What is Security Operations?
Businesses and organizations follow security operations to ensure security of their digital assets.

What is Security Operations?
Security operations (SecOps) is a combination of the information security and IT departments in a business working together to detect, contain, and recover from cyber security incidents.


What is a Security Operations Center (SOC)?
A security operations center (SOC) is the security operations team and the actual facility that’s dedicated to detecting and resolving security incidents. A properly run SOC can mean the difference between being safe and becoming a headline.
A security operations center acts as the central security hub for an organization – incorporating telemetry from across the ecosystem and making the final decision regarding how to respond to threats. SOCs initially were a room full of analysts who secured an organization’s digital assets that were primarily on-premises. The “room” has now expanded to include a team of experts, working anywhere, who secure an expanded ecosystem; on-premise, remote or in the cloud.

How Does Security Operations Work?
The security operations workflow
The security operations workflow is the lifecycle of a security event and the order of operations the SOC must take to address that event. There are typically five steps:
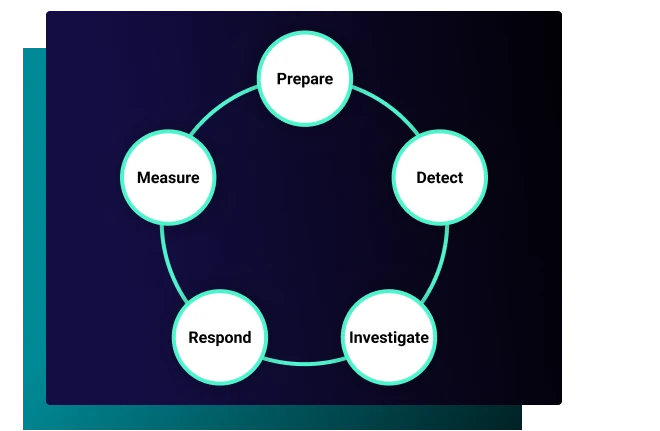


Prepare
Preparation involves ensuring tools, resources, and technologies are available to support the detection, investigation and response process. This includes network monitoring systems, intrusion detection software, anti-malware solutions, and forensic analysis tools.
Regularly practicing and refining incident response procedures through tabletop exercises and other training sessions can help members of a SOC or IR team to be prepared to act quickly to threats.
Detect
Detection could be considered the foundation of a security operations workflow; identifying potential or actual security incidents within an organization’s systems and networks. Without detection, an organization cannot take action against threat actors compromising its data or systems. The detection process involves various layers such as network monitoring, log analysis, threat intelligence, anomaly detection, and many more to identify potential threats.
Investigate
Security alerts are generated by various tools detecting suspicious activity in an organization’s security environment. Investigating alerts confirms if a threat is taking place and assess its severity, impact, and root cause. A security analyst determines the extent of the compromise, how it happened, what data has been impacted, and who was responsible for the incident. The investigation process involves analyzing logs, examining network traffic, interviewing employees, reviewing system configurations, and many other measures.
Respond
An incident response plan provides a structured approach for responding to threats. A good incident response plan should identify potential threats and vulnerabilities, establish procedures for response, and provide guidelines for escalation or invoking backup services.
Remediation typically involves taking action to eliminate the threat and restore business operations. This may include patching vulnerabilities, removing malware, restoring backups, improving security controls, and more.
Measure
Measuring the effectiveness of an organization’s security operations is essential to determines the level of maturity, your security posture and if your organization is making data informed decisions. and identify areas for improvement.
Here are some key metrics:
Mean Time to Detect (MTTD): the time it takes for the security team to detect a security incident.
Mean Time to Respond (MTTR): the time it takes for the security team to respond to and mitigate the impact of a security incident.
False Positive Rate: the frequency at which security alerts are generated incorrectly.
Number of Incidents: The number of incidents detected over a given period of time.
Vulnerability Management Effectiveness: the time between identifying a vulnerability and applying the patch or mitigation measures, number of vulnerabilities identified, and the severity of identified vulnerabilities.
Training and Awareness: tracking the completion of security trainings, phishing simulation outcomes, and employee risk awareness.
Security Operations Challenges
Here are five common challenges inherent in building an efficient security operations:


1. Changing business landscape
A remote work environment introduces many BYOD devices. That, coupled with the explosion of new apps, services, and employees online, creates myriad opportunities for phishing and credential stuffing attacks. Monitoring for user behavior that is outside the norm will help catch this.
2. Lack of singular visibility
Organizations combat this modern network sprawl by investing in more tools – that don’t integrate well with each other. And they can be so time-consuming to operate that analysts can spend more time learning, managing, and troubleshooting them than responding to security alerts.
3. Inability to continuously optimize tools
We’re in the middle of a cyber talent shortage, and as companies are moving to new architectures and cloud-based modules, the need for more training (and more hands on deck) has increased beyond the capacity of many to keep up.
4. Too many manual tasks and processes
What can really exacerbate this problem is organizations still doing so many tasks by hand, many repetitive. With an increasingly complex environment, it is impossible for analysts to keep up, leading to inconsistencies, errors, and headlines.
5. Lack of actionable metrics
A business may have invested in the tools they need, but have difficulty measuring their effectiveness. As security teams rush to put out fires and implement solutions, tracking the measurements of success can get lost in the shuffle, leading to tool-sprawl, shelf-ware, and directionless security strategy. Typical metrics include things like number of alerts, while more useful, actionable metrics like total ecosystem coverage are left out.
The Life of A SOC Analyst
One type of individual contributor who works in the SOC is called a SOC analyst. A SOC analyst is part of a team of like-minded experts that monitor, discover, respond to and mitigate cybersecurity threats within an organization. The role has a watchdog element, and they’re often the first boots on the ground when a cyber incident occurs – day or night. It may get busy, but it’s never boring.
SOC analysts can be divided further into ranks based on experience, and tasks range from entry-level threat analysis to higher-level escalated events like breach control and mitigation. Some basic skills an analyst needs to have are:


Network Defense
This includes monitoring alerts and analyzing trends.
Ethical Hacking
Penetration testing your network to ensure the security of your defenses.
Incident Response
Dealing with the fallout of a cyberattack – reporting it, investigating it, and mitigating the damage caused.
Computer Forensics
Backtracking what happened in an attack by recreating it with data pulled from the event.
Reverse-Engineering
“Acting out” the breach to find what the attacker did to compromise the system.


What is SOC-As-A-Service
Managed SOC, or SOC-as-a-Service (SOCaaS), is a type of managed security service where you outsource your security operations center to a third party on a subscription basis. This can be an entire takeover or a partial addition to your team to force-multiply your current capabilities. The benefits of using SOC-as-a-Service include:
How to Improve Your Security Operations
There are plenty of models and best practices for running a SOC, but how do you know if you’re doing it right? Your SOC should go beyond the basic capabilities and utilize today’s technology to its fullest, taking strain off your team. Here are some key attributes of a best-in-class SOC:


Singular, actionable visibility
Successful incident response requires complete visibility across the ecosystem – on-premises and cloud – so there are no blind spots. Furthermore, it is vital to have visibility into cyber risk coverage so analysts can plan how to close any gaps.
Track metrics that matter
Communicate the measurements that matter to improve security posture and close any communication gap with the business.
Consistency
A major failing of security operations today is ad-hoc or inconsistent processes. A well-managed security operations org should codify best practices. That way, work gets done more efficiently, with fewer errors, and with less unnecessary human involvement.
Automation, AI, and machine learning
Ponemon research reveals that only 13% of incidents are contained within a month. Given the high volume of alerts security experts are faced with daily, it’s no wonder. Leveraging automation and AI across the security lifecycle helps sift through mundane security tasks, prioritize events, enrich investigations to reduce noise, and drive faster actions.
Unified workbench
Find a platform that integrates your existing tools and unifies detection, investigation, and response capabilities to show the full picture on a single screen – driving faster and easier decision making.
Proactive operations that drive resilience
Prevention is better than the cure. A best-in-class solution includes threat hunting, breach simulations, health monitoring, and a continuous feedback loop so your posture is constantly being evaluated and improved.

GreyMatter: A Security Operations Platform from ReliaQuest
ReliaQuest delivers successful security outcomes by force-multiplying an organization’s security operations team. It uniquely combines the power of technology and security expertise to make security possible for organizations by increasing visibility, reducing complexity, and managing risk.
ReliaQuest GreyMatter is a cloud-native security operations platform that is delivered as a service any time of the day, any place in the world. Built on an Open XDR architecture, it offers bi-directional integration across any vendor solution, whether on-premises or in one or multiple clouds, to ingest data and automate actions. It brings together telemetry from any security and business solution to deliver singular visibility across the enterprise ecosystem and unifies detection, investigation, and response to drive security effectiveness and cyber resilience.


