Key Findings

First observed in March 2024, “BlackLock” (aka El Dorado or Eldorado) has rapidly emerged as a major player in the ransomware-as-a-service (RaaS) ecosystem. By Q4 2024, it ranked as the 7th most prolific ransomware group on data-leak sites, fueled by a staggering 1,425% increase in activity from Q3. BlackLock uses a double extortion tactic—encrypting data while stealing sensitive information—to pressure victims with the threat of public exposure. Its ransomware is built to target Windows, VMWare ESXi, and Linux environments, though the Linux variant offers fewer features than its Windows counterpart.
BlackLock’s rise has been both swift and strategic, targeting organizations across a wide range of sectors and geographies. If its current trajectory continues, we predict it could claim the top spot as the most active ransomware group in 2025.
To understand what’s driving BlackLock’s rise, we took a deep dive into its activity on cybercriminal forums, communication methods, and infrastructure. This report reveals the features that set BlackLock apart in the highly competitive and ever-evolving ransomware landscape, focusing on:
Unusual features of BlackLock’s ransomware variant and data-leak site that give it a competitive edge
BlackLock’s hands-on strategy on the ransomware-focused Russian-language forum RAMP
How BlackLock’s forum activity correlates with subsequent waves of attacks
The group’s likely pivot toward targeting Entra Connect
Read on to learn more about these key differentiators, how BlackLock’s strategies threaten organizations worldwide, and what you can do to stay ahead of this rising ransomware powerhouse.
Infrastructure Built for Dominance: Unconventional Data-Leak Site and Bespoke Malware
Custom-Built Malware
Competitor ransomware groups like “Bl00dy,” “Dragonforce,” and “RA World” rely on leaked “Babuk” or “LockBit” builders to launch attacks. BlackLock, however, stands apart by developing its own custom malware —a hallmark of top-tier groups like “Play” and “Qilin.”
While leaked ransomware builders are easy to use, they come with a major drawback: Security researchers can access and dissect the code, find weaknesses, and develop defenses against them. In contrast, BlackLock’s custom malware keeps researchers in the dark—at least until its source code is leaked.
At first glance, BlackLock’s advertisements on ransomware forums may seem similar to other big players, boasting multi-platform support and advanced encryption. However, its high volume of posts on its leak site in 2024 demonstrates its superior effectiveness.
Unusual Data-Leak Site
A closer look at BlackLock’s data-leak site revealed unique tricks aimed at blocking researchers and organizations from downloading stolen data. Unlike most other leak sites, BlackLock’s platform is packed with features likely designed to prevent targeted organizations from assessing the scope of their breaches. This, in turn, ramps up pressure on the organizations to quickly pay ransoms, often before they can fully evaluate the situation. These features also highlight BlackLock’s technical sophistication, reinforcing its reputation as a polished, professional operation.
Here’s what we encountered during our investigation of the site and how we overcame its challenges:
Query Detection
Observation: BlackLock’s leak site would stop sending responses when GET requests to extract folder names were sent too quickly.
Solution: By limiting requests to one every second, we bypassed this restriction and successfully extracted the folder names needed to analyze the impact on named victims.
Bogus File Responses
Observation: When automated or frequent download attempts were detected, BlackLock’s site would respond with empty files containing only contact information—a technique we’d never seen before. This perplexing tactic was likely designed to frustrate investigators, forcing them to manually download files one by one—a time-consuming and labor-intensive process.
Solution: By randomizing download intervals (2–5 seconds), using unique browser agents, and rotating session IDs for each request, our teams successfully automated file downloads.
Overcoming these roadblocks demonstrated the critical role of hands-on research in tackling advanced ransomware groups, especially as attacker techniques grow increasingly sophisticated and innovative. BlackLock’s unusual tactics further showed the lengths it goes to protect its operations and turn up the heat on its victims.
BlackLock’s Web of Associates on RAMP
Our Threat Research team also analyzed the interactions of user “$$$,” BlackLock’s representative on RAMP forum. This analysis revealed how BlackLock builds relationships with other users, establishes trust, and secures resources to fuel its ransomware activities. The most notable observation was the sheer volume of activity on BlackLock’s RAMP account. Although many RaaS operators use the forum to recruit affiliates, BlackLock’s account is far more active, with 9x more posts than “RansomHub’s” operator as of January 2025.
The table below shows the comparable engagement of other RaaS representatives.
Forum Activities | BlackLock | Lynx | RansomHub | Dragonforce |
Total Posts | 307 | 7 | 35 | 8 |
Creates Multiple Threads | ||||
Engages in Other Forum Sections | ||||
Advertises to Affiliates | ||||
Attempts to Recruit Developers | ||||
Engages with IABs |
Through this increased engagement, $$$ has built a reputation that surpasses their rivals, allowing them to efficiently recruit initial access brokers (IABs), affiliates, and technical specialists to boost BlackLock’s operations.
We also observed that $$$ carefully tailors their interactions based on the user they’re communicating with—whether it’s programmers, IABs, or other ransomware operators. Depending on the user, $$$ varies the tone of their messages and how much information they give away. $$$’s interactions broadly consist of:
Inner circle: Users who have likely worked directly with $$$. We identified these users through posts requesting off-platform contact (e.g., via Tox) or instances where others mentioned previous collaborations.
Outer circle: Users who’ve had positive but inconclusive interactions with $$$, such as supporting $$$ in disputes or responding to malware inquiries without confirmed purchases.
Expanding the Team with Traffers and Programmers
BlackLock actively recruits key players, known as traffers, to support the early stages of ransomware attacks. These individuals drive malicious traffic, steer victims to harmful content, and help establish initial access for campaigns. Recruitment posts for traffers explicitly outline requirements, signaling BlackLock’s urgency to bring on candidates quickly—often prioritizing speed over operational security.
In contrast, posts seeking higher-level developer and programmer roles are far more discreet, with details and resumes shared privately instead. These roles likely involve greater trust, higher compensation, and long-term commitment, making the recruitment process more delicate.
Case Study: In Figure 1, $$$ seeks traffers who have “all their own tools” and offers to cover expenses and share profits. The post ends, “P.S. the primary goal is, of course, networks and ransom.”
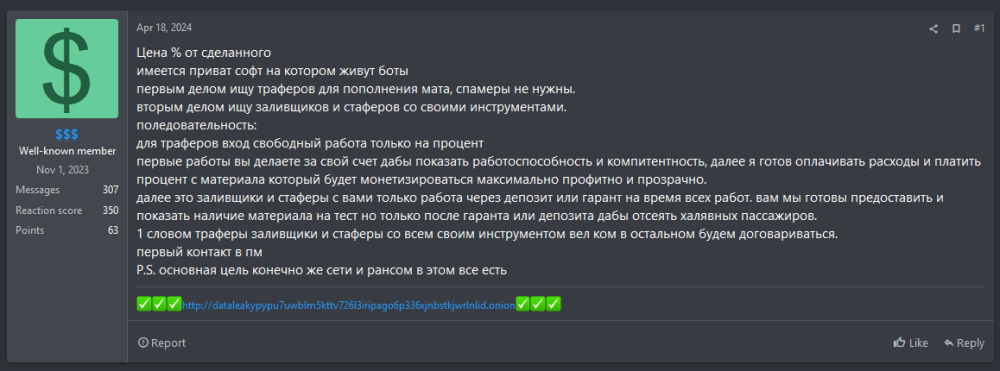
Figure 1: Forum post by user $$$ seeking traffers, offering expense coverage and a share of profits
Most RaaS operators delegate these early-stage tasks to affiliates, but BlackLock’s decision to take control reflects an aggressive strategy that likely fueled its rapid rise in 2024.
IAB Communications Predict Attack Waves
Working with trusted IABs speeds up attacks for affiliates or ransomware operators by eliminating the need to spend time gaining access to target systems. $$$’s frequent engagement with IAB posts on RAMP means it’s realistically possible that BlackLock sometimes compromises systems directly, bypassing the use of affiliates altogether.
Case Study: Figure 2 shows $$$’s response to IAB “guccigan,” who offers domain admin access in Tier 1 countries (e.g., the US). $$$ asks, “so you can get around Sentinel One?” and then “likes” guccigan’s affirmative reply
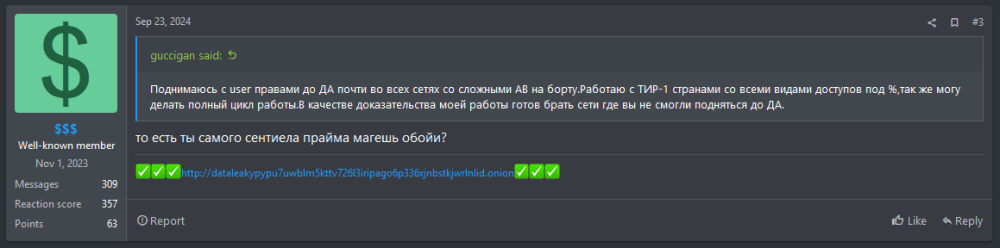
Figure 2: $$$ responds to IAB’s RAMP post offering domain level-accesses, asking whether they can bypass Sentinel One
In this incident, $$$’s interaction with guccigan took place just weeks before BlackLock’s major attack waves in October and November 2024, which included multiple US targets. This timing means it’s realistically possible BlackLock used guccigan to gain accesses before its name-making campaign, enabling faster and more coordinated attacks.
Affiliate Recruitment Aligns with Major Attack Campaigns
Case Study: On November 7, 2024, $$$ advertised a “pre-New Year holiday opportunity to earn in the ransomware field with a reliable and trusted company,” asking interested parties to send their contact details privately. This cautious approach likely helps protect both affiliate and target identities, leaving victims unaware and unable to harden defenses. Two days later, as shown in Figure 3, $$$ closed the thread with the message: “The campaign is over. People have been found. Thank you and good luck.”
Notably, affiliate recruitment posts like this often precede major attack waves, suggesting a link between the timing of these posts and BlackLock’s operations.
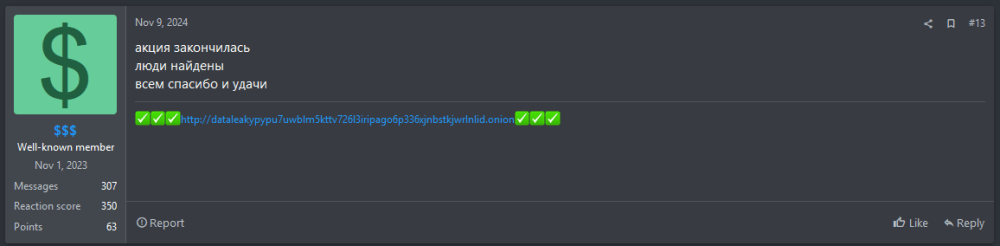
Figure 3: $$$ post confirms “campaign is over,” as recruitment efforts had concluded
The timing of these recruitment posts coincides with two of BlackLock’s four major attack waves.
May 31, 2024: $$$ posted looking for “pentesters,” which preceded BlackLock publishing 16 data-leak site posts in June—23% of its 2024 total.
November 2024: A recruitment push earlier in this month foreshadowed 10 data-leak site posts between November 18 and December 18, 2024—15% of the year’s total.
Collaboration or Competition? BlackLock and its Rivals
BlackLock’s interactions with competing ransomware and malware operators suggest a degree of collaboration. $$$ has shown positive engagement with users associated with Dragonforce and Lynx ransomware, as well as interest in testing or buying tools from other RaaS groups and malware sellers.
In Figure 4, $$$ defends “Silencer” (from Lynx ransomware) after another user criticized their post. $$$ responded directly to Silencer, stating: “you’re my competitor, but I’m happy to welcome you to the market with kind words. I wish you success in your work.”
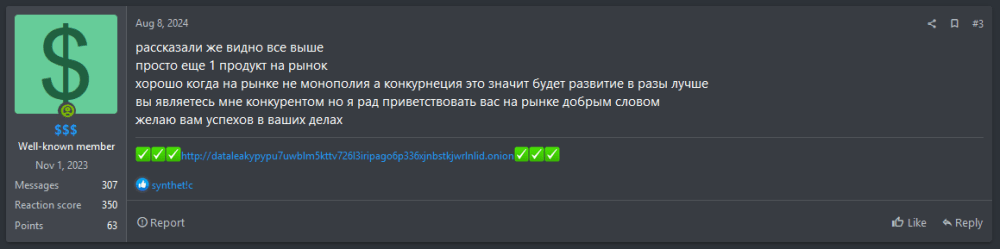
Figure 4: $$$ responds to criticism of ransomware rival, Silencer, in post offering encouragement and well-wishes
Collaborating with other ransomware or malware operators, including to test tools, allows BlackLock to compare and potentially incorporate useful features into its operations. Monitoring these interactions could provide early indicators of BlackLock’s malware evolution, allowing for proactive defense strategies.
Step Up Your Defense Against BlackLock
How ReliaQuest Helps You Stay Ahead
Threat Intelligence: ReliaQuest actively tracks BlackLock’s operations to refine threat profiles and deliver tailored intelligence to organizations. By monitoring BlackLock’s data-leak site and forum activity and updating IOCs, we provide actionable insights to identify BlackLock’s targeting patterns and strengthen defenses. This intelligence directly informs threat models and response plans, helping organizations anticipate BlackLock’s next moves and implement proactive countermeasures.
Incident Response: As an extension of our customers’ teams, ReliaQuest provides expert support during active incidents. From analyzing BlackLock’s operational footprint to investigating potential data exposures, we deliver actionable insights rooted in primary source intelligence. Our analysts work closely with customer teams to contain threats and provide tailored risk mitigation strategies—ensuring businesses can recover quickly and effectively.
Detection Rules: ReliaQuest monitors for changes in BlackLock’s tactics, techniques, and procedures (TTPs) to refine detection rules and spot group-specific behaviors. Key techniques we monitor include ESXi account compromise, shadow copy deletion, and pass-the-hash (PtH) attacks—core methods BlackLock uses to infiltrate systems and encrypt data. By constantly fine-tuning these rules, we ensure timely detection of incidents, helping organizations stay ahead of BlackLock.
Detection Rule | MITRE ATT&CK ID | Summary |
Anomalous Logon of VMWare ESXi Service Account | TA0005: T1708.001 – Default Accounts TA0003: T1078.001 – Default Accounts TA0001: T1078.001 – Default Accounts TA0004: T1078.001 – Default Accounts | This rule detects potential compromise of the highly privileged ESXi service account “vpxuser” by flagging suspicious authentications via user agents other than VMware-client/X.X.X or VMKernel—behavior consistent with BlackLock campaigns targeting ESXi hosts. |
Shadow Copies Deleted | TA0005: T1070.004 – File Deletion TA0040: T1490 – Inhibit System Recovery TA0002: T1059.003 – Windows Command Shell | BlackLock’s ransomware deletes shadow copies through the Windows command line to prevent recovery and force ransom payments. This rule detects such deletions, a tactic to disable backup restoration. |
Pass-the-Hash Attack | TA0005: 1500.002 – Pass the Hash TA0008: T1550.002 – Pass the Hash | BlackLock uses PtH techniques to move laterally within networks, taking a user's NTLM hash to access other hosts. This rule detects such attacks via security tool alerts or host-based event logging. |
To cut your mean time to contain (MTTC) threats from hours to minutes and minimize damage from BlackLock’s attacks, organizations should pair GreyMatter detections with the following Automated Response Playbooks. These ready-to-go workflows automatically counter BlackLock’s tactics, stopping attacks quickly and preventing cascading effects like data encryption, lateral movement, and exfiltration. Adding Automated Response Playbooks to your incident response plan means faster, more consistent defenses against BlackLock’s evolving techniques.
Terminate Active Sessions: Ends hijacked sessions to immediately block attacker access and prevent lateral movement across systems.
Reset Passwords: Resets compromised credentials to render stolen passwords useless and block attacker re-entry.
Disable User: Deactivates compromised accounts used to execute unauthorized actions, such as PowerShell scripts or malicious activity.
Your Action Plan
In addition to foundational security measures—such as enabling multifactor authentication (MFA) and disabling Remote Desktop Protocol (RDP) on unnecessary systems—defending against BlackLock requires strategic focus on its targeted infrastructure. With ESXi as one of BlackLock’s main attack vectors, securing this environment is critical.
Disable Unnecessary Services: Turn off unused management services such as vMotion, Simple Network Management Protocol (SNMP), and redundant HTTPS interfaces to minimize attack surfaces. While these services help manage or monitor ESXi hosts, leaving them active unnecessarily can create vulnerabilities. Additionally, enable Secure Shell (SSH) only when needed and disable it immediately after use.
Enable Strict Lockdown Mode: To complicate BlackLock’s ability to exploit weak interfaces, configure ESXi hosts to allow management exclusively through vCenter. Lockdown mode prevents direct connections to ESXi hosts, such as via SSH, unless explicitly allowed during emergencies. Routing all interactions through vCenter Server significantly reduces the risk of unauthorized privilege escalation and unmonitored actions.
Restrict Network Access: Use identity-aware firewalls or strict access control lists (ACLs) to block BlackLock from accessing ESXi hosts or moving laterally. For added security, only allow access through secure jump servers—dedicated systems used to connect to critical infrastructure—or out-of-band management systems on isolated networks.
What’s Next
Early Warnings Suggest Entra Connect Is Next Target
ReliaQuest found evidence suggesting that BlackLock may be planning to exploit Microsoft Entra Connect synchronization mechanics as part of its evolving attack strategy, providing early warnings about its likely campaign focus in 2025.
During a targeted investigation into user $$$, prompted by BlackLock’s rapid rise in 2024, we identified a post from January 28, 2025 made by $$$ that included a link to a security research blog. The blog explained how attackers could abuse Entra Connect’s synchronization to manipulate user attributes and compromise on-premises environments (see Figure 5). The blog highlighted the following:
Attackers could add a public key to the msDS-KeyCredentialLink attribute of an Entra user, enabling them to authenticate as that user in on-premises environments.
This tactic bypasses traditional security controls and allows attackers to escalate privileges and move laterally across connected systems.
Entra Connect treats the entire Entra tenant as a single trust boundary. Compromising one domain likely means the compromise of all others in the tenant.
$$$ stated: “I’m looking for people who are able to work with this… will provide all necessities.”
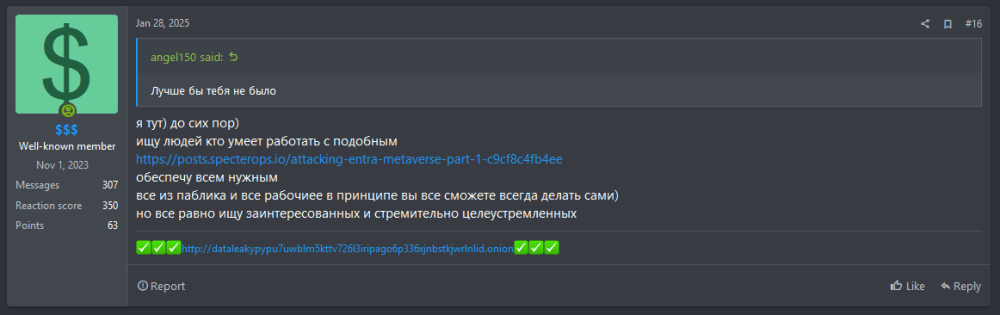
Figure 5: $$$ posts about a blog on Entra Connect tradecraft and asks for users who can work with it
For organizations managing multiple domains under one tenant, this tactic creates a significant risk of privilege escalation and the potential for a major breach. While the blog describes the attack hypothetically, its feasibility and potential impact make it a serious concern.
What makes BlackLock’s interest in Entra Connect stand out is its overt focus on initial access—a rarity among RaaS groups, which usually stick to post-compromise stages. While attacks using Entra as a vector are unusual, the ransomware group “Storm-0501” demonstrated its potential by exploiting Entra using a different method in September 2024.
This discovery underscores the importance of proactive solutions like ReliaQuest GreyMatter Digital Risk Protection (DRP). GreyMatter DRP not only monitors posts from users like $$$ but also promptly alerts you if ransomware operators mention your organization or assets—empowering you to take action before threats escalate.
Since BlackLock is likely to target Entra Tenant vulnerabilities in the future, it’s critical to secure this infrastructure now. Here’s how to get ahead of the risk:
Harden Attribute Synchronization Rules: Customize Entra Connect sync rules to turn off unnecessary flows, especially for sensitive attributes like msDS-KeyCredentialLink, to stop BlackLock from abusing them to access accounts.
Monitor and Restrict Key Registrations: Require administrator approval for key registrations and regularly audit the msDS-KeyCredentialLink attribute for unexpected changes to block malicious keys.
Enforce Conditional Access Policies: Limit key registration to compliant devices and apply location- or risk-based restrictions to prevent BlackLock from registering rogue keys or performing unauthorized syncs.
Copycat Forum Activity and Emerging IAM Attack Vector
By building its influence on RAMP and pursuing Entra Connect tradecraft, BlackLock is laying the groundwork for its next wave of campaigns in 2025. The following insights outline how its tactics and collaborations are likely to develop.
Boosting the Competition: As of January 2025, $$$ ranks third for post count and fifth for reputation score on RAMP, cementing their influence and trust within the ransomware community. By backing groups like Dragonforce and Lynx, $$$ has shown how an active RAMP presence and strategic collaboration drives success. This approach is likely to inspire other actors to copy BlackLock’s model to grow their own operations, which means we’re likely to see a wider range of effective attacks in 2025.
The IAM Strategy: BlackLock’s focus on Entra Connect tradecraft indicates the group will likely pursue the identity and access management (IAM) attack vector as a key strategy. By exploiting synchronization flows between on-premises and cloud environments, attackers can manipulate trusted mechanisms to escalate privileges, maintain persistence, and compromise connected domains. To extend its capabilities, BlackLock will likely recruit specialists skilled in IAM systems like VMware AirWatch and Cisco Identity Services Engine. This expertise would allow BlackLock to exploit hybrid infrastructures for more sophisticated attacks.