ReliaQuest expands its GreyMatter Agentic Teammates with the release of its new AI persona, the Threat Hunting Teammate.
Your best threat hunters are exceptional at connecting the dots, understanding attacker behavior, and finding what shouldn't be there. Yet their potential is limited by time-consuming tasks: context-switching between tools, managing query languages, and writing reports—work that creates a barrier to effective threat hunting.
As threat actors increasingly leverage AI to accelerate the speed and complexity of attacks, you cannot afford inefficiency.
Make Your Strongest Threat Hunters Stronger With AI
Despite their talent, a manual threat hunting team struggles to validate security impact, drive improvement, and scale their security program. By leveraging agentic AI, your threat hunting team can scale your security program at the speed of your business.
What you need is your existing threat hunters to accomplish exponentially more, faster.
With the release of the GreyMatter Threat Hunting Teammate, ReliaQuest makes it possible for every analyst to hunt efficiently, faster, and with more precision.
Meet Your New Threat Hunting Teammate
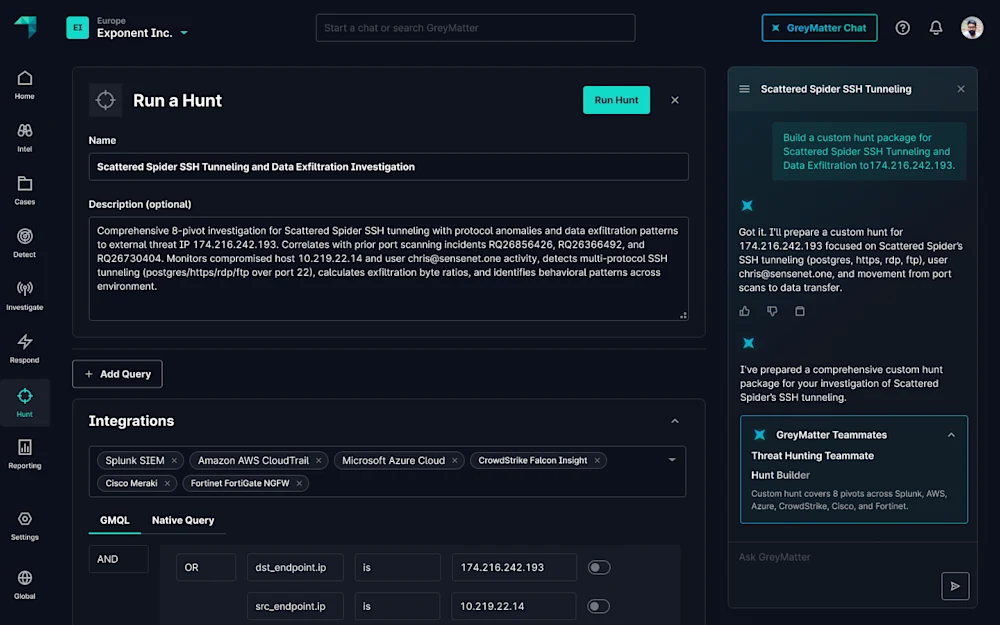
The GreyMatter Threat Hunting Teammate is an Agentic AI persona that empowers security teams to launch and analyze cross-telemetry hunts using threat intel to identify gaps and correlate trends, saving you time and multiplying your impact.
Create and Execute Hunts in Minutes with Agentic AI
Start the conversation with your Threat Hunting Teammate.
Speak to the Threat Hunting Teammate just as you would to a real colleague. For example, you could direct your Teammate to “dig deeper on this user’s activity in the past 7 days," or ask, "What are the emerging threats in healthcare that I should be hunting for?"
Regardless of how you phrase it, the Threat Hunting Teammate understands your intent, identifies available telemetry sources in your environment, and recommends an appropriate hunt package or builds a custom one tailored to your infrastructure.
Your recommendations adapt to your specific environment.
The Teammate prioritizes hunts based on your industry, your environment, and the current threat landscape, then adjusts recommendations as it learns from the results of previous hunts.
Hunt results are automatically analyzed and summarized.
The platform identifies patterns and anomalies, assesses severity, contextualizes findings with the MITRE ATT&CK framework based on the hunt package used, and recommends next steps for investigation or remediation. Teams receive actionable findings instead of raw log volumes.
Specialized agents work together through a multi-agentic architecture.
The Threat Hunting Teammate orchestrates specialized skill agents with SQL execution, data analysis, and time series analysis capabilities to collaboratively execute complex hunts. The system connects with your Detection Engineering and Threat Intel Research Teammates to surface findings and inform broader security operations in real time.
Threat Hunting Teammate in Action: Hunting Scattered Spider
A security team receives intelligence about Scattered Spider activity targeting their industry. Instead of manually building queries across multiple tools over days, the human analyst tasks the Threat Hunting Teammate to:
Build a custom hunt package aligned to Scattered Spider tactics, techniques, and procedures, mapped to the available telemetry.
Execute a hunt that produces millions of logs and events with automatically analyzed results.
Identify the findings: ten exposures, with 3 SaaS applications showing unauthorized access patterns.
Report to the CISO with an executive summary: findings are contextualized within the MITRE ATT&CK framework based on the Scattered Spider hunt package, with recommended investigation and remediation steps.
What would have taken weeks of manual correlation was completed in hours. The team moved from hunting blind to hunting with precision.
Key Benefits
The Threat Hunting Teammate helps SOC teams to:
Hunt efficiently: Accelerate hunting with conversational workflows and built-in expertise.
Stay precise: Contextualize every hunt to your geography, industry, telemetry, and threat intelligence.
Respond faster: Automate hunt analysis and quickly move from findings to response.
One Hunt Cascades Across Your Team
The Threat Hunting Teammate works together with a collaborative team of AI personas—each specialized in intelligence, hunting, and detection.
The GreyMatter Agentic Teammates, a team of role-based AI personas built with 15 years of frontline security operations experience, collaborate with each other and your analysts to shift your team toward predictive security operations.
When the Threat Hunting Teammate discovers suspicious activity, Threat Intel enriches findings with personalized, actionable intelligence. The Detection Engineering Teammate builds and validates new rules to catch similar activity. This integration transforms a single hunt into organization-wide improvement, with each finding strengthening the entire security program.