Key Findings
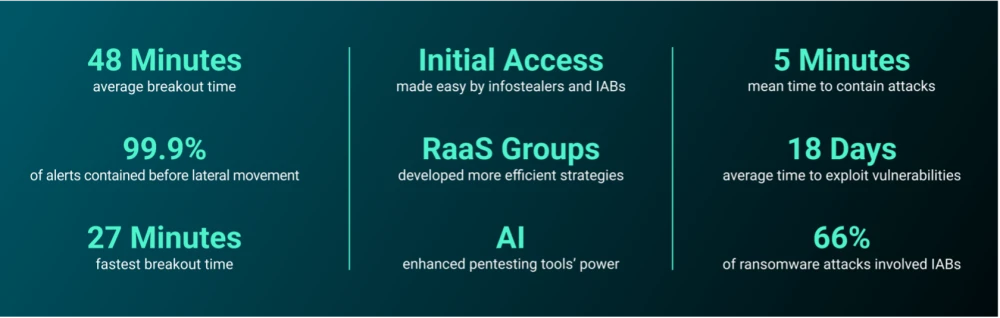
2024 was the year cyber threats got quicker. Cyber attackers really picked up the pace, executing faster, more efficient breaches that pushed traditional defenses to their limits. Our research reveals 2024 saw a 22% increase in attack speed compared to 2023, with the fastest incident achieving lateral movement in just 27 minutes. This quicker infiltration leaves organizations with even less time to respond, making automated defenses crucial in matching—and surpassing—the speed of adversaries.
We’ve identified three main factors driving faster attack speeds:
Increased Activity by IABs: Initial access brokers (IABs) are capitalizing on the surge in information-stealing malware (infostealers), offering adversaries a quick and easy way to launch attacks.
Streamlined RaaS Operations: The ransomware-as-a-service (RaaS) ecosystem has become more efficient, with affiliates adopting new, more specialized strategies like help-desk scams to accelerate and refine their attacks.
AI-Enhanced Pentesting Tools: Threat actors are using AI to boost the capabilities of penetration testing (pentesting) tools, allowing them to identify flaws in victim systems faster.
In this report, we unpack the drivers behind the accelerated cyber attacks and provide actionable recommendations to help organizations tackle the evolving threat landscape. We’ll explore why containing attacks as fast as possible is crucial and explain how ReliaQuest GreyMatter uses automation and self-learning AI to empower our customers with rapid, effective responses.
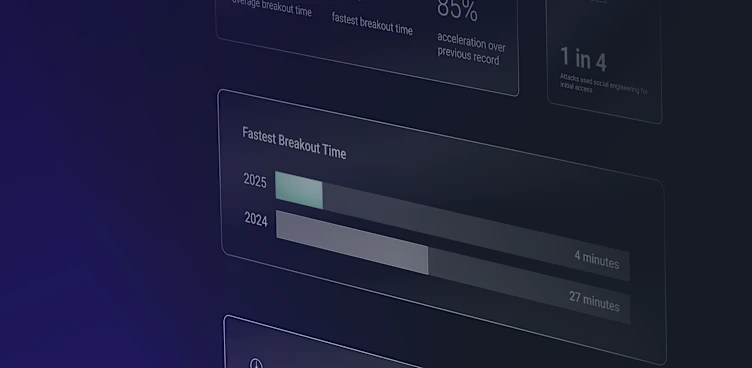
Attackers Move Faster: Breakout Time Falls to 48 Minutes
We analyzed GreyMatter data to measure breakout time in customer incidents throughout 2024. We found that the average breakout time was 48 minutes—22% faster than in 2023, based on comparisons with external industry reporting. The fastest breakout time recorded was just 27 minutes.
While only a tiny percentage (0.02%) of true-positive alerts for our customers led to lateral movement, the trend is clear: attacks are getting faster.
Breakout time is the time it takes threat actors to progress from initial access to lateral movement—the point when the incident becomes harder to detect and contain. Our investigation measured the average time between initial access and successful lateral movement in incidents that involved hands-on-keyboard activity from attackers between January 1 and December 31, 2024. In cases where IABs were likely used, we measured breakout time from the beginning of the second intrusion, as lateral movement typically doesn’t occur during an IAB intrusion. |
For defenders, breakout time is the most critical window in an attack. Successful threat containment at this stage prevents severe consequences, such as data exfiltration, ransomware deployment, data loss, reputational damage, and financial loss. So, if attackers are moving faster, defenders must match their pace to stand a chance of stopping them.
Our customer data shows this challenge clearly: the mean time to contain (MTTC) attacks for security teams relying solely on manual incident containment strategies is 8 hours 12 minutes. This leaves organizations fighting a losing battle against attackers who are in and through a network in under 30 minutes. In contrast, GreyMatter customers using Automated Response Playbooks reduce their containment time to under 5 minutes, allowing them to outpace even the speediest threat actors.
We recommend tailoring responses to align with the three key strategies that attackers are using in their workflows to make them more efficient and reduce breakout time.
Infostealers Nearly Double, IAB Listings Skyrocket 142%
In the intricate dark-web supply chain, threat actors deploy infostealers to harvest credentials, which they then sell on dark-web marketplaces to more sophisticated cybercriminals. Buyers of these credentials include ransomware affiliates, un-affiliated threat actors, and IABs.
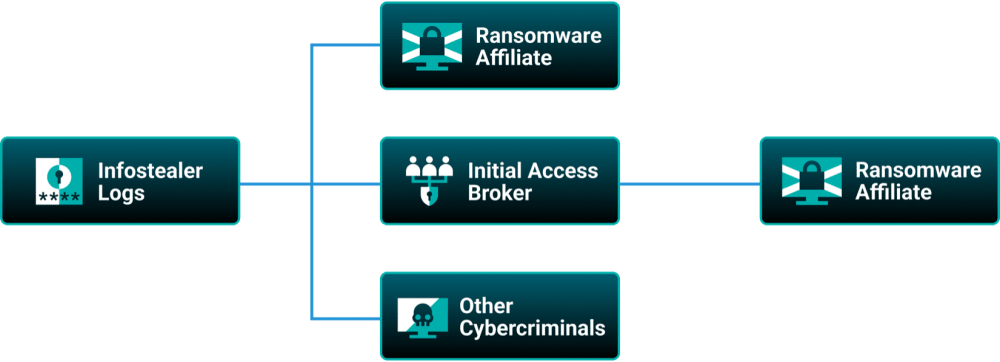
Figure 1: Infostealer logs are often sold to IABs, or they can be sold directly to adversaries
ReliaQuest collections reveal a >50% increase in infostealer logs posted on the dark web in 2024 compared to 2023. During the same period, initial access listings on cybercriminal platforms surged by 142%.
An increase in available credentials allows IABs to provide greater volumes of quick, low-effort access to privileged systems. Among the 2024 hands-on-keyboard incidents we analyzed, 50% of them used valid or exposed credentials for initial access. The consequences of this supply chain can be severe: GreyMatter data shows that 66% of customer ransomware incidents in 2024 involved initial access likely purchased from an IAB.
By purchasing access from IABs, attackers skip the time-consuming process of network infiltration and gain immediate entry, often with admin-level privileges or pre-installed backdoors. This drastically reduces breakout time, enabling threat actors to focus on deploying ransomware or stealing data with minimal delay. According to GreyMatter data, threat actors who use IABs can achieve breakout times as fast as 27 minutes.
To make their breakout time faster still, we saw evidence of threat actors creatively combining infostealer logs and automated scripts in 2024.
In a BreachForums post on December 4, 2024, a user claimed to have used infostealers to identify 21 Zabbix accounts vulnerable to CVE-2024-42327 (see Figure 2). Zabbix, an open-source IT monitoring tool, oversees networks and servers. Using exposed credentials and infostealer logs, the user created a proof of concept (PoC) script to authenticate via the target’s API, obtain a session ID, and gain access. By automating the reconnaissance and initial access stages of the attack on multiple systems simultaneously, the user identified vulnerable targets in seconds and reduced their overall breakout time. ReliaQuest expects to see more infostealers used within automated scripts in the short to medium term, as generative AI (GenAI) tools lower the barrier of entry into coding.
Infostealers like “LummaC2” and “Raccoon” harvest personal, financial, and business data—including passwords, credit card numbers, and browsing history—from compromised systems. They often infiltrate systems via phishing emails or compromised websites and operate quietly to avoid detection. Using techniques like keylogging (to capture everything a user types) or form grabbing (intercepting data submitted in web forms before it’s encrypted by the browser), they steal sensitive data and credentials that are then sold on cybercriminal forums, specialized log marketplaces, and messaging apps like Telegram |
IABs act as middlemen in the initial access supply chain. They specialize in breaching networks and selling access to other threat actors. Using methods like phishing, exploiting vulnerabilities, or stealing credentials, IABs gain entry into systems but rarely exploit them directly. Instead, they sell the access to ransomware affiliates, data thieves, and other cybercriminals. The more privileged the access, the higher the price, so IABs are incentivized to escalate privileges before selling. It’s a win-win for buyers and brokers—buyers save time and IABs walk away with bigger profits. |
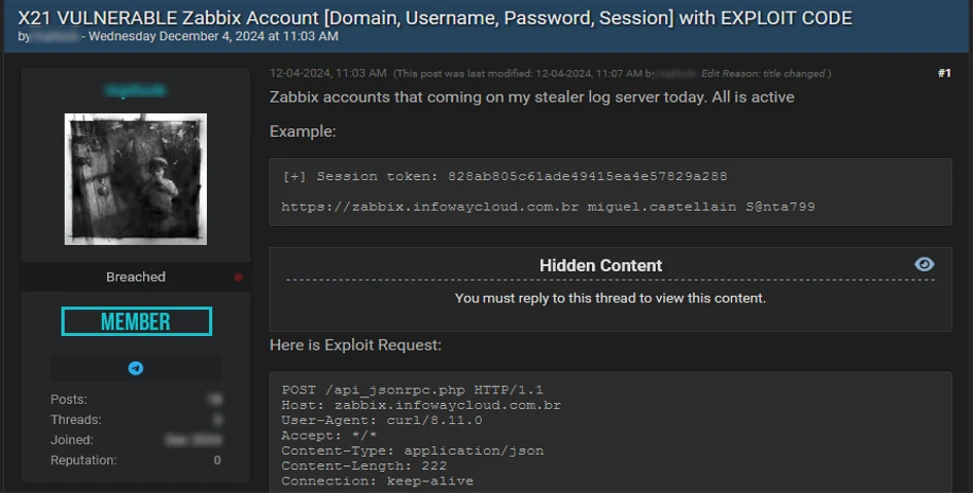
Figure 2: BreachForums user shares vulnerable Zabbix accounts found using an infostealer and automated scriptsTo protect your networks from infostealers and IABs, we strongly advise you:
Disable password saving in browsers to prevent theft. Use dedicated secret management software to securely store credentials and prevent infostealer malware from retrieving passwords saved to browsers.
Monitor for exposed credentials on the dark web using, for example, ReliaQuest Digital Risk Protection (DRP). When an exposure is identified, an alert is triggered, allowing you to take immediate action, such as ending the session, enforcing a password change, and notifying the affected user.
Secure administrative accounts using Privileged Access Management (PAM) solutions and monitor privileged actions for suspicious behavior, as IABs target accounts with high levels of access, such as domain or local administrator accounts.
How Specialized Affiliates and Smarter Tactics Are Accelerating Ransomware
The RaaS market is growing, both in the number of publicly named victims and in diversity. As outlined in our latest ransomware report, the number of active ransomware groups—mostly RaaS operations—ballooned from 60 in 2022 to almost 100 last year. As competition grows between ransomware groups, so does the need to scale and outpace defenders. As a result, RaaS groups have developed new strategies and techniques to reduce breakout time.
The RaaS model is already far more efficient than traditional ransomware schemes. By providing a “plug-and-play” approach, RaaS eliminates lengthy development cycles, enabling attackers to launch attacks quicker and easier than ever before. Once within the RaaS system, affiliates—who earn a share of ransoms—are incentivized to scale their operations and refine their tactics to outpace manual defenses. The result of faster attacks? More organizations are hit in less time.
We’ve identified two main methods that affiliates have been using to accelerate breakout times that are poised to become even more prominent in the coming year: collaborating with other affiliates in an “assembly line” and conducting help-desk scams.
Attacks Get Faster Through Specialized Ransomware Assembly Lines
In our analysis of ransomware incidents, we noticed distinct peaks and troughs in activity within compromised environments. This suggests that affiliates are dividing attacks into phases. We assess with high confidence that affiliates of many RaaS groups, particularly “Black Basta,” are working as an assembly line, with each affiliate specializing in a specific attack stage before handing over to the next affiliate.
In multiple ransomware incidents, we’ve observed periods of fast and intense activity followed by breaks lasting up to 48 hours—likely representing the handover between affiliates. During the breakout phase (see Phase 1 in Figure 3 below), threat actors move from one procedure (technique) to the next in an average of just 7 minutes. Notably, there are no time gaps between procedures during the breakout phase, suggesting the breakout phase is handled by one affiliate in a single sprint with no handover.
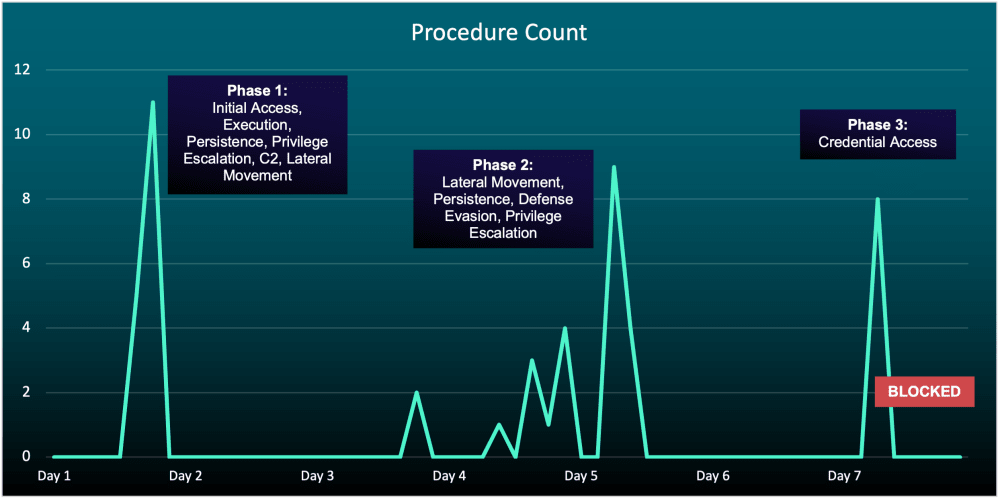
Figure 3: Timeline of incident involving “assembly line” strategy
Attacks which likely use this assembly line process revealed highly repetitive techniques, indicating efforts to scale and remove the brainwork from attacks and speed up operations.
There are a few ways in which this phased approach allows RaaS groups to move faster:
Practice makes perfect. Affiliates repeatedly work in one attack phase, continually gaining experience, thereby reducing the likelihood of mistakes and hesitancy. This, in turn, makes an assembly-line attack strategy more efficient and effective.
Specialized affiliates largely repeat the same techniques in their part of an attack, so they are more likely to have all the resources and tools they need close to hand. Resources include email spamming tools, exploitation frameworks, and infostealer logs. Affiliates using IABs for access need to have non-traceable cryptocurrency and often a guarantor to facilitate purchase.
RaaS groups can recruit affiliates with certain skills, such as pentesting or ways to gain initial access (see Figure 4). By recruiting specialists, ransomware groups can hire highly skilled affiliates who don’t need to learn on the job.
As a result, affiliates can finish their part of the attack at lightning speed, far exceeding manual containment efforts. By having one affiliate in charge of the breakout phase, RaaS groups ensure maximum efficiency and ensure the attack is not disrupted before lateral movement.

Figure 4: “DragonForce” ransomware group recruits “specialists in different spheres, from access to pentesters” on RAMP forum
Help-Desk Scams: The Fast Track to Compromise
IT help-desk scams skyrocketed in 2024, with 17% of incidents involving voice phishing for initial access—a key indicator of a help-desk scam. These scams are often linked to groups like Black Basta and “Scattered Spider” and largely take two forms:
Attackers launch an email spam wave followed by a phishing message via Microsoft Teams, posing as help-desk employees offering “assistance” to users to elicit a fast response.
Attackers impersonate legitimate users to trick the target organization’s help desk into granting access.
We recorded a mean time of just four minutes between the initial email wave and the phishing message, with another four minutes to establish command-and-control (C2), demonstrating how quickly threat actors can move. The breakneck speed at which threat actors can socially engineer users, send a phishing message via instant messaging, and then use native Remote Management and Monitoring (RMM) tools to establish a C2 connection allows the threat actor to swiftly advance their attack and achieve rapid breakout times.
The success of these help-desk scams hinges on the abuse of standard IT practices, particularly remote management sessions. Many organizations rely on RMM tools for help-desk support, enabling IT staff to take control of user accounts. Attackers exploit legitimate tools such as AnyDesk, TeamViewer, and ScreenConnect to install malware, execute code, and move laterally across networks without raising suspicion. By using living off the land (LotL) techniques, attackers bypass the need for additional software and establish persistence quickly, making their attacks faster and harder to detect.
Customer Case Study |
In December 2024, ReliaQuest responded to an attack on a manufacturing company carried out by the Black Basta ransomware group, who likely used the assembly-line approach to execute the attack (see Figure 5). |
Characteristic of Black Basta attacks, the user first received an influx of spam emails, followed by a phishing message on Microsoft Teams impersonating the user’s company help desk. The attacker quickly convinced the user to start a Quick Assist session, giving the attacker remote control of the system. From there, the attacker used process injection to move laterally via remote desktop protocol (RDP) and set up a new C2 connection using a OneDrive beacon to a malicious IP address. |
What made this attack so effective was the clever use of Teams and Quick Assist. Employees tend to respond more quickly to Teams messages than emails, especially when the sender appears to be an internal help desk. Additionally, organizations usually have Quick Assist—a remote support tool built into Windows 10 and 11—already installed on their systems for legitimate IT assistance. This meant the attacker didn’t need to waste precious time convincing their target to download sketchy software, which might have raised red flags or led to detection. |
Following this incident, ReliaQuest developed new detections to identify spearphishing attempts via Teams. These include monitoring for new chats created by external users and identifying suspicious chat names (e.g., “Support or “Troubleshoot”) and Teams messages sent to multiple users. |
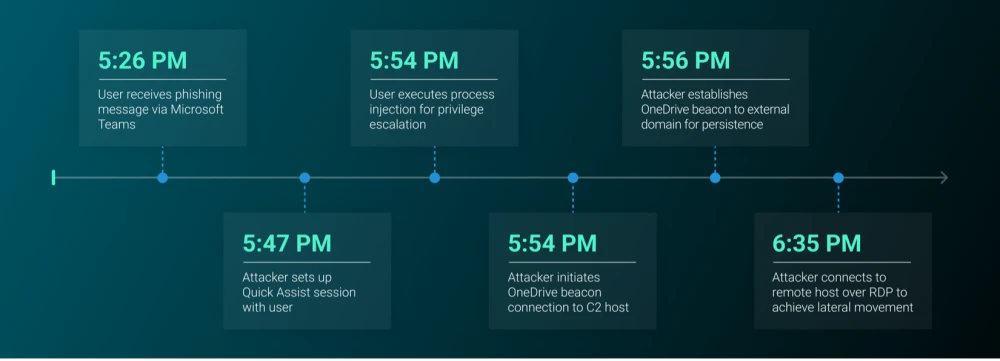
Figure 5: Timeline of techniques used from initial access to first lateral movement in case study incident
Take Action
Enable logging for Microsoft Teams, particularly the “ChatCreated” event, to detect and monitor unauthorized activity.
Create an allowlist of approved external users and block communications from users not on the list (see Figure 6).
Notify users, IT personnel, and security teams about this ongoing campaign. Remind users to follow established communication channels and procedures for IT support and emphasize that IT assistance offered outside of these procedures shouldn’t be trusted.
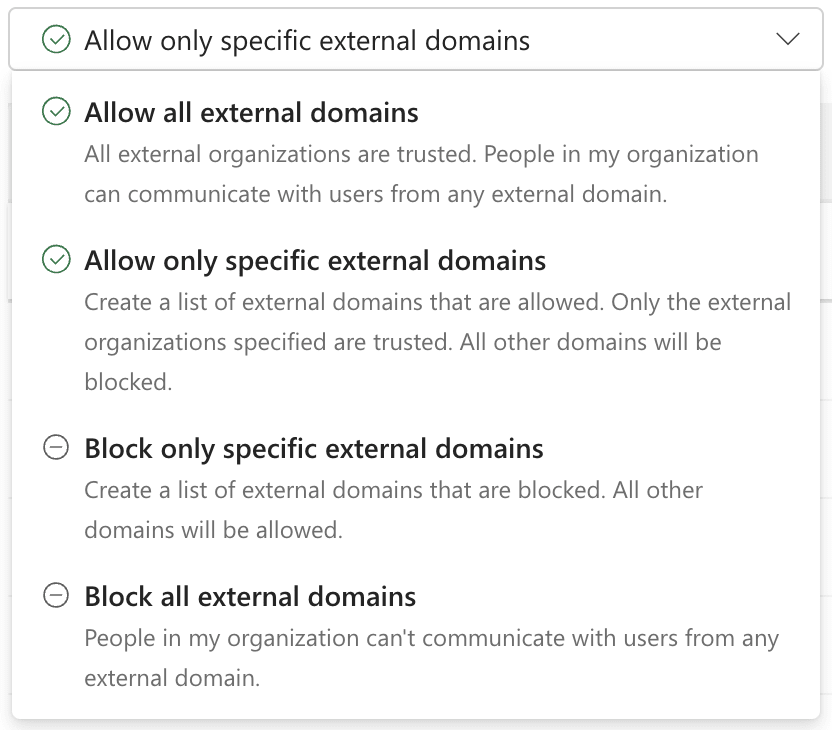
Figure 6: Allowing only specific external domains to communicate with users mitigates the risk of threat actors leveraging Microsoft Teams for phishing
The Role of AI in Faster Vulnerability Exploitation
ReliaQuest has identified a 62% reduction in the time between a vulnerability being discovered and its exploitation by attackers—known as the time to exploitation. In 2023, the average time to exploitation was 47 days, but in 2024, this dropped to just 18 days. This sharp decrease strongly indicates that a major technological advancement—likely GenAI—is enabling threat actors to exploit vulnerabilities at unprecedented speeds.
These advances accelerate many phases in the kill chain, particularly initial access. We found vulnerability exploitation accounted for over 17% of initial access incidents among ReliaQuest customers in 2024.
For many years, threat actors have been co-opting legitimate pentesting tools to exploit vulnerabilities. However, with the emergence of AI and automation enhancing their capabilities, this now presents a bigger risk.
Thanks to these technologies, attackers can automate reconnaissance, spot vulnerabilities faster, and adapt exploitation techniques in real time based on the target’s defenses. As a result, they skip the manual, time-consuming trial-and-error processes to achieve faster lateral movement and payload deployment, which significantly reduces breakout time.
Adversaries are leveraging GenAI alongside pentesting tools to:
Generate instant guidance on pentesting tools, allowing threat actors to sharpen their skills and bridge knowledge gaps.
Write scripts for tasks like network scanning, privilege escalation, and payload customization. Custom payloads and modules help threat actors bypass detection, further increasing the likelihood of success.
Analyze scan results and suggest optimal exploits, enabling attackers to target critical vulnerabilities and refine attack strategies.
Pentesting tools, particularly exploitation frameworks, are among the most powerful tools in a threat actor's arsenal. Originally designed for legitimate pentesting, these tools identify and exploit vulnerabilities in software, systems, or networks. Cybersecurity professionals widely use frameworks like Metasploit, Burp Suite, and Cobalt Strike for assessing digital security, as they offer pre-built modules and scripts that automate complex tasks. |
Recognizing the potential of AI to streamline pentesting, legitimate tools like Burp Suite have integrated large language models (LLMs) to enhance vulnerability scanning and traffic analysis.
As a result, threat actors using Burp Suite can now read an analysis of the tool’s results in plain English, making their next steps clearer and more likely to be successful. While these integrations lower the barrier to entry for legitimate pentesters, they also empower less-experienced threat actors to abuse pentesting tools.
Additionally, dark-web activity indicates that threat actors are creating their own tools that integrate LLMs with pentesting tools. On the Russian-language forum XSS, a user shared a GitHub link to a tool combining Nmap, Nuclei, and SQLmap with Llama, Meta’s open-source LLM (see Figure 7).
In this case, the LLM agent acts as a “consultant,” analyzing vulnerability scans and providing guidance. By integrating AI in this way, threat actors skip the trial-and-error process associated with vulnerability exploitation, increasing their speed and ability to adapt to the specificities of compromised environments. We expect breakout times will continue to decrease as threat actorsincorporate more automation in vulnerability exploitation.
Figure 7: Python code corresponding to the AI analysis file of a pentesting tool created by a forum user
To mitigate the risks of threat actors using exploitation frameworks during attacks, organizations should:
Revise patching programmes and systematically reduce delays in updating and applying security patches.
Ensure old, well-known vulnerabilities are patched, as exploitation frameworks typically have large libraries dedicated to older vulnerabilities. According to ReliaQuest data, threat actors are more likely to exploit old vulnerabilities than newly disclosed ones, as resources like PoCs for older vulnerabilities are easier to find online.
Exploitation frameworks heavily rely on PowerShell and other scripting tools, so enable PowerShell Script Block logging and command logging to capture and analyze all executed scripts and commands. Focus on detecting malicious activity like encoded payloads or unauthorized use of administrative modules. Additionally, monitor for unusual scripting behavior, such as PowerShell execution by non-standard accounts or from unexpected locations.
Step Up Your Defenses Against Faster Attacks
ReliaQuest’s Approach
Cyber threat actors are moving fast—so defenders must move faster. With breakout time down to just 48 minutes, threat actors are achieving lateral movement faster than ever. At this point, manual defenses just can’t catch up.
ReliaQuest GreyMatter seamlessly integrates with any technology in your existing tool stack to identify and contain threats within just 5 minutes. This rapid response prevents cybercriminals from gaining or maintaining a foothold in your environment, giving your teams the critical time they need to investigate and address root causes.
Our GreyMatter platform leverages decades of security data to power generative and agentic AI, streamlining Tier 1 and Tier 2 tasks. Combined with automation, this enhances threat detection, containment, investigation, and response, enabling customers to outpace threat actors.
By deploying detections together with GreyMatter’s Automated Response Playbooks, organizations can drive down their MTTC from hours to just 5 minutes. Rapid responses are crucial in containing threats before they inflict damage. We advise customers to incorporate the following Automated Response Playbooks into their incident response plans for a faster and more efficient defense strategy:
Terminate Sessions and Reset Passwords: Threat actors abuse stolen credentials to move laterally, gaining access to high-value data. This Playbook cuts off an attacker’s access by terminating hijacked sessions and resetting compromised credentials.
Delete File: This Playbook automatically removes ransomware payloads from a host’s directory, halting the execution of ransomware files before they can encrypt critical systems and data, minimizing attack impact.
Isolate Host: This Playbook isolates a compromised host from the network, preventing the attacker from maintaining C2 connection or moving laterally.
Top Lessons and What’s Next
Breakout times are at an all-time low, and it’s clear that manual containment can’t keep up anymore. Attackers are leveraging new technologies like automation and evolving social engineering tactics, leaving organizations with no choice but to fight fire with fire. Automation is no longer optional—it’s essential to protecting what matters most: our people, data, and time. While organizations may differ in their adoption of automation, the risk of breaches continues to rise, and this trend isn’t slowing down. Breakout times will likely drop further, eventually leveling off at around 30 minutes, as certain steps—like making complex decisions or addressing unique scenarios—still require a human touch. The only way to counter this increasing speed is to be even faster. And that means integrating automation into your containment strategy.