AI for isolated tasks—like leveraging LLMs to develop malware—to fully integrating AI into operational processes. In the long term (beyond 12 months), attackers will highly likely continue with these efforts, allowing them to scale and streamline attacks while minimizing manual effort. For example, the ransomware group “GLOBAL GROUP” (formerly known as "BlackLock") has already integrated an AI chatbot into its ransomware negotiations, offloading this often time-intensive task.i
By automating operations, adversaries can conduct attacks faster and reduce downtime between attacks, leaving organizations with less time to detect and respond. The accelerated cadence of operations places immense pressure on security teams, stretching already limited resources and increasing the likelihood of successful breaches.
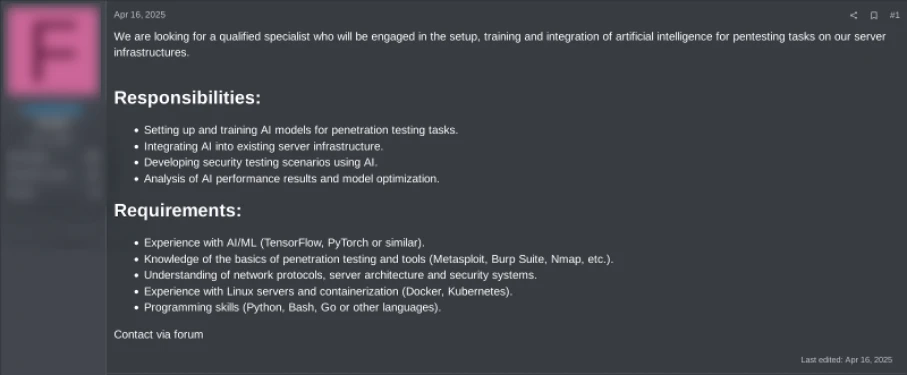
Figure 3: Exploit forum user recruiting AI expert (translated from Russian)
Deepfakes Continue To Dominate
Beyond automation, deepfake technology has emerged as a powerful tool for cybercriminals’ arsenal. Since Q2 2024, recruitment posts have advertised deepfake capabilities that enable attackers to impersonate employees and execute more effective social engineering attacks (see Figure 4). This tactic has already proven successful; in one notable case, adversaries used a deepfake impersonation of a CFO to scam a company out of $25 million in February 2024.

Figure 4: Recruiter seeking a social engineer with deepfake experience
Looking ahead, once deepfake technology enables adversaries to remove language barriers in real time, it will present an even greater threat. Attackers could target organizations across multiple languages, significantly expanding their reach. What’s more, with recruitment for English-speaking social engineers already at an all-time high (see Figure 1), real-time deepfake technology offers an alternative to traditional methods. As such, social engineering attacks will almost certainly become more prevalent. Without robust security measures, organizations face significant risk from these increasingly deceptive tactics, which are expected to emerge in the long-term future (beyond 12 months).
Attackers Look to the Cloud as Azure Recruitment Quadruples
Cloud environments are continuing to garner interest on the dark-web job market. Recruitment posts seeking candidates skilled in cloud exploitation—specifically Azure—quadrupled from 2023 to 2024. While mentions during the first half of 2025 have slightly declined, sustained activity suggests that growth will continue, with the potential for another spike by the end of the year.
The surge in activity between 2023 and 2024 is likely driven by financially motivated threat actors, such as closed ransomware groups or affiliates, seizing the opportunity to target cloud environments to pivot into Active Directory domains. This, in turn, allows attackers to steal sensitive data for extortion and other malicious purposes.
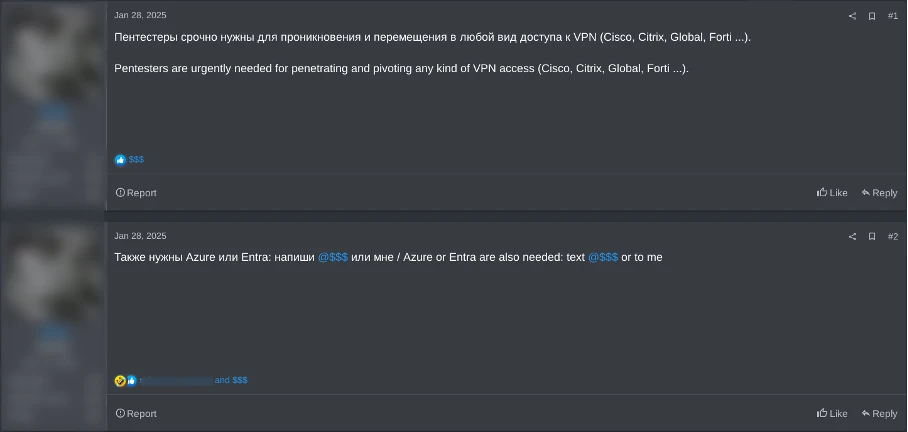
Figure 5: RAMP member recruiting users with VPN and Azure compromising experience
For example, a recruiter in Figure 5 explicitly seeks "pentesters" skilled in pivoting via VPNs and knowledgeable about "Azure or Entra," inviting them to connect directly or through a well-known figure, “$$$,” who frequently recruits for ransomware groups like GLOBAL GROUP.
To counter these threats, it’s imperative that organizations enforce least privilege access, implement multifactor authentication (MFA), conduct regular credential audits, and use tools like Cloud Security Posture Management (CSPM) to address misconfigurations and secure APIs. As organizations increasingly depend on the cloud, adversaries are ramping up efforts to exploit these environments. Proactive cloud security strategies are essential for securing environments and mitigating the rising risks of data breaches and operational disruptions.
The Future of Security Evasion Lies in IoT Exploitation
Recruitment for skills related to compromising Internet of Things (IoT) devices first appeared on dark-web forums in 2023. Although interest waned in 2024, recruitment has rebounded and is now on track to surpass previous years by the end of 2025 (see Figure 1). This renewed focus is likely due to these devices being unmanaged and riddled with vulnerabilities.
A stark example occurred in March 2025 when “Akira” ransomware exploited a camera to bypass EDR systems, deploying ransomware and rendering the EDR solution ineffective.iii Such tactics underscore the growing appeal of IoT exploitation as attackers seek alternative pathways to achieve their objectives.
The long-term outlook (beyond 12 months) signals a continued rise in IoT-related attacks. As organizations integrate more IoT devices into their environments, the attack surface expands exponentially, creating more entry points for cybercriminals. Without proper inventories, these devices often become blind spots, enabling adversaries to circumvent security controls and increase the risk of breaches.
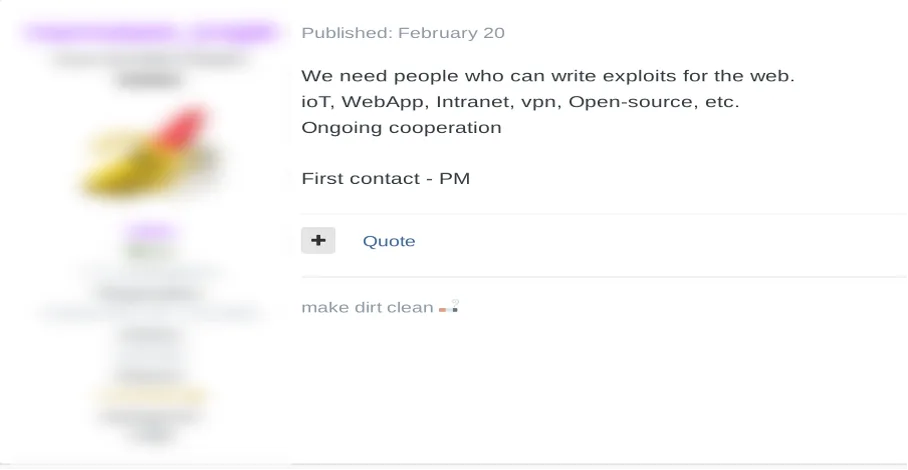
Figure 6: Exploit forum user recruiting exploit developer with IoT experience (translated from Russian)
In Demand Now: ClickFix, Social Engineering, Hypervisors
The cybercriminal job market is reshaping the threat landscape, with attackers shifting focus toward ClickFix malware execution, English-speaking social engineering, and hypervisor expertise. These in-demand skills highlight changing priorities as attackers look to maximize impact and profitability. As cybercriminals recruit talent to fill these skill gaps and replicate successful tactics, organizations must stay vigilant and prepare for attacks that often follow shortly after these trends emerge on dark-web marketplaces.
ClickFix Recruitment Drives 850% Surge in Activity
The cybercriminal job market is a key driver in accelerating the adoption of emerging attack techniques, as demonstrated by the rise of ClickFix malware execution. Between late 2024 and early 2025, ClickFix activity surged by an alarming 850%, with a 200% spike occurring within just one month of targeted recruitment posts appearing. This rapid escalation highlights how demand for specific expertise directly fuels the deployment of new methods, making it essential for organizations to monitor these shifts and proactively strengthen defenses.
Let’s look at the ClickFix lifecycle. The ClickFix technique was first seen being deployed by an innovative adversary in May 2024 and then gained traction as a novel attack vector. By March 2025, recruitment posts seeking specialists in ClickFix execution began appearing (see Figure 7). Shortly after, the volume of attacks leveraging this technique skyrocketed, underscoring how recruitment significantly amplifies the operationalization of a new technique.

Figure 7: Exploit user recruiting for ClickFix expert (translated from Russian)
English Proficiency Is the Key to Social Engineering Success
By 2025, English-language social engineering became the most sought-after skill in the cybercriminal job market. Job adverts mentioning this skill more than doubled between 2024 and 2025 (see Figure 1), with 87% of posts created by recruiters and the remaining 13% by job seekers—a clear indicator of the significant demand for this skill.

Figure 8: Black Basta social engineering pay inquiry and response (translated from Russian)
Ransomware groups such as “Black Basta” have previously demonstrated the effectiveness of leveraging English-speaking social engineers to obtain initial access and then handing off to another team for further exploitation. This team effort highly likely allowed attackers to circumvent security controls, such as email security gateways, which would have otherwise blocked the malicious ZIP file provided by the social engineer. A chat leak from early 2025 from the Black Basta group revealed just how desirable this skill set is (see Figure 8).
The large increase in job postings almost certainly reflects efforts by cybercriminals to replicate the success of groups like “Scattered Spider” and Black Basta. This indicates that English-language social engineering attacks are likely to become more frequent moving forward.
As a result, organizations must prepare to counter the rising threat of social engineering attacks. This includes strict help-desk procedures, secondary verification for MFA device enrollment, and training users to only use official channels for IT support.

Figure 9: Exploit user highlights English speaking and social engineering in job advert (translated from Russian)
Hypervisor Expertise Becomes a Standard in Cybercrime
Hypervisors have become a staple skill in the cybercriminal job market, as they offer attackers the ability to compromise multiple virtual machines (VMs) simultaneously. This makes hypervisors a lucrative target for adversaries seeking to maximize impact and efficiency. By examining the demand for hypervisor expertise, we can better understand how attackers are evolving their methods and anticipate future threats.
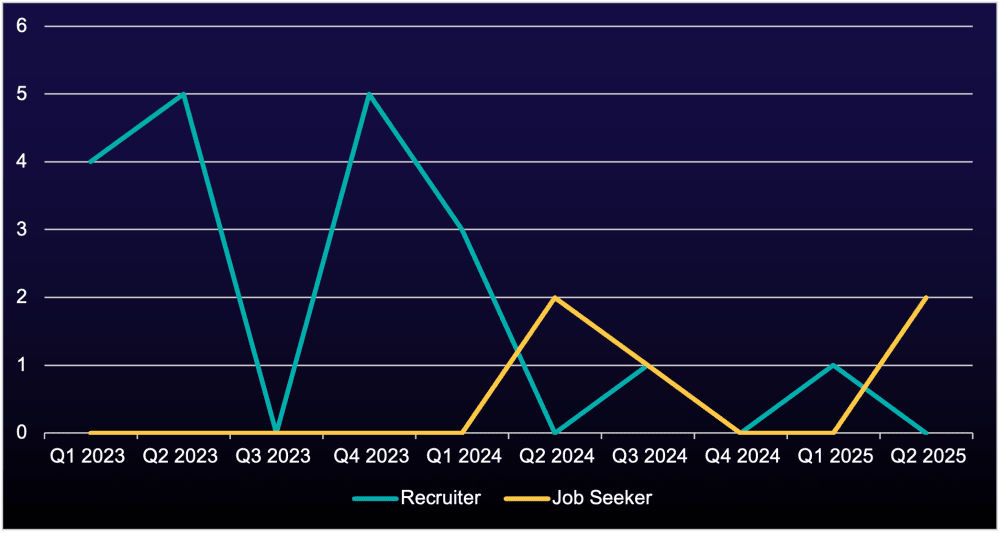
Figure 10: Recruiter or job seekers mentioning hypervisors (January 2023–July 2025)
This fluctuation in demand for hypervisor expertise tells a familiar story: When there’s demand for an expertise, adversaries quickly upskill to fill the gap (Figure 10). It also shows there was a clear shortage in hypervisor skill in 2023. However, as the demand was met, hypervisor expertise became just another standard skill in the criminal job market, highlighting the adaptability of the adversary ecosystem.
One notable example of hypervisor abuse involves Scattered Spider. The threat group compromised a company’s ESXi environment by obtaining domain administrator credentials through social engineering. Once inside, it created its own VM within the ESXi environment to stage and deploy the “RansomHub” encryptor. This tactic allowed the group to evade EDR systems defenses and complete the attack in just six hours.
New Tricks, Same Goals, and How to Defend Against Them
Although attackers continue to innovate their attacks and pursue up-and-coming skill sets, their goal remains the same: profit through data exfiltration and system encryption. The consistency in these core objectives gives organizations an advantage, allowing them to tailor defenses to disrupt attackers’ progress.
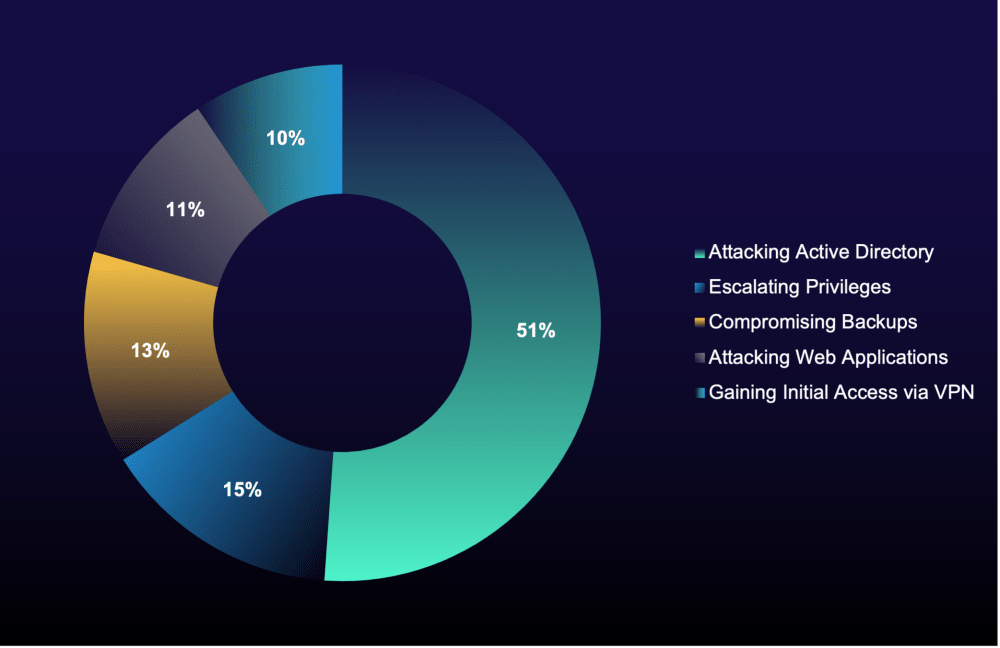
Figure 11: Top criminal job market skills (January 2023–July 2025)
Between 2023 and 2025, the number of attackers advertising Active Directory-related skills doubled, while recruitment for this expertise dropped by 60%. This shift signals that attackers have become highly adept at targeting Active Directory, making it a critical focus for organizational defenses.
For defenders, this is a silver lining. A robust defense-in-depth strategy can slow adversaries down enough to deter them. Much like burglars, attackers are likely to abandon their heist and move on to easier targets when encountering too many obstacles and delays.
ReliaQuest’s Approach
ReliaQuest provides its customers with advanced detection and response tools to swiftly identify and address threats associated with the tactics, techniques, and procedures (TTPs) detailed throughout the report.
ReliaQuest GreyMatter DRP: With the rise in attacks targeting IoT devices, monitoring publicly exposed assets like ports and access keys has become essential for defending against emerging and unknown attack techniques. The GreyMatter Digital Risk Protection (DRP) solution offers visibility and detection of exposed assets, enabling security teams to close ports, change keys, and mitigate threats associated with IoT compromises.
Detection Rules: ReliaQuest’s extensive library of detection rules is built on the latest threat intelligence and research, which helps organizations identify suspicious activity.
By deploying ReliaQuest’s detection rules in combination with the following Automated Response Playbooks, organizations can cut their mean time to contain (MTTC) from hours to minutes and mitigate the impact and post-exploitation of attacks:
Reset Passwords and Terminate Sessions: Terminating the live session immediately halts any ongoing attacker activity and forces a reset of credentials to prevent re-entry. This is especially effective against attackers who have stolen credentials and attempted to change the associated MFA device.
Disable User: Disabling user accounts prevents any further actions from being taken. In the event of a compromise, this step blocks all activity associated with the suspicious user, halting any potential damage.
Block IP: Blocking IP addresses prevents them from being used within potentially malicious environments. Stopping attackers from using IPs can prevent them from re-entering the environment from the same IP address.
Your Action Plan
With threats constantly evolving, staying ahead of the game is critical. Proactively strengthening your security today can make all the difference in tackling tomorrow’s challenges.
Stay Ahead of AI-Driven Threats: Use vulnerability management tools for automated scanning and reporting and integrate them with ticketing systems to streamline remediation. Attackers are leveraging AI to quickly identify patterns, scan networks, and uncover vulnerabilities at scale. Regularly scanning your infrastructure ensures you stay one step ahead and reduces the risk of exploitation.
Conduct Social Engineering Training and Testing: Train employees to spot social engineering tactics, like phishing, to build a vigilant workforce that can better resist unsolicited attempts at manipulation. Regularly testing the help-desk team’s adherence to security protocols further strengthens defenses, ensuring your organization is equipped to recognize and block these threats, ultimately reducing the risk of unauthorized access.
Adopt a Risk-Based Approach to Security: Regularly assess risks to identify and prioritize high-value assets and potential attack vectors. Focus resources on protecting these assets and implement adaptable risk management frameworks to stay ahead of evolving threats. Attackers thrive on exploiting overlooked or under-protected systems, so by strategically allocating resources, organizations reduce the chances of leaving exploitable vulnerabilities.
Andrew Adams and Hayden Evans are the primary authors of this report.