Editor’s note: This report was authored by Thassanai Mccabe
Key Points
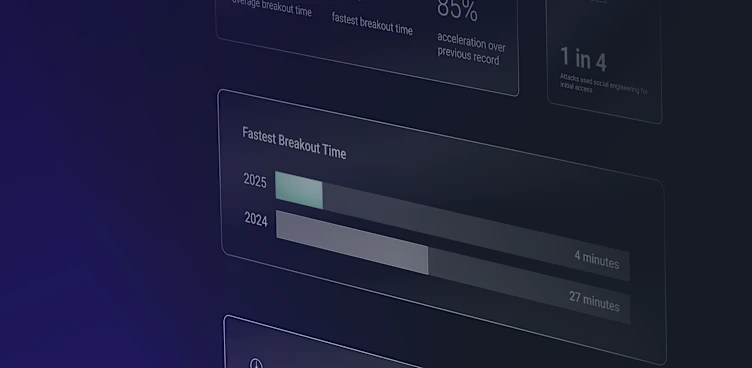
Axios user agent activity surged 241% from June to August 2025, dwarfing the 85% growth of all other flagged user agents combined.
Attacks that paired Axios with Direct Send achieved a 70% success rate in recent campaigns, outpacing non-Axios campaigns with unparalleled efficiency.
Attackers are highly likely to continue using Axios to automate and scale phishing campaigns.
Organizations are encouraged to implement robust detection mechanisms to identify and mitigate suspicious user-agent activity, with particular attention to Axios related patterns.
ReliaQuest has identified an anomalous surge in stolen credentials that likely indicates mass-automated phishing activity. Our investigation points to a rapidly evolving threat: attackers exploiting the Axios user agent—a lightweight, promisebased HTTP client—to automate phishing and credentialstealing at unprecedented scale. In recent campaigns, Axios abuse was amplified through Microsoft Direct Send, a trusted email delivery method that helps phishing traffic slip past secure gateways.
What's New?
Explosive Growth Across Multiple Detections: Between June and August 2025, activity tied to Axios as a user agent surged by 241%, far exceeding the growth seen across all other flagged user agents. Out of 32 flagged user agents observed in this timeframe, Axios accounted for 24.44% of all activity. This makes Axios 10 times more common than any other user agent attackers are using.
Staggering Success Rates: In the most recent campaign we tracked, 70% of incidents leveraging Axios and Direct Send resulted in credentials being stolen successfully. Over the past three months, Axios-powered attacks had a 58% success rate overall, compared to just 9.3% for incidents without Axios.
Shifting Targets: Beginning in July 2025, this campaign initially focused on high-profile individuals, such as executives and managers in industries like finance, health care, and manufacturing. By August, it had broadened in scope to include everyday users.
The combination of the Axios user agent with tools like Direct Send is proving to be a game-changer for attackers, yielding far higher success rates in account takeovers than traditional phishing methods, which were only seen succeeding around 9.3% of the time over the past three months. By exploiting the trusted nature of Direct Send and leveraging Axios’s lightweight, developer-friendly design, attackers are not only scaling their operations but also streamlining attack techniques to bypass traditional security defenses with alarming precision. This efficiency allows attackers to steal credentials faster, at a scale and success rate unmatched by other methods.
It’s highly likely that attackers will continue to refine and expand their use of Axios, pushing beyond phishing to exploit broader opportunities. Axios’s flexibility makes it a versatile tool—not just for phishing but for API exploitation, data scraping, and even large-scale infrastructure attacks. This positions industries heavily reliant on JavaScript frameworks, such as health care, e-commerce, and finance, as prime targets for escalating abuse. Read on to uncover:
Why Axios is the go-to user agent for attackers.
Why this trend should be on your radar.
How Direct Send and Axios work together to enable successful attacks.
Proactive steps your organization can take to mitigate the risks of Axios exploitation.
Axios: Attackers’ Go-To for Scalable Phishing
Speed and Stealth: Why Attackers Favor Axios
Axios has become the go-to weapon for attackers, driving modern phishing campaigns with speed, scale, and automation that is hard to match when using alternate user agents. At the heart of the 241% surge in activity, Axios lets attackers juggle tasks like sending HTTP requests, stealing credentials, and hitting APIs all at once. The result is more victims, less effort.
What makes Axios stand out is its ability to adapt in real-time. Its promise-based API and middleware interceptors let attackers log, tweak, replay, and troubleshoot easily. This makes it easier to bypass multifactor authentication (MFA), hijack session tokens, and tailor attacks to each target.
In the Axios activity we saw, QR codes and phishing domains set the trap, then Axios let attackers exploit the data they captured. In the incidents we observed, Axios played a pivotal role in interacting with APIs and bypassing MFA protections. Attackers used Axios to:
Capture session tokens or MFA codes through sophisticated phishing workflows, allowing them to bypass authentication barriers.
Exploit SAS tokens in Azure authentication workflows. Specifically, Axios requests leveraged the Shared Access Signature (SAS:BeginAuth) mechanism to manipulate or hijack tokens, granting access to sensitive resources without direct authentication credentials.
With its simplicity, automation, and flexibility, Axios gives attackers the edge to scale operations with precision and minimal effort. It wasn’t built for malicious use, but attackers are exploiting it to supercharge their campaigns—and, as evidenced by the observed activity surge, it’s working.
The Problem with Other User Agents
Axios addresses the problems older tools like Python’s requests library or curl can’t. In comparison, other legacy options are slower, less efficient, and tougher to scale for phishing campaigns that need speed and efficiency. Without asynchronous workflows, attackers are stuck running tasks like sending HTTP requests, stealing credentials, and interacting with APIs one at a time—slowing down operations and limiting both reach and therefore, their impact.
What sets Axios apart is its ability to intercept, modify, and replay HTTP requests effortlessly, which is critical for bypassing MFA and adapting attacks in real-time. Attackers can integrate Axios seamlessly into modern JavaScript frameworks, blending into legitimate workflows while scaling their campaigns with speed and precision. This ease of use directly fuels the surge in Axios activity.
Many other user agents lack Axios’s flexibility and ease of automation, leaving attackers to rely on more manual or less efficient methods. For example, user agents without robust automation capabilities make it harder to scale credential harvesting or execute workflows like MFA token interception. Attackers may have to write complex custom scripts or rely on tools that are easier for security teams to flag as suspicious. Additionally, the absence of Axios’s ability to mimic legitimate traffic patterns increases the chances of triggering anomaly detection systems, which monitor for unusual behavior in login workflows. These inefficiencies not only slow down an attacker’s operations but also increase the likelihood of detection, reducing the overall success rate of their campaigns.
The Organizational Blind Spot: Axios in Legitimate Traffic
Traditional defenses like user-agent analysis and reputation-based filters are failing against Axios-powered attacks, leaving organizations exposed. Tools like reputation-based filtering which flag potentially harmful activity based on the known reputation of an IP address, domain, or user agent, can struggle against Axios because of its prevalence in legitimate development environments, applications, or browsers.
Attackers use this blind spot to bypass MFA, hijack sessions tokens, and automate phishing workflows. Axios’s native promise-based workflows, error handling, and retry abilities simplify the process which makes large-scale campaigns easier to manage. The customizability offered by Axios lets attackers tailor their activity to further mimic legitimate workflows. Additionally, Axios’s forgiving nature gives attackers a significant advantage, as it lowers the technical barrier for sophisticated attacks.
The dangers Axios introduces are compounded by a lack of awareness. Many enterprises underestimate Axios’s role in attack chains, often dismissing it due to its association with legitimate development. As a result, Axios-powered phishing campaigns have become highly successful, with them being likely to continue to ramp up in pace and scale. Detections that rely heavily on user-agent analysis alone are insufficient against attackers using tools like Axios.
The Direct Send–Axios Pipeline: Bypassing Defenses at Scale
Direct Send is a Microsoft feature that email security tools typically trust by default, which makes it a key enabler for phishing attacks. Email security tools often rely on reputation-based filters that analyze IP addresses and domains to decide if the sender is trustworthy. Because Microsoft IP addresses are typically trusted, phishing emails sent via Direct Send can bypass these defenses, allowing attackers to impersonate internal users and deliver malicious content directly to inboxes.
Trusted Delivery + Automated Exploitation = Efficient Phishing
When paired with Axios, the threat from Direct Send abuse scales dramatically. Together, Direct Send and Axios form a highly efficient attack pipeline: Direct Send delivers phishing emails that appear legitimate, while Axios automates backend workflows like intercepting MFA tokens and authenticating stolen credentials. This seamless system allows attackers to operate at scale with minimal effort, blending into legitimate Axios traffic and evading detection.
The combination of Direct Send and Axios creates a highly effective phishing pipeline, which is highly likely to have played a key role in achieving the 70% success rate observed in the recent theft of credentials.
Why This Matters
Direct Send and Axios are making it easier and faster for attackers to conduct effective phishing campaigns, achieving unmatched success rates. With stolen credentials, attackers can infiltrate networks, escalate privileges, exfiltrate sensitive data, and compromise additional systems.
The QR Code Entry Point
Axios and Direct Send have also made it easier for attackers to integrate QR codes into phishing campaigns. In tracked campaigns, we saw malicious QR codes embedded into PDF attachments and paired with phishing emails with enticing subject lines like “payment,” “bonus,” and “payslip.”

Figure 1: Example of emails which were highly prevalent in observed Direct Send abuse and Axios exploitation campaigns (Source: X (Twitter))
Why QR codes? They exploit a key security blind spot: most email security tools don’t scan QR content as rigorously as URLs. Once scanned, QR codes redirect victims either to short, deceptive .es domains like ywnlzl.dwqewi[.]es and ooox.hrcbods[.]es, designed to look like legitimate Microsoft Outlook login portals or to Firebase-hosted apps that ride on Google’s trusted reputation to bypass defenses.
The disposable nature of this infrastructure is another key to its success. Short-lived domains and easily replicable Firebase links make it harder for defenders to blacklist and track the campaign’s footprint. Attackers can quickly abandon compromised assets and spin up new ones to stay ahead. This combination of QR codes, trusted hosting, and throwaway infrastructure makes these phishing campaigns fast, flexible, and harder to stop.
Why This Matters
Axios amplifies the impact of phishing campaigns by bridging the gap between initial access and full-scale exploitation. Its ability to manipulate authentication workflows and replay HTTP requests allows attackers to weaponize stolen credentials in ways that are both scalable and precise. This makes Axios integral to the rising success of Direct Send phishing campaigns, showing how attackers are evolving beyond traditional phishing tactics to exploit authentication systems and APIs at a level that traditional defenses are ill-equipped to handle.
Step Up Your Defenses Against Axios
ReliaQuest’s Approach
ReliaQuest’s detection rules are continuously updated using the latest relevant threat intelligence and research, which help organizations defend against the exploitation of tools like Axios, which increase attackers’ chances of success.
Organizations can significantly reduce their mean time to contain (MTTC) threats—from hours to just minutes—and minimize the threat of increasingly scaling phishing attacks by deploying these rules alongside these GreyMatter Automated Response Playbooks:
Block IP: This playbook can be used to cut off attacker infrastructure like the CIDR range 185.168.208[.]0/24 which has been observed in Direct Send abuse campaigns featuring Axios.
Reset Password: This playbook can be used to shut down an attacker’s next move. Resetting password for accounts that have had their credentials stolen can prevent automation-driven brute forcing and credential harvesting, mitigating systems from further exploitation.
Disable User: Disabling compromised accounts prevents attackers from using them to access systems, steal data, or move laterally within your network. This playbook can be key to stopping activity tied to Axios and Direct Send abuse.
Your Action Plan
The sharp rise in Direct Send abuse tied to the Axios user agent highlights the danger of relying solely on common defenses like MFA. When these measures are bypassed, detecting follow-on activity becomes critical. Missing this activity gives attackers time to increase their foothold, move laterally, and cause more damage. Acting quickly and decisively on suspicious activity is key to limiting the scale of an attack and minimizing its impact.
To secure your environment against the potential exploitation of the Axios user agent, we recommend the following actions:
Secure Direct Send: Disable Direct Send if not needed. If used, enforce stricter controls and route internal email activity through an email security gateway for threat inspection, such as scanning for malicious QR codes, URLs, or PDF attachments. Rejecting Direct Send can have downstream effects, though—see our recommendations below.
Anti-Spoofing Policies: Configure anti-spoofing policies on email gateways to block emails pretending to come from trusted sources.
Phishing Awareness: Train all users, including VIPs, to recognize phishing emails with deceptive subjects like (e.g., MEM0, 0VERDUE, INV0ICE) to reduce high-risk interactions.
Block Suspicious or Uncommon Top-Level Domains: Block uncommon top-level domains like .es, .ru unless required for business purposes.
Steps to Take Before Rejecting Direct Send
Rejecting Direct Send helps protect against unauthenticated, anonymous emails sent from your domain to your Exchange online tenant. But, if you’re unprepared, your organization will be unable to send emails from devices or systems that rely on unauthenticated mail connectors. Here are some steps to take to prevent email delivery failures.
Secure Communication Protocols: Ensure that all printers, email applications, and services use Simple Mail Transfer Protocol (SMTP) or an approved mail connector.
Restrict Third-Party Connectors: Configure third-party email connectors to permit emails only from trusted certificates or designated IP address ranges.
Prevent Anonymous Emails: Verify that no devices are set up to send anonymous SMTP emails, eliminating a common avenue for malicious activity.
Implement Authentication Protocols: Confirm that email authentication protocols, such as SPF, DKIM, and DMARC, are correctly configured and actively enforced. These protocols help validate sender identities and reduce the risk of spoofing and phishing attacks.
Key Takeaways and What’s Next
The success of Axios strongly suggests that increasingly streamlined and automated attack methodologies will continue to evolve and ramp up. This is likely to transform how attackers exploit APIs, as Axios accelerates the identification of API vulnerabilities, the scraping of sensitive data, and the bypassing of security mechanisms.
The Axios Effect: Automation and the Future of API Exploitation
CISOs need to adapt their security strategies to proactively defend against automated, multistage API attacks before they become widespread. It is highly likely that Axios will become a cornerstone of broader attack frameworks, automating multiple stages of the attack lifecycle, from reconnaissance to exploitation. This can lead to a dramatic increase in the frequency, scope, and sophistication of API-targeted attacks. For example, attackers could pair Axios with tools like Selenium, a customizable browser automation utility, to script advanced API scraping. They could also use Axios with new or existing frameworks to streamline API exploitation during post-exploitation phases. Attackers no longer need to rely on manual processes; instead, they will likely continue to use tools like Axios to turn API exploitation into a streamlined, easy, and scalable operation.
CISO Priority: Locking Down APIs Against Axios‑Powered Abuse
The growing threat from Axios—especially when paired with tools like OWASP ZAP or botnet frameworks—demands tighter API defenses. Attackers are using Axios to automate vulnerability scanning, bypass rate‑limits, and harvest sensitive data at scale. CISOs should:
Harden API controls with advanced rate‑limiting, strict input validation, and API‑specific anomaly detection.
Block abuse tactics such as IP spoofing used to evade throttling.
Enforce stronger authentication methods like OAuth 2.0 to protect access points.
Conduct proactive testing with dedicated API security tools to identify and fix vulnerabilities early.
IOCs
Artifact | Details |
185.168.208[.]63 | IP Address |
185.168.208[.]61 | IP Address |
185.168.208[.]62 | IP Address |
185.168.208[.]59 | IP Address |
185.168.208[.]55 | IP Address |
185.168.208[.]36 | IP Address |
185.168.208[.]60 | IP Address |
185.168.208[.]44 | IP Address |
178.130.47[.]216 | IP Address |
ywnlzl.dwqewi[.]es | Domain |
ooox.hrcbods[.]es | Domain |
cpewyx[.]es | Domain |
ogyhr[.]es | Domain |
bsfff[.]es | Domain |