
Read The Case StudyWith GreyMatter, my team doesn’t have to do a lot of chair swiveling; we can see everything happening on one platform, which has enabled us to quickly identify and respond to threats.Christine VanderpoolCISO, Florida Crystals
Win Against Attackers with Automation & AI
Attackers use automation to breach networks in just 27 minutes, while manual SecOps responses lag behind at 8 hours—a dangerous speed gap that puts organizations at risk. This guide reveals how leading SecOps teams are using automation and Agentic AI to:

Cybercriminals are outsmarting typical defenses faster than ever. Accelerate response with an automation-driven security operations platform powered by agentic AI.


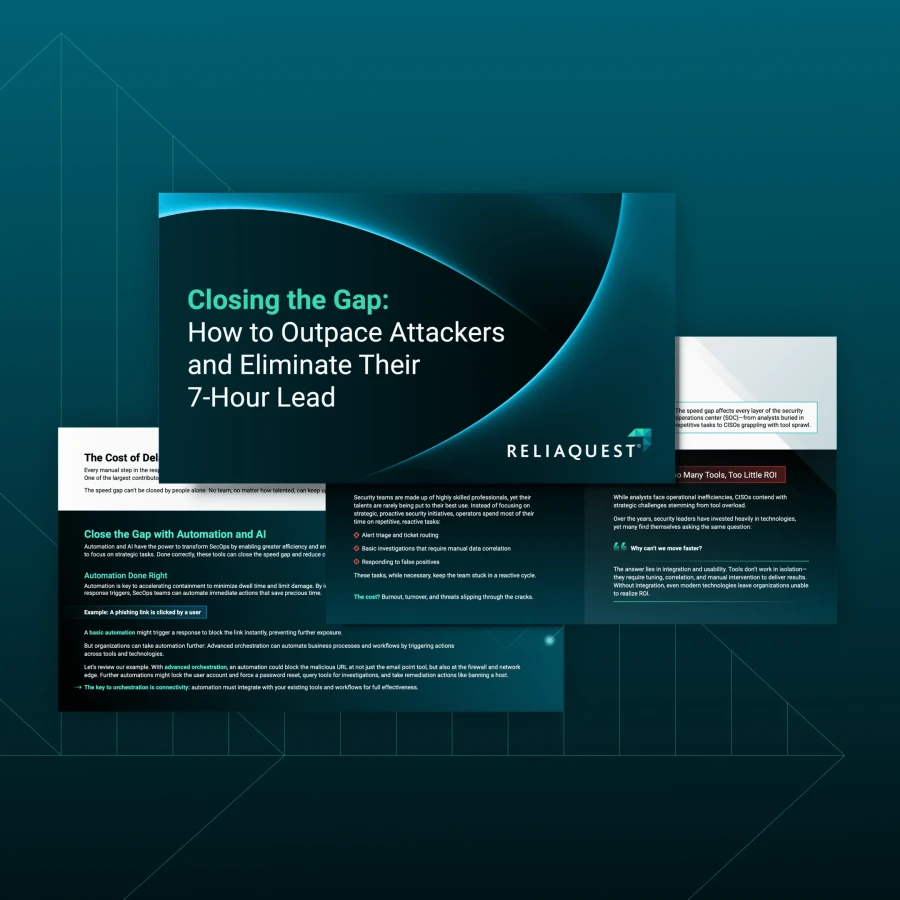
When lateral movement happens in under 30 minutes, an hours-long containment time isn’t good enough. Contain threats in under 5 minutes and stop attackers in their tracks with GreyMatter automation.
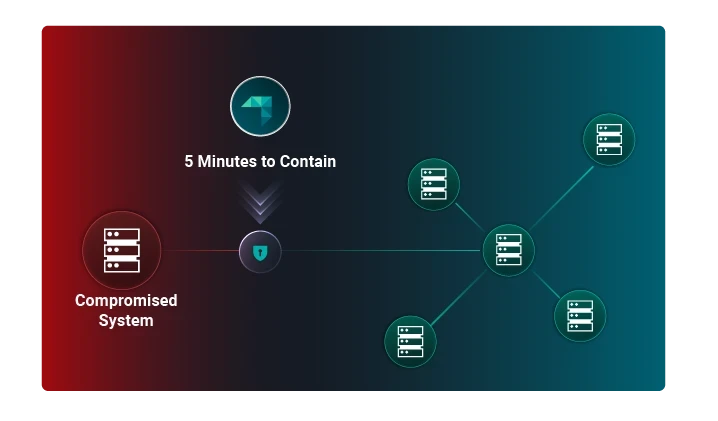
Attackers gain footholds in your environment while your team is stuck pulling alert artifacts. Take the mindless Tier 1 and Tier 2 tasks off their plate with AI so they can focus on proactive security.
Build and automate no-code workflows within GreyMatter for smooth execution every time. Keep your team coordinated to tackle threats with precision and speed.
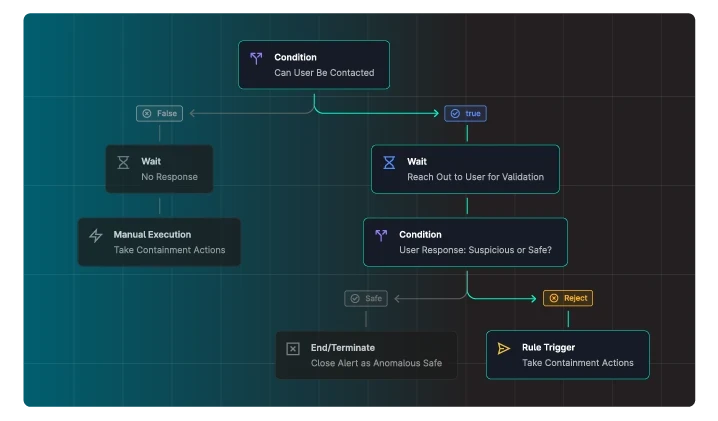

Seamlessly integrate GreyMatter into your existing security operations tech stack to enhance visibility across your tools and gain the context and insights you need to operationalize security and protect your business.
See Integrations