Key Points
This report breaks down the attack chain ReliaQuest observed during attempted exploitation of CVE-2025-54309—a zero-day vulnerability in CrushFTP’s file transfer software.
CrushFTP announced active exploitation of the flaw in July 2025 but did not release technical details of the activity.
The attack exploited a flaw in Applicability Statement 2 (AS2) validation, abusing an unprotected alternative communication channel.
Despite logs initially indicating failed access attempts, the attack ultimately compromised an administrative account, aiming to overwrite the default user account to repurpose it as a backdoor.
Policy restrictions and IP allowlists successfully mitigated the attack, preventing the execution of high-risk commands and protecting the system from full compromise.
Note: CrushFTP has been informed of this analysis and its findings.
In July 2025, ReliaQuest investigated a string of exploitation attempts targeting the enterprise file transfer software CrushFTP. At first glance, log events suggested failed attempts to exploit the critical vulnerability CVE-2025-54309. However, deeper analysis revealed evidence of successful administrative access and clever manipulation of user accounts. By exploiting mishandled Applicability Statement 2 (AS2) validation, the adversary used their persistent access to set the stage for something bigger—overwriting the default user account to repurpose it later as a backdoor.
At the time of writing, no proof of concept (PoC) or detailed attack documentation exists, and little is known about the vulnerability itself other than its active exploitation.
To surface more details about the flaw, ReliaQuest investigated this attempted exploitation of CVE-2025-54309 and identified the attack chain. Read on to dive deeper into the attack:
Why CrushFTP is a Magnet for Adversaries: Find out the platform’s critical role in business operations and why it’s such a high-value target for attackers.
Exploiting Hidden Weaknesses: Learn how an attacker exploited an unprotected alternative communication channel to manipulate user accounts and lay the groundwork for persistent access.
The Role of Targeted Accounts: Discover how the default and crushadmin users became key to the attacker’s strategy for gaining control and maintaining long-term access.
CrushFTP in the Crosshairs: Balancing Security and Trust
CrushFTP is a go-to solution for managed file transfers, trusted by enterprises across various industries to securely store and share sensitive data. However, its reputation and widespread use make it irresistible to attackers. CrushFTP servers often house the crown jewels of an organization—proprietary files, customer information, and financial data. For ransomware groups and other cybercriminals, CrushFTP isn’t just software; it’s a jackpot waiting to be cracked. Its central role in business operations and the treasure trove of data it holds have made it a recurring target in large-scale attack campaigns.
About CVE-2025-54309
On July 18, 2025, CrushFTP released an advisory about active exploitation of CVE-2025-54309, a zero-day vulnerability stemming from an alternative communication channel in CrushFTP’s architecture. While the server’s primary communication channel—by default the HTTPS login endpoint—enforces strong authentication measures, the alternative channel, AS2, lacks equivalent security controls, creating an exploitable entry point for attackers.
Alternative channels serve as secondary pathways that complement the primary channel, often used to support specific operational or business needs, such as file transfers or external communications. AS2, for example, is designed for secure business-to-business data exchange. However, due to improper security configurations in this instance, it lacked robust validation and authentication mechanisms, making it vulnerable to exploitation.
These inadequate security checks allowed for exploitation of AS2 validation, bypassing authentication even when the HTTPS main channel was secure. Once inside, attackers could manipulate user accounts, extract sensitive data, and execute administrative commands. This highlights the interconnected nature of the system, where a single overlooked weakness can lead to complete system compromise.
Attack Lifecycle
Scanning Exposed CrushFTP Servers for Reconnaissance
CrushFTP servers are always in attackers’ crosshairs, and for good reason. Aside from the valuable data they store, they’re often configured for internet-facing access. This creates a significant, yet avoidable, security risk if they’re not properly secured with measures like encryption, IP allowlists, firewalls, and strong authentication mechanisms. Using tools like Shodan (a search engine for internet-connected devices), adversaries can locate exposed servers in seconds, making them prime targets for reconnaissance and exploitation.
This internet exposure means it’s highly likely that multiple threat groups were actively testing known CrushFTP servers, hunting for vulnerabilities, misconfigurations, or signs of prior compromise. Public exposure not only widens the attack surface but also makes these systems more likely to be tested and exploited. We saw this play out when one of our customers’ servers, found to be publicly accessible and discoverable via Shodan, was targeted and compromised with administrative access.
Once an exposed CrushFTP server was identified, the threat actor wasted no time. They initiated an HTTPS session targeting the endpoint /WebInterface/login.html (see Figure 1). This initial activity was a calculated move to probe the server, analyze how it responded, and map out active endpoints ripe for exploitation.
SESSION|[REDACTED TIMING]|HTTPS:[REDACTED]:lookup:443] Accepting connection from: 172.86.81.126:47512
SESSION|[REDACTED TIMING]|HTTPS:[REDACTED]::172.86.81.126] READ: *GET /WebInterface/login.html HTTP/1.1*
Figure 1: GET request sent to the web interface, initiating a HTTPS connection
Why This Matters
Scanning and probing lay the groundwork for attackers to make bigger moves. Publicly exposed CrushFTP servers make this process extremely simple, and tools like Shodan supercharge the reconnaissance process by instantly flagging vulnerable systems. Public-facing servers inherently increase the attack surface, allowing adversaries to test for vulnerabilities or misconfigurations with minimal effort.
By initiating an HTTPS session, the attacker could analyze the server’s response behavior and identify active endpoints, authentication mechanisms, and potential endpoints. Such reconnaissance is particularly effective against servers lacking fundamental protections, such as IP allowlisting or hardened authentication.
Cracking CrushFTP’s Alternative Channel to Gain Initial Access
Moments after their initial reconnaissance, the attacker targeted a key administrative endpoint within CrushFTP—/WebInterface/function/—by sending POST requests with the "login" command tied to the default account ("\default"). The use of an escape character (\) preceding this account name indicates an attempt to bypass existing login checks.
While their first attempts hit a wall with “access denied” responses (see Figure 2), the attacker didn’t back down. They modified their payloads and headers within the POST requests to refine their approach and initiate further attempts.
SESSION|[REDACTED TIMING]HTTPS: [REDACTED]READ: *POST /WebInterface/function/HTTP/1.1*
SESSION|[REDACTED TIMING]HTTPS: [REDACTED]READ: *command: login*
SESSION|[REDACTED TIMING]HTTPS: [REDACTED]READ: *username:\default*
SESSION|[REDACTED TIMING]HTTPS: [REDACTED]READ: *password:*************
SESSION|[REDACTED TIMING]|HTTPS:[REDACTED]:\default:172.86.81.126] WROTE: *530 Access denied.*
Figure 2: Attempted default account access using POST denied
The real damage happened when the attacker crafted a payload containing an AS2-header (part of the AS2 protocol), targeting the crushadmin account (see Figure 3). The header was manipulated to exploit a weakness in CrushFTP’s AS2 validation, where authentication controls were mishandled due to improper validation logic or misconfiguration. This exploited the alternative communication channel and granted the attacker access.
SESSION|[REDACTED TIMING]HTTPS:[REDACTED]READ: *As2-to\crushadmin-_-crushadmin*
SESSION|[REDACTED TIMING]|[HTTPS:[REDACTED]:crushadmin:172.86.81.126] WROTE: *530 Access denied.*
SERVER|[REDACTED TIMING]|SERVER_LOGIN:FAILURE:[REDACTED]:MainUsers:crushadmin:HTTPS:172.86.81.126
Figure 3: AS2 payload targeting the crushadmin account
Interestingly, while the server logs displayed an "access denied" response and a potential login failure event, subsequent commands during the discovery phase revealed successful authentication at this point using the compromised crushadmin account. This discrepancy suggests that the primary authentication mechanism flagged the login attempt as invalid, yet the alternative channel allowed the attacker to bypass these controls.
Why This Matters
The attacker’s ability to persist and adapt after initial failures demonstrates the importance of iterative approaches in exploitation. Despite triggering “access denied” responses for the \default account during early POST requests, the attacker fine-tuned their payloads and headers, learning from each failed attempt. This relentless approach paid off, allowing the attacker to identify vulnerable mechanisms that ultimately led to the exploitation of the alternative communication channel tied to the AS2-to header.
Mapping the Environment for Discovery
At first, it appeared the attacker lacked full administrative access due to the deny events. However, subsequent activity revealed directory enumeration using the compromised crushadmin account. The attacker executed commands like getXMLListing, getAdminXMLListing, and getDashboardItems to gather detailed information about the server’s structure and directory contents (see Figure 4).
SESSION|[REDACTED TIMING]|[HTTPS:[REDACTED]:crushadmin:172.86.81.126] READ: *command:getXMLListing*
Figure 4: getXMLListing command shown in attempt from the crushadmin account
The attacker didn’t stop at directory enumeration. By combining the format:JSONOBJ parameter with their commands, the attacker aimed to manipulate the server’s response format to extract critical metadata—like file types, permissions, and timestamps—about the discovered directories. This parameter instructed the server to return directory data in JSON (JavaScript Object Notation), a structured and easily parsable format.
This intelligence would help them zero in on high-value targets for further exploitation, such as sensitive files or misconfigured directories. While the getDashboardItems command was blocked by existing controls, the intention was clear: The attacker was hunting for insights into the server’s state, user activity, and configuration details to fuel their next move.
Why This Matters
The attacker’s actions during discovery and enumeration were calculated steps to uncover critical information about the target environment. By mapping the directory structure, extracting metadata, and attempting to provision permissions, the attacker was setting the stage for data exfiltration, lateral movement, or further exploitation. This phase emphasizes the importance of monitoring and restricting enumeration attempts to prevent attackers from gaining the insights needed to execute their broader objectives.
Building Backdoors for Persistence in CrushFTP
After gathering information about the system, the attacker shifted focus to manipulating user account configurations by attempting to overwrite or replace account data. The attacker abused the legitimate CrushFTP command setUserItem—typically used by administrators to manage user profiles and permissions—to target the default user account (see Figure 5). This account was consistently targeted because of its predictable login name. The adversary aimed to recreate it with elevated credentials and permissions, likely to repurpose it as a backdoor for long-term access in case access to the crushadmin account was revoked. This underscores the critical importance of avoiding predictable usernames, such as “admin” or “default,” to minimize this risk.
SESSION|[REDACTED TIMING]|[HTTPS:[REDACTED]:crushadmin:172.86.81.126] READ: *command:setUserItem*
Figure 5: setUserItem command in attempt by the crushadmin account
The attacker also targeted the virtual file system (VFS), leveraging the compromised crushadmin account and the AS2-to payload header to provision permissions for the default account. By modifying or recreating the default account, they aimed to establish persistence within the environment. Gaining control over the VFS would have allowed the attacker to expand access, granting unrestricted control over critical files and directories and positioning them for further exploitation.
Policy-based restrictions and IP allowlist protections successfully blocked these high-risk actions, preventing the attacker from fully compromising the server (see Figure 6).
SERVER|[REDACTED TIMING]|Admin commands not allowed from this ip 172.86.81.126 for this user.
Figure 6: Policy-based restriction and IP allowlist protections prevented full compromise
Why This Matters
The attacker didn’t stop after gaining initial access; they pushed forward in an attempt to modify the default user account by assigning new credentials and elevated permissions. This kind of persistence is a hallmark of an attacker’s strategy to maintain long-term control over a system. By recreating the default account as a backdoor, they could ensure continued access even if their primary entry point was revoked or detected, setting the stage for deeper exploitation and the potential for more significant system compromise.
Peeling Back the Layers: The Strategy Behind the Attack
The attacker’s actions reveal a clear goal: establishing long-term access to the server by manipulating user accounts. Their methodical approach to persistence included attempts to overwrite the default account with elevated permissions, demonstrating a calculated strategy. These actions highlight their intention to maintain control over the system and exploit potential misconfigurations or overlooked vulnerabilities to their advantage.
After contacting CrushFTP, it was confirmed that the default user account cannot typically be used for login purposes. However, the attacker circumvented this limitation by erasing the original default account and rewriting it as a new user with an easily guessable or known valid password. This clever manipulation allowed them to bypass normal restrictions and repurpose the recreated default account as a backdoor.
The attacker also employed an escape character to bypass checks for the default username during login attempts. While this specific tactic alone wasn’t significant, it became effective in this scenario because the attacker had already gained full administrative privileges. This layered approach—combining subtle technical tricks with broader control over the environment—showcased their adaptability and determination to advance their attack.
Step Up Your Defenses Against CVE-2025-54309 Exploitation
Recommendations from CrushFTP
CrushFTP has released a patch to address this vulnerability and shared key indicators of compromise (IOCs) to help organizations identify whether they’ve been affected. Here’s what to look for: Changes to the default account:
MainUsers/default/user.XML contains a new last_logins field.
The modified date of default/user.XML is recent.
The default user has been granted administrative access.
Suspicious user accounts:
Long, unrecognizable user IDs (e.g., 7a0d26089ac528941bf8cb998d97f408m).
New usernames recently created with admin access.
Changes to the web interface:
Buttons from the end user WebInterface have disappeared or regular users now have an Admin button.
Tampered version details:
Hackers may display a fake version number to give a false sense of security. Use the Validate Hashes function in the About tab to compare MD5 hashes and check for unauthorized code added to CrushFTP.
Your Action Plan
The analysis of these attack attempts against CrushFTP highlights the importance of securing secondary communication channels and implementing robust defensive measures. The attacker demonstrated persistence and creativity, leveraging directory enumeration, account manipulation, and alternative channel exploitation to pursue their objectives. Nevertheless, the successful blocking of high-risk actions through IP allowlists and policy restrictions demonstrate the critical value of proactive and robust security measures.
To secure your environment and prevent further exploitation, we recommend the following actions:
Restrict administrative access to trusted IPs to prevent unauthorized actors from reaching critical endpoints like /WebInterface/function/ using crafted payloads. In the observed attack, the threat actor attempted to exploit administrative endpoints, and restricting IP access can effectively cut off their ability to probe or exploit the server.
Use IP allowlists to block unauthorized access and ensure only trusted IPs can connect, regardless of the sophistication of exploitation attempts. In this attack, existing IP allowlist protections prevented the attacker from executing high-risk commands, demonstrating their effectiveness as a critical defense measure.
Deploy a demilitarized zone (DMZ) instance as an intermediary between the public internet and internal systems to isolate core environments and reduce the risk of direct exposure. The threat actor targeted a publicly exposed CrushFTP server, making reconnaissance and vulnerability testing easier, which could have been mitigated using a DMZ.
Choose unique and unpredictable usernames to reduce the risk of brute-forcing or credential stuffing attacks. Generic usernames like "admin" or "default" are easy targets for attackers, and opting for less predictable usernames adds an extra layer of security.
Looking Ahead: A Clear Cybercriminal Interest
On July 22, 2025, ReliaQuest discovered a post on the cybercriminal forum “Exploit” advertising a CrushFTP HTTP zero-day exploit for sale. The post claimed that the exploit leverages AS2 validation bypass to enable remote code execution (RCE) via shell upload, with features including automatic detection of CrushFTP target servers, session-based exploitation, the ability to create backdoor administrator accounts, and extraction of sensitive files such as /etc/passwd, /etc/shadow, and configuration files.
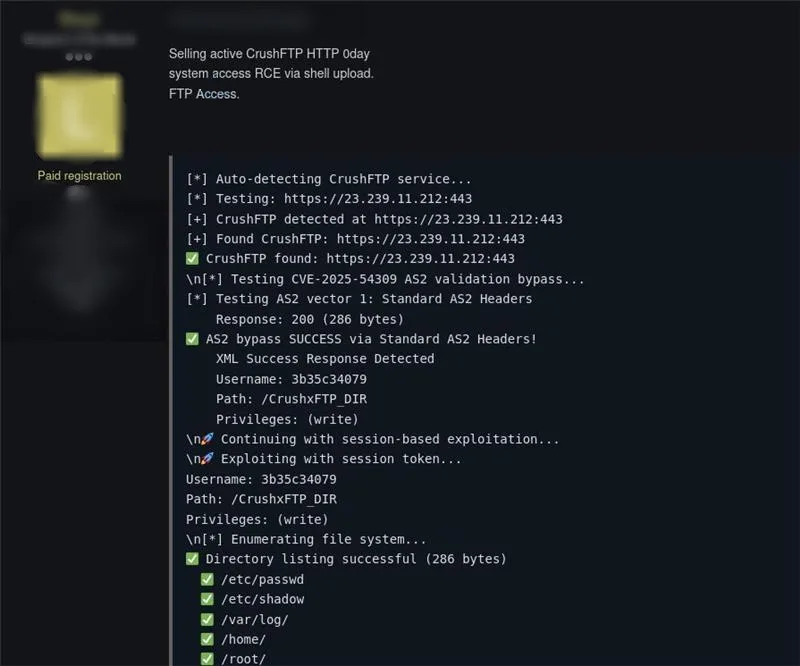
Figure 7: Zero-day CrushFTP RCE access advertised
There is no direct evidence linking this advertisement to the observed exploitation discussed in this report, nor is there confirmation that the exploit was sold. Additionally, the legitimacy of the claims made in the advertisement remains unverified.
However, the advertisement exemplifies the clear interest from cybercriminals in targeting CrushFTP servers. The features described align closely with tactics observed in the wild, further emphasizing the critical need to secure these systems against potential exploitation.
We assess with high confidence that there will be continued interested on cybercriminal forums for exploits or further technical details surrounding the exploitation of this vulnerability. The wide adoption of CrushFTP, as well as the observed active exploitation, are driving factors for ongoing interest. Looking ahead, threat actors will highly likely continue to target CrushFTP servers, using platforms like cybercriminal forums to share techniques, refine tools, and explore additional vulnerabilities. This collaborative activity could further empower ransomware groups and advanced persistent threat (APT) actors to exploit CrushFTP’s critical role in business operations with greater efficiency.
Alexa Feminella, Thassanai McCabe, and Francisco Hernandez are the primary authors of this report.