2025 brought major shifts to the threat landscape, as nation-state actors refined their tradecraft and financially motivated groups exploited the expanding attack surface created by cloud adoption and remote work. From North Korean operatives infiltrating organizations as IT workers, to ransomware groups reverse-engineering security patches, adversaries demonstrated creativity and persistence that challenged traditional defenses.
The year also saw established groups like "Clop" and "Akira" continuing their campaigns against internet-facing enterprise platforms, while emerging collectives like "Scattered Lapsus$ Hunters" blended social engineering with large-scale data theft. These developments reveal how quickly threat actors adapt to new opportunities and why enterprises must move beyond reactive security postures.
In this blog, the ReliaQuest Threat Research team analyzes three critical predictions for 2026's threat landscape, offering practical defense strategies grounded in the lessons of 2025. The full report examines these predictions (and one more!) and provides comprehensive tactical guidance for building resilience against tomorrow's threats.
Weaponized AI: When Pen-Testing Tools Turn Against Defenders
Prediction: In 2026, cracked versions of AI-powered penetration testing tools will emerge on cybercriminal forums, enabling attackers to discover and exploit vulnerabilities at greater speed.
AI-powered pen-testing tools gained real traction in 2025, fundamentally changing how vulnerabilities are discovered and exploited. This rise can be attributed to the widespread availability of advanced AI technologies and the growing need to secure complex digital ecosystems faster and more effectively. The tools use advanced algorithms and scalable architectures to automate tasks traditionally performed by human testers, such as vulnerability discovery, exploitation, and attack simulation. These tools have proven their effectiveness—Xbow, for instance, dominated HackerOne's bug bounty leaderboard, outperforming human experts and discovering CVE-2025-27888.
Xbow on top of the HackerOne bug bounty leaderboards. (Source: HackerOne)
But cybercriminal forums tell a different story about what's coming. Posts recruiting developers to build AI pen-testing tools indicate clear demand. Yet history suggests a simpler path: Cobalt Strike became weaponized once cracked versions hit the dark web—this tool appeared in 50% of ReliaQuest customer incidents. AI pen-testing tools will likely follow the same trajectory.
We're already seeing the foundation. In 2025, threat actors sold deepfake creation services and "Blackhat ChatGPT"—a jailbroken AI model—on forums like "DarkNet Army." The monetization playbook is clear.
Once weaponized, these tools could obliterate traditional attack timelines—moving from initial access to ransomware deployment in minutes. Cracked AI tools will lower the barrier to entry, flooding the field with sophisticated attackers operating at machine speed.
We expect that in 2026, as cracked AI pen-testing tools proliferate, organizations failing to adopt AI-driven defenses will likely find themselves outpaced by attackers.
Maintainer Compromise: The Next Supply-Chain Attack Vector
Prediction: In 2026, we anticipate the emergence of specialized cybercriminal groups focused on exploiting open-source repository maintainers—the individuals responsible for managing and overseeing the development of open-source software projects.
Open-source software powers modern infrastructure, yet its foundation is fragile. Of 11.8 million open-source projects, 7 million are maintained by a single person. Nearly half of the 13,000 most-downloaded npm packages rely on one maintainer. This creates perfect conditions for exploitation: overworked volunteers lack security resources, and burnout erodes vigilance against spearphishing. We expect that in 2026, as specialized groups systematically target maintainers, supply-chain attacks will shift from opportunistic to industrialized.
For enterprises, the potential consequences of attacks could be costly:
Updates from compromised maintainers are often automatically trusted and pulled into a company’s CI/continuous delivery (CD) pipeline. | Once malicious code is in a trusted package, it can steal sensitive credentials from build servers, like cloud API keys and service tokens. | One compromised open-source library can impact hundreds of applications across an entire enterprise. |
This allows automated processes to freely deliver malware—whether it’s a sneaky crypto-miner slowing down your app or spyware stealing user data from browser sessions. | Credentials in hand, attackers can access customer data, sell credentials and credit card information on the dark web, and put users at risk of identity theft and fraud. | For end users, this means service disruptions, disabled features, and lost trust when they realize their data was exposed long before the breach was contained. |
The warning signs were loud and clear in September 2025. “Qix”, the maintainer of packages with 2 billion weekly downloads, fell victim to phishing despite having MFA protection enabled. Attackers published cryptocurrency-stealing malware across his repositories. That same month, PyPI maintainers received phishing emails from fake pypi[.]org domains, leading to thousands of poisoned packages. Meanwhile, the "Shai-Hulud" worm infected over 500 npm packages through fake collaboration invites.
Unlike initial access brokers who sell credentials, we predict that maintainer-focused groups will monetize the compromise itself—transforming stolen accounts into mass-distribution channels. One compromised maintainer becomes a platform for injecting malware into millions of applications simultaneously, generating revenue through data theft and extortion from a single control point.
The Noise Paradox: Competing Strategies in The Cybercriminal Environment
Prediction: In 2026, financially motivated threat actors will likely adopt sharply contrasting operational strategies. Emerging groups are likely to use bold, vocal, and often brash tactics as a high-risk, high-reward method to build their brand and attract affiliates. Meanwhile, the most successful and established groups will operate covertly to ensure long-term viability avoid law enforcement scrutiny.
We predict that emerging ransomware groups will increasingly adopt "weaponized noise" strategies to rapidly build credibility and recruit affiliates, while established operations maintain quiet persistence. We anticipate this bifurcation will create prioritization challenges for defenders, as attention-grabbing tactics obscure stealthier, more capable threats.
Throughout 2025, we observed distinct operational archetypes among financially motivated threat groups. "DragonForce" exemplified weaponized noise, reorganizing into a decentralized cartel while aggressively recruiting through forum advertisements and journalist engagement. The group defaced competitors' data-leak sites, claimed collaboration with established actors like "Qilin", and recruited "RansomHub" affiliates after that operation went offline. In Q1 2025, the group accounted for 26 victims, but by Q2, that number had more than doubled to 57.
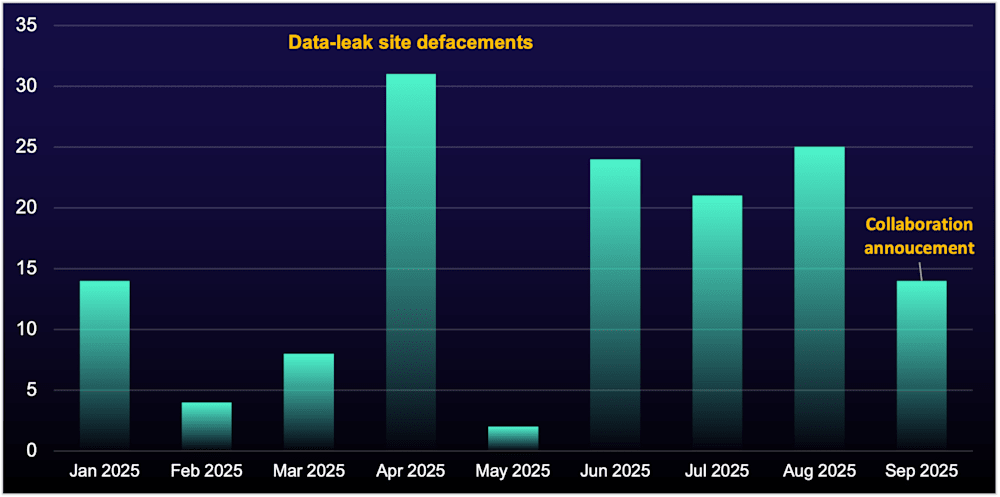
DragonForce's data-leak site volume in 2025 infographic chart
Meanwhile, the noise generated by "Scattered Lapsus$ Hunters" showed this strategy's risks. The group launched extortion-as-a-service platforms, maintained active social media presence, and publicized its Salesforce breach affecting 50+ organizations. Yet these brazen tactics drew swift law enforcement action—authorities seized its data-leak sites on both clear and dark web. While the short-term visibility attracted attention, sustainability proved elusive.
Meanwhile, established groups like Qilin and Akira—ranking first and second in Q2-Q3 2025 victim counts—operated silently. They avoided forum disputes, limited public engagement, and focused on operational security, recognizing that their impact already draws scrutiny.
We anticipate this divergence will intensify in 2026. Emerging groups will view weaponized noise as essential for rapid credibility-building in crowded markets, accepting law enforcement risks for immediate recruitment gains. However, this creates dangerous blind spots for defenders. Security teams will struggle with prioritization as headline-grabbing groups overshadow methodical actors. Resources will misalign toward reactive postures rather than addressing consistent TTPs that span both noisy and quiet operations.
We expect that in 2026, the attention economy of ransomware will force defenders to resist chasing headlines and instead focus on foundational TTPs that counter threats across the operational spectrum.


