Editor’s note: This report was authored by Alexa Feminella
Key Points
Attackers are adapting and repurposing major zero-days, transforming single exploits into polymorphic threats that amplify their impact and complicate attribution and defense.
The SAP NetWeaver zero-day (CVE-2025-31324) exemplifies these risks, causing widespread ripple effects and demonstrating the high return and cascading potential of targeting enterprise technologies.
Underground markets reveal a clear preference for enterprise zero-days, with remote code execution (RCEs) dominating for immediate access and local privilege escalation (LPEs) emerging for malware effectiveness and facilitating access to enterprise low-system gaps.
Staying ahead of zero-days requires predictive intelligence, visibility, automation, and faster methods of detection like detecting at-source or in transit.
Months after we disclosed the critical SAP NetWeaver zero-day (CVE-2025-31324), groups currently making waves—like “Scattered Lapsus$ Hunters,” linked to “ShinyHunters”—dropped a chained exploit for the same vulnerability. But why do zero-days like this one keep evolving, and what makes them so irresistible for attackers?
When a major zero-day emerges, it sets off a dramatic chain of events, attracting multiple threat groups with varying motives who adapt and repurpose it—much like polymorphic “worm” malware that rapidly evolve with every new infection. Attackers thrive on their ability to act quickly and think creatively, leveraging versatile tools and malware to twist a single vulnerability into a variety of exploitation paths.
Consequently, defenders aren’t battling a single threat; instead, they face compounded risks from multiple simultaneous attacks, each widening the attack surface and amplifying the impact.
Cybercriminal forums drive this frenzy, turning enterprise zero-days into commodities. Remote code execution (RCE) vulnerabilities on average command a staggering revenue of $366,500—for their ability to deliver immediate access, while the rising popularity of local privilege escalation (LPE) exploits reflects attackers’ growing focus on maximizing malware impact and targeting low-level system gaps in enterprise environments.
Defenders face a race against time, as zero-days remain unpatchable until discovered—but the real challenge lies in anticipating the next major zero-day before it cascades into chaos. Read on to discover:
How major zero-days in enterprise platforms trigger cascading events, especially through attackers’ rapid adoption of simple, versatile exploits.
How cybercriminal forums are pivotal for attackers to advertise zero-days, where enterprise vulnerabilities are favorable, but also for analyzing recurring themes and trends evolving the zero-day market.
How to stay ahead of zero-day threats by employing GreyMatter Discover, Agentic AI, Digital Risk Protection (DRP) and detections, and why predictive intelligence is more critical than ever.
Major SAP NetWeaver Zero-Day Turns Polymorphic
Once a major zero-day becomes known, it evolves from a tool for advanced attackers to an accessible commodity for many. The SAP NetWeaver zero-day (CVE-2025-31324) exemplifies this, as attackers used varied “exploitation twists”—deploying tools like “Brute Ratel” for stealthy command-and-control (C2), the Heaven’s Gate technique for memory manipulation, and persistent backdoors like “PipeMagic.” These adaptations transformed the vulnerability into a polymorphic threat, evolving with each new tool and tactic and making it impossible for defenders to rely on a single mitigation strategy.
To make matters worse, proof-of-concept (PoC) exploits and dark web commodification accelerated the weaponization of CVE-2025-31324, shrinking defenders’ response windows. Nation-state actors and big-name ransomware groups wasted no time capitalizing on the open exploitation window, repurposing the same web shell deployment tactic but adapting it to suit their unique objectives.
This maximum severity unrestricted file upload vulnerability allowed attackers to deploy JSP web shells and execute commands remotely via simple HTTP requests, making it accessible even to attackers with limited technical expertise. As shown in Figure 1, one group’s actions inspire others to follow suit, creating a snowball effect of opportunistic activity and widening the overall exploitation ecosystem.

Figure 1: Cascading events of CVE-2025-31324
Unlike many zero-days that quietly go unnoticed, CVE-2025-31324 stood out for its technical simplicity, high-value environment, and versatility.
Although SAP acted quickly to release a patch for CVE-2025-31324, the exploitation timeline reveals how attackers adapt, seize opportunities, and thrive within an interconnected ecosystem—creating ripple effects that extend far beyond initial disclosure.
The Ripple Effect: How Zero-Days Foster Opportunistic Exploitation
When a versatile zero-day like CVE-2025-31324 emerges in an enterprise system, it creates a “perfect storm” for attackers and an overwhelming challenge for defenders. Each threat group adapts the vulnerability to suit its unique goals, building upon one another’s actions and creating broad, opportunistic activity across the cybercriminal ecosystem.
This dynamic evolution doesn’t just amplify the impact of the vulnerability—it increases the incentive for attackers to exploit it, as they see the success achieved by others. This interconnectedness among attackers complicates attribution, hinders predictions of behavior, and makes mitigation strategies increasingly difficult to prioritize.
Defending against zero-days requires a proactive, forward-looking approach. Organizations must focus on resilience, visibility, and attack surface reduction to anticipate and mitigate cascading risks before they spiral out of control.
While not every enterprise zero-day evolves into a widespread, cascading event like CVE-2025-31324, the potential is always there. Whether a zero-day cascades depends on how quickly attackers can adapt it, how versatile the vulnerability is, and how critical the targeted system is to enterprise operations.
Attackers Seek Enterprise and Networking Zero-Days
The most coveted zero-days are those for enterprise and networking platforms because of their versatility, profitability, and cascading impact potential—fueled by cybercriminal forums that enable the buying, selling, and brokering of zero-days.
Enterprise systems like SAP NetWeaver are packed with sensitive data, power critical workflows, and, once breached, open the door to bigger opportunities like ransomware campaigns or espionage. Networking devices, like VPNs and firewalls, play a big role too—they’re the gateways that connect enterprise systems, making them just as valuable to attackers.

Figure 2: Zero-Day Targets by Platform
The focus on enterprise platforms shows a clear strategy: Attackers want to hit systems that give them the most control and reach. It’s not just traditional enterprise setups—networking and mobile devices are increasingly targeted as attackers adapt to hybrid and mobile-first infrastructures. This means defenders need to focus on protecting key assets like enterprise servers, cloud environments, VPNs, and mobile devices. A single breach in any of these assets can quickly spiral into major disruptions, data loss, and even full network takeovers.
RCEs and LPEs: The Stars of the Zero-Day Market
While enterprise systems are the main target, the main types of vulnerabilities sought on these markets are RCE and LPE exploits. These zero-day types are indispensable for enabling the high-impact campaigns seen with SAP CVE-2025-31324, and now with the Microsoft SharePoint vulnerability (CVE-2025-53770), where attackers can leverage remote access to maximize their objectives.
On average, attackers make $366,500 for RCE vulnerabilities on cybercriminal forums, showing high demand, but the popularity of LPEs is rising fast. Below, we explore how each vulnerability type fits into cybercriminal strategies and how they relate to the major zero-days circulating in 2025 so far.
RCE: The Uncontested Champion
RCEs are the most sought-after zero-days on cybercriminal forums for good reason: they grant attackers immediate, remote access to critical systems, making them indispensable in enterprise exploitation. The exploit types most commonly advertised on cybercriminal forums include:
Pre-Authenticated RCEs
These exploits allow attackers to bypass login requirements, granting direct access to high-value enterprise systems. By targeting platforms that manage critical workflows and sensitive data, attackers can disrupt operations, steal information, and move laterally within networks.
Associated products:
Oracle E-Business Suite (EBS)
Cisco Secure Email Gateway
Cisco Identity Services Engine (ISE)
Fortinet FortiOS SSL-VPN
Palo Alto Networks
Ivanti SAML single sign-on (SSO)
Zero-Click Exploits for Mobile and Browsers
The prevalence of advertisements for these vulnerabilities highlights the growing risks to personal and corporate devices, which play a central role in hybrid work environments. By compromising these devices, attackers can access sensitive data, infiltrate corporate systems, and scale their attacks across large user bases.
Associated products:
iOS
Chrome on Android
Safari
PDF
iMessage
Full-Root RCEs for Android Devices
These exploits give attackers complete control over Android devices, enabling persistent surveillance, data theft, and lateral movement. Within enterprise environments, Android devices are often managed by Mobile Device Management (MDM) systems or used to access cloud services, making them valuable entry points for broader campaigns.
Associated products:
Chrome on Android
Android device
LPE: The Rising Star
While less in-demand than RCEs, the number of LPE ads has skyrocketed by 728.57% since early 2024. LPEs require attackers to gain access first but once inside, these exploits facilitate deeper system control, making them a natural complement to RCEs in coordinated attacks.
Why the surge in popularity? LPE exploits are easier to develop than RCEs and still bring in good money: $96,000 on average. But there are other reasons why attackers favor these flaws, including enhancing malware functionality:
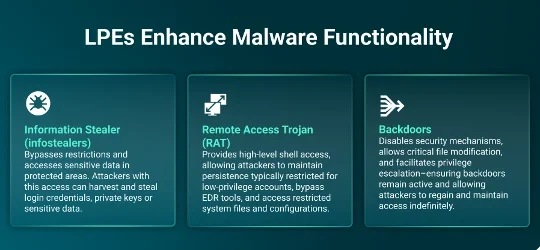
Figure 3: Malware types that LPEs can enhance
LPEs are also critical for escalating privileges when initial access is limited, such as with webservers:
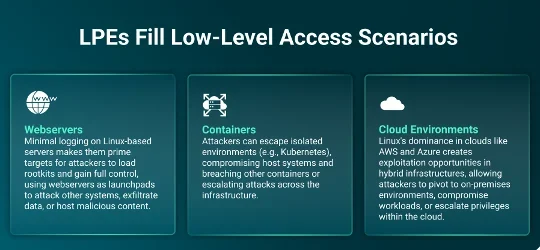
Figure 4: Environments that LPEs can help provide access to
RCEs + LCEs for Power and Profit
RCEs and LPEs complement each other perfectly in enterprise-focused campaigns. RCEs allow attackers to breach systems remotely, while LPEs provide the tools to escalate privileges, maintain persistence, and launch further attacks. Together, they create a pathway for cascading impacts and high-profit operations, including data theft, ransomware, and espionage.
Step Up Your Defenses Against What’s Next
While no one can predict the next major zero-day, we can learn from the characteristics of past zero-days that triggered cascading impacts. To stop the chain reaction, early detection is critical, enabling us to disrupt exploitation before it escalates.
ReliaQuest’s Approach
Zero-day vulnerabilities pose some of the most difficult challenges for organizations, requiring a proactive, multi-faceted approach to detection, prevention, and response.
Agentic AI: The ReliaQuest GreyMatter agentic AI security operations platform autonomously plans, executes, and adapts its responses to evolving threats, detecting vulnerabilities and malicious activity across SIEMs, clouds, or at the source.
By preventing threats before they escalate—such as resolving vulnerabilities or mitigating suspicious activity—agentic AI outpaces attackers. When necessary, it circulates critical issues to your team for immediate action, ensuring zero-day threats are neutralized proactively.
GreyMatter Discover: Zero-days thrive in environments with visibility gaps. GreyMatter Discover provides full visibility into every asset and identity across your environment, enabling you to identify and address vulnerabilities before they can be exploited. By uncovering what’s missing, misconfigured, or at risk, this tool allows organizations to take immediate action directly within the platform. With automated responses, GreyMatter Discover ensures exposures are resolved without delays, leaving fewer opportunities for zero-days to take hold.
GreyMatter Digital Risk Protection (DRP): The underground economy is a key driver of zero-day exploitation. GreyMatter DRP continuously monitors cybercriminal forums, analyzing zero-day advertisements and discussions to uncover emerging threats. By identifying trends in vulnerability types and technologies targeted, DRP provides early warning on zero-days before they can strike, enabling organizations to prepare ahead of time.
Detection Rules: Zero-days are often unknown until exploited, but early detection can change the game. ReliaQuest’s extensive library of detection rules, built on the latest threat intelligence and research, enables organizations to identify suspicious activity indicative of zero-day exploitation. These rules help detect and mitigate attackers’ tactics and behaviors, even before specific vulnerabilities are disclosed.
Your Action Plan for Zero-Day Defense
To defend against zero-day vulnerabilities and prepare for the next major zero-day, organizations should adopt a proactive, layered approach. Here’s how to get started:
Adopt Defense in Depth: Layered security strategies are crucial to countering the wide range of tactics attackers may use. From EDR to network segmentation and behavioral analytics, each layer increases the chances of early detection and disruption.
Prioritize Predictive Threat Intelligence: Move beyond understanding current threats to proactively identifying attacker patterns, trends, and potential vulnerabilities. Predictive capabilities empower defenders to prepare for what attackers might exploit next.
Focus on Resilience Through Threat Modeling: Resilience ensures systems can withstand attacks even when vulnerabilities are exploited. Regular backups, robust visibility, and continuous testing of defenses are integral to limiting the impact of zero-days.
Invest in Proactive Measures: With zero-days offering no immediate patches, reducing the attack surface becomes critical. Implement Zero Trust principles, vulnerability management, and sandboxing to limit attackers’ opportunities.
Enhancing Organizational Agility: Foster cross-functional collaboration between IT, security, and business teams to ensure a coordinated response. Regular incident response simulations and upskilling initiatives help organizations act decisively when zero-days arise.
Patch Smart, Not Just Fast: While patching is critical, not all systems can be patched immediately. Use a risk-based patching approach, focusing on vulnerabilities in exposed systems (e.g., internet-facing applications) or critical business functions. Deploy virtual patching (via firewalls or intrusion prevention systems) as an interim measure.
What’s Next for Zero-Days
As technology evolves, attackers are poised to exploit vulnerabilities in the systems driving modern business transformation. Cloud-native platforms and AI-powered technologies are shaping the next wave of zero-days, creating profound challenges for security leaders.
The Rise of Cloud-Native Zero-Days
Cloud-native platforms like Kubernetes, Docker, and serverless architectures are becoming the backbone of enterprise operations. However, their reliance on APIs, microservices, and interconnected architectures makes them prime zero-day targets.
A single zero-day in a containerized workload, cloud management tool, or orchestration platform could compromise entire ecosystems. Attackers could infiltrate supply chains, disrupt business-critical workflows, and exfiltrate sensitive data at scale. This interconnectedness means that a zero-day in one component of a cloud-native environment can ripple across enterprises, jeopardizing multiple organizations simultaneously.
Defenders must anticipate that attackers will increasingly exploit misconfigurations, API vulnerabilities, and interdependencies in cloud-native environments, making visibility and runtime security non-negotiable priorities.
AI’s Double-Edged Sword in Zero-Day Exploitation
Artificial intelligence is reshaping the zero-day threat landscape, both as a target and a tool. Attackers are already weaponizing AI to uncover vulnerabilities at unprecedented speed, using it to automate zero-day discovery in complex environments and hybrid infrastructures. This capability shrinks defenders’ response windows, amplifying the pressure to detect and mitigate threats in real time.
AI is also making exploitation more sophisticated. Automated tools can design custom exploits, chain vulnerabilities, and scale attacks faster than traditional methods. For example, attackers could use AI to identify hidden relationships between systems, predict defensive gaps, and execute precision-targeted campaigns against high-value enterprise environments.
On the defensive side, AI offers promise in predictive intelligence, anomaly detection, and automated remediation. However, the race between attackers and defenders will only accelerate as both sides compete to harness AI’s capabilities, creating a high-stakes arms race in the zero-day ecosystem.






