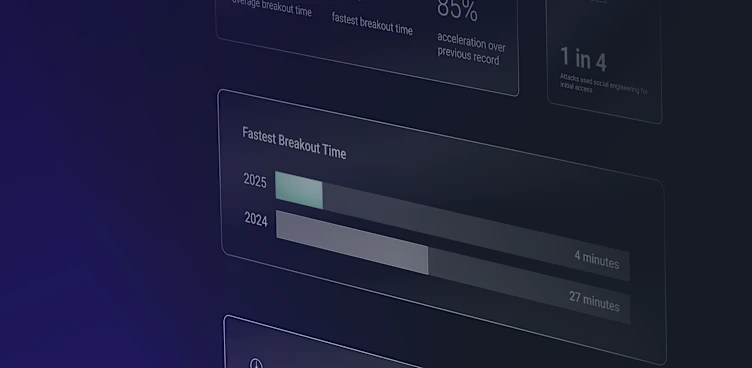
The first quarter of 2023 (January 1 to March 31) set a dangerous precedent. Q1 2023 was the most prolific our ReliaQuest Threat Research Team has ever observed in terms of double-extortion ransomware. More victims were named on data-leak sites than in any other quarter to date. There’s no denying that ransomware activity is a steadily growing threat.
Ransomware operators rely on consistent, robust ways to enable command and control (C2) so they can communicate with compromised devices on a targeted network. The most popular C2 framework? Hands down, it’s Cobalt Strike. The popularity of legitimate penetration-testing tool Cobalt Strike probably stems from a perfect blend of effectiveness and user-friendliness. Let’s examine how this benign-by-design tool has been weaponized during 2023.
C2 and Cobalt Strike: Partners in Crime
Attackers often rely heavily on C2 communications to start and progress attacks, including human-operated ransomware attacks. C2 infrastructure empowers them to control infected devices, perform malicious activity, and quickly adapt to a targeted organization’s environment in pursuit of valuable data and assets.
Breaking this link to C2 infrastructure disrupts attacks—it either stops the communication completely or delays its progression, allowing more time for investigation and remediation. By default, Cobalt Strike enables payload staging via a valid checksum8 request (a checksum being the process of checking a file’s integrity). The Cobalt Strike team server then returns a shellcode payload. From that, security researchers can extract the payload’s configuration, uncovering a bounty of details about how the implant operates, including the C2 address, the C2 port, the spawn-to process, and the license ID.
Researchers have meticulously detailed the default configurations of team servers. By searching for unique values in the HTTP response headers, JARM signatures, and default certificates, and using network scan data services like Shodan, ReliaQuest can profile potential Cobalt Strike team servers. That gives our security team the power to proactively monitor customer environments for communication with these indicators.
Team Server Use: Running the Numbers
Our data reflects covers Cobalt Strike team server activity from February 1, 2022, to February 1, 2023. The vast majority of the servers we identified were hosted on infrastructure located in China, followed by the US and Hong Kong (see Table 1). No surprise there—given the number of large legitimate hosting providers in the US and China, as seen in the breakdown of top autonomous system numbers. (In case you missed it, an autonomous system is a large network or group of networks that have a single routing policy, and each system is assigned a unique number, or ASN, to identify it, which is typically owned and operated by a single service provider.)
Threat actors have shown an affinity for using legitimate hosting providers as it helps them blend in with legitimate traffic.
Table 1: Number of Cobalt Strike team servers, by host country
Country | Servers Hosted |
China | 4,830 |
US | 3,176 |
Hong Kong | 781 |
Russia | 325 |
Singapore | 176 |
Lithuania | 175 |
Romania | 150 |
UK | 128 |
Netherlands | 122 |
Germany | 114 |
Take a look at Table 2 for a breakdown of ASNs: Several well-known cloud hosting providers sit at the top of the list.
Table 2: Number of Cobalt Strike team servers, by ASN
ASN | Count |
45090 – TENCENT-NET-AP Shenzhen Tencent Computer Systems Company Limited, CN | 2,695 |
37963 – ALIBABA-CN-NET Hangzhou Alibaba Advertising Co.,Ltd., CN | 1,136 |
14061 – DIGITALOCEAN-ASN, US | 674 |
20473 – AS-CHOOPA, US | 390 |
16509 – AMAZON-02, US | 373 |
8075 – MICROSOFT-CORP-MSN-AS-BLOCK, US | 203 |
14618 – AMAZON-AES, US | 190 |
55990 – HWCSNET Huawei Cloud Service data center, CN | 181 |
132203 – TENCENT-NET-AP-CN Tencent Building, Kejizhongyi Avenue, CN | 177 |
134548 – DXTL-HK DXTL Tseung Kwan O Service, HK | 164 |
The most common C2 ports can be seen in Table 3; the default ports for HTTP and HTTPS (80 and 443) were the most commonly used for communication.
Table 3: Most commonly used C2 ports, by number of instances
C2 Port | Count |
443 | 4,892 |
80 | 3,829 |
8080 | 675 |
8443 | 541 |
8090 | 271 |
8888 | 247 |
8081 | 183 |
9999 | 177 |
4444 | 172 |
8088 | 167 |
Of the beacon payloads recorded, most were configured with an IP address for the C2. The C2 address is often the same as the team server address. For beacons that used a domain for C2, most used content delivery networks, such as provided by Tencent, CloudFront, and Azure. These services help beaconing blend in with legitimate traffic.
Table 4: Most commonly used registrars, by number of uses
Registrar | Count |
NAMECHEAP, INC. | 353 |
ENAME TECHNOLOGY CO.,LTD. | 330 |
MARKMONITOR, INC. | 295 |
GODADDY.COM, LLC | 247 |
OWNREGISTRAR, INC. | 171 |
NICENIC INTERNATIONAL GROUP CO., LIMITED | 122 |
GANDI SAS | 103 |
NAMESILO, LLC | 99 |
HOSTING CONCEPTS B.V. D/B/A REGISTRAR.EU | 95 |
AMAZON REGISTRAR, INC. | 86 |
Notice the high number of C2 domains registered with reputable registrars, like Ename Technology and MarkMonitor, in Table 4? That’s primarily explained by the heavy use of legitimate CDN services (Tencentcs, Cloudfront, Azure). These services assist threat actors via domain fronting: C2 traffic is routed through a legitimate CDN to hide attacker-owned infrastructure. Domain fronting conceals user traffic and threat actors often use it for C2 purposes.
Our data revealed the most commonly used “spawn-to” processes: temporary processes spawned by the Cobalt Strike implant, which are used to inject code that carries out post-exploitation commands. Each beacon configuration lists a spawn-to process for x86 and x64 architecture, but the process selected is typically the same for both. The default spawn-to process is rundll32.exe. Because that process runs without any command-line arguments, an effective detection opportunity arises. Many of the top spawn-to processes listed in Tables 5 and 6 are also rarely executed without command-line arguments.
Table 5: Most commonly used spawn-to processes (x64), by number of uses
Spawn to x64 | Count |
%windir%\sysnative\rundll32.exe | 8,087 |
%windir%\sysnative\dllhost.exe | 1,342 |
%windir%\sysnative\gpupdate.exe | 232 |
%windir%\sysnative\svchost.exe | 195 |
%windir%\sysnative\WUAUCLT.exe | 185 |
%windir%\sysnative\runonce.exe | 184 |
%windir%\sysnative\regsvr32.exe | 149 |
%windir%\sysnative\WerFault.exe | 105 |
%windir%\sysnative\WerFault -a | 73 |
Table 6: Most commonly used spawn-to processes (x86), by number of uses
Spawn to x86 | Count |
%windir%\syswow64\rundll32.exe | 8,087 |
%windir%\syswow64\dllhost.exe | 1,342 |
%windir%\syswow64\gpupdate.exe | 233 |
%windir%\syswow64\svchost.exe | 196 |
%windir%\syswow64\runonce.exe | 184 |
%windir%\syswow64\WUAUCLT.exe | 173 |
%windir%\syswow64\regsvr32.exe | 150 |
%windir%\syswow64\WerFault.exe | 106 |
%windir%\syswow64\WerFault -a | 75 |
%windir%\syswow64\choice.exe | 45 |
Best Defense: Combatting Cobalt Strike Abuse
At ReliaQuest, we continuously profile team servers in the wild, identifying payloads to extract configuration details. The indicators of compromise collated through this process are fed into , which means they can be used an emergency feed and trigger alerts. The end result? We can offer significant coverage of active Cobalt Strike C2 servers, and our customers can take appropriate steps to block Cobalt Strike infrastructure.
For extra defense, offers coverage to detect behaviors linked to many of the capabilities of Cobalt Strike. And the following steps should also help mitigate Cobalt Strike abuse.