Key Findings

The first quarter of 2025 set new ransomware records, with more organizations named on data-leak sites than ever before. In this report, we’ll discuss:
“Clop’s” dominance in February 2025 and its focus on the retail trade sector.
Our original research into leaked “Black Basta” chat logs.
Ransomware predictions for the rest of 2025.
Actionable recommendations to safeguard your data.
Read on to learn the key factors behind this surge, the broader implications for the ransomware threat landscape, and strategies to help your organization stay ahead in the enduring fight against ransomware.
February Shatters December’s All-Time High
for the most organizations listed on data-leak sites—but February 2025 blew past those numbers, driven by major activity spikes from ransomware groups Clop, “Medusa,” and “FunkSec.” Clop alone was responsible for 35% of all victims named on data-leak sites that month.
Clop’s latest campaign, exploiting zero-day vulnerabilities (CVE-2024-50623 and CVE-2024-55956) in Cleo managed file transfer (MFT) solutions, fueled a 23% increase in overall ransomware activity between Q4 2024 and Q1 2025. Clop’s exploitation of Cleo highlights how weaknesses in systems can ripple across interconnected industries, disrupting supply chains, halting operations, and impacting countless businesses simultaneously. To mitigate this risk, organizations must prioritize targeted risk assessments of third-party platforms like Cleo to identify vulnerabilities and address weaknesses before they’re exploited for large-scale disruptions.

Figure 1: Number of compromised organizations listed on data-leak sites, April 2024 through March 2025 versus April 2023 through March 2024
Ransomware-as-a-service (RaaS) group Medusa reached even greater heights this quarter, jumping 35% compared to Q4 2024, potentially capitalizing on the void left by disrupted ransomware gangs in late 2024. Medusa has increasingly targeted critical infrastructure, where disruptions can cripple essential services and cause widespread chaos. At-risk organizations should implement deception technologies, such as honeypots and decoy systems, to misdirect attackers and gather intelligence on their tactics.
Meanwhile, FunkSec continued its meteoric rise, carrying momentum from Q4 2024 into Q1 2025. Leveraging AI to develop malware, FunkSec named 152 victims this quarter—up from 82 last quarter—earning its place as the fourth most active ransomware groups in Q1 2025. This surge demonstrates how AI is enabling even inexperienced threat actors to launch sophisticated attacks across multiple sectors.
Clop’s Cleo Campaign Sets Q1 Records
Clop’s explosive start to 2025 reflects its strategy of operating in bursts. After naming just 26 victims in 2024, Clop skyrocketed to an unprecedented 389 victims in February alone—a staggering 1,400% increase. Clop’s ability to lie dormant for months before launching high-impact campaigns highlights the need for constant defenses against its usual tactics, techniques, and procedures (TTPs), such as vulnerability exploitation and mass data exfiltration. Its attacks can strike without warning, demanding vigilance from organizations.

Figure 2: Number of organizations listed on data-leak sites by ransomware group, Q1 2025
In contrast, Q4 2024 leader “RansomHub” saw a slight 1% dip in activity following its January 2025 announcement of a profit-split reduction from 90/10 to 85/15. While it’s too early to determine whether this change will significantly impact operations, Q1’s minor decrease is likely natural variation rather than a meaningful trend.
Despite reduced profit shares, RansomHub remains appealing to affiliates because of its adaptability and innovation. And its developments in Q1 2025 reaffirm the group’s status as a persistent threat:
Custom Backdoor: Affiliates now use “Betruger,” a versatile malware for keylogging, credential dumping, and network scanning, streamlining pre-deployment activities.
“SocGholish” (aka FakeUpdates): RansomHub used this JavaScript malware via fake browser updates on compromised sites, targeting US government entities to establish access and deploy ransomware.
Expanded Target Scope: Tailored encryptors now target Windows, ESXi, Linux, and FreeBSD, abusing CVE-2024-3400. Affiliates use tools like Nmap for reconnaissance, PCHunter to disable defenses, and FileZilla for data exfiltration.
Affiliates leaving groups like RansomHub are driving cross-pollination of tactics, spreading proven methods across ransomware gangs and complicating attribution. Meanwhile, groups are deploying custom backdoors, exploiting fresh vulnerabilities, and expanding their reach across operating systems—innovations designed to outmaneuver traditional defenses.
Group To Watch
Name: “Lynx”
Type: RaaS group
Emergence: July 2024
Victimology: US- and France-based wholesale trade and professional, scientific, and technical services (PSTS) organizations
Highlight: Activity rose 115% between Q4 2024 and Q1 2025
Encryption: Utilizes Go-based ransomware builder compatible with Windows and Linux. Employs AES-CTR for file encryption and ECC Curve25519 for key exchange. Attackers can customize encryption via command-line flags to target specific files, directories, or systems.
File Impact: Avoids encrypting critical directories (e.g., Windows, Program Files) and file types (e.g., .exe, .dll). Attaches ransom notes titled “README.txt” containing contact details for Tor and email communication.
Anti-Recovery Measures: Deletes shadow copies, encrypts hidden volumes, and terminates backup-related processes such as SQL, Veeam, and Exchange.
To stay ahead, enterprises should invest in AI-driven anomaly detection capable of flagging unconventional patterns, such as cross-operating system activity or the deployment of custom backdoors, helping predict emerging tactics before they’re fully weaponized. Additionally, engaging in industry-wide intelligence sharing can provide insights into affiliate activities, enabling organizations to disrupt collaborative ransomware efforts at their roots.
Take Action
To defend against RansomHub, focus on three key strategies:
Monitor for IOCs: Use behavioral analysis tools to detect indicators of compromise (IOCs) like suspicious filenames and unusual activity early.
Implement Network Segmentation: Restrict lateral movement and ransomware spread by segmenting your network
Prioritize Patch Management: Regularly update edge devices and operating systems to close vulnerabilities and reduce the risk of exploitation.
Retail Trade Under Fire from Clop, Europe Feels the Heat
and entities have long been top ransomware targets, and Q1 2025 was no exception. However, the real shake-up came in the , with Clop’s campaign accounting for 46% of retail trade organizations named on data-leak sites and pushing the sector from sixth to fourth place compared to Q4 2024. Why? Many retailers rely on Cleo for managing e-commerce transactions, order fulfillment, and supplier coordination. So, the impact of targeting Cleo can be severe, including financial losses, recovery costs, fines, reputational damage, and strained trust with customers and partners. While retail trade organizations are experiencing heavy ransomware targeting now, we don’t expect this trend to last. Once the dust settles, attackers will likely refocus on industries they’ve traditionally targeted.

Figure 3: Number of compromised organizations listed on data-leak sites by sector, Q1 2025
Ransomware activity in the US and Europe spiked this quarter, with Clop’s aggressive campaign driving a big chunk of victim numbers across both regions. Yet while Clop’s operations are a major factor in Q1, these regions have always been prime targets for ransomware groups thanks to their strong economies, high-value industries, strong digital infrastructure, and potential for large-scale disruption. Countries like the US, France, Germany, and the UK remain consistent hotspots, regardless of the group behind the attack.
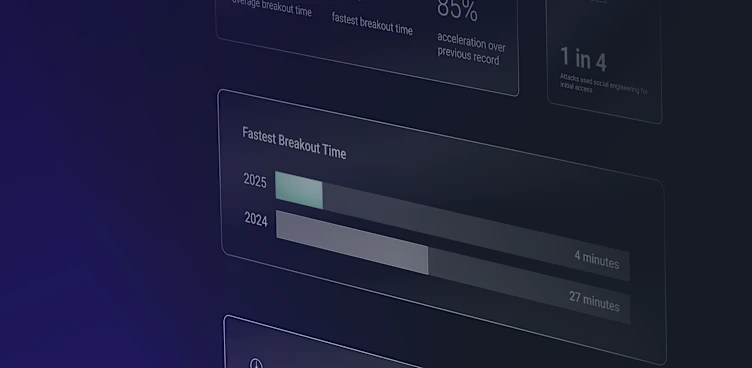
Even as Clop dominates the spotlight, the inherent appeal of these regions continues to draw attention from other ransomware groups. And growing competition among ransomware gangs is pushing attackers to exploit every available opportunity. This surge in ransomware activity across the US and Europe highlights how attackers are leveraging AI and automation to accelerate their campaigns and shorten breakout times—the critical window between initial access and lateral movement. With , attackers are clearly succeeding in their efforts and showing no signs of slow down.

Figure 4: Number of compromised organizations listed on data-leak sites by geography, Q1 2025
Take Action
Proactive strategies aren’t just nice to have—they’re essential for minimizing disruption and safeguarding operations in today’s ransomware landscape. By leveraging AI and automation, organizations can level the playing field and respond to attackers with equal speed and sophistication.
Approaches must also be tailored to specific sectors. Industries like retail trade, which heavily rely on MFT platforms like Cleo should prioritize isolating and hardening critical systems. Segment MFT platforms and other high-risk systems from the broader network to reduce exposure and limit lateral movement during attacks. Enforce strict access controls to ensure sensitive systems are accessible only to authorized users. Additionally, deploy real-time monitoring tools designed for supply-chain risks to detect anomalies or suspicious activity tied to ransomware tactics.
ReliaQuest Investigates: Black Basta Weaponizes Forums
In February 2025, a leak of Black Basta’s internal chat logs provided a rare glimpse into the group’s operations. Our analysis uncovered links to cybercriminal forum posts, revealing how Black Basta likely uses forums to acquire tools, exploits, and services. These cybercriminal marketplaces play a critical role in helping ransomware groups refine their tactics and scale their attacks.
By examining shared links, we mapped how forum resources directly align with Black Basta’s operations. The table below outlines the connections between forum posts and known Black Basta tactics and objectives, illustrating the group’s deep reliance on the underground ecosystem to fuel its operations.
Attack Phase | Forum Thread Title | Likely Black Basta Use Case | MITRE ATT&CK ID |
|---|---|---|---|
Initial Access | Spamming Services for Phishing Campaigns | Delivering ransomware payloads through emails that bypass filters. | T1193 – Spearphishing Attachment |
Initial Access | “QuantumBuilder” - Spoof Extensions and Bypass Security | Disguising ransomware payloads as legitimate file types to evade detection and gain access. | T1566 – Phishing |
Initial Access | PDF Landing Pages for Spam Campaigns | Ensuring payload delivery via inbox phishing campaigns, maximizing reach. | T1193 – Spearphishing Attachment |
Initial Access | Remote code execution (RCE) + Privilege Escalation Exploit for Veeam Backup | Exploiting vulnerabilities in enterprise systems to gain initial access and credentials. | T1190 – Exploit Public-Facing Application |
Privilege Escalation & Persistence | VMware ESXi Shell Exploit - Remote Access | Bypassing authentication to gain remote access, enabling lateral movement and persistence. | T1134 – Access Token Manipulation |
Privilege Escalation & Persistence | Hidden Virtual Network Computing (HVNC) | Enabling stealthy remote access for undetected data exfiltration and ransomware deployment. | T1071 – Application Layer Protocol |
Privilege Escalation & Persistence | Crypters and Loaders - Evade Detection | Ensuring ransomware payloads bypass detection and maintain persistence within compromised systems. | T1055 – Process Injection |
Privilege Escalation & Persistence | Masscan GUI Pro - Network Scanning Tool | Scanning networks to identify valuable targets for lateral movement and exfiltration. | T1046 – Network Service Scanning |
Exfiltration & Double Extortion | “Stealc” Malware for Data Theft | Facilitating data theft through admin panels, supporting double-extortion tactics. | T1020 – Automated Exfiltration |
Exfiltration & Double Extortion | Selling Stolen Data (Binlists) | Leveraging stolen data using tools like binlists for extortion. | T1056 – Input Capture |
Exfiltration & Double Extortion | Masscan GUI Pro - Network Scanning Tool | Locating sensitive data repositories for exfiltration during reconnaissance efforts. | T1046 – Network Service Scanning |
Exfiltration & Double Extortion | “LummaC2” Stealer Malware | Stealing credentials and exfiltrating data to strengthen extortion efforts. | T1560 – Archive Collected Data |
Ransomware Deployment | Crypters and Loaders - Evade Detection | Obfuscating ransomware payloads during deployment to bypass endpoint defenses. | T1027 – Obfuscated Files or Information |
Ransomware Deployment | PDF Droppers for Ransomware Deployment | Automating large-scale payload delivery for efficient ransomware deployment. | T1204 – User Execution |
Ransomware Deployment | QuantumBuilder - Spoof Extensions and Bypass Security | Automating delivery of ransomware payloads through spoofed file types. | T1204 – User Execution |
Ransomware Deployment | VMware ESXi Shell Exploit - Remote Access | Targeting virtualized environments, encrypting systems with tailored ransomware payloads. | T1210 – Exploitation of Remote Services |
Monitoring these cybercriminal platforms allows defenders to identify emerging threats, anticipate attack methods, and patch vulnerabilities before they’re weaponized. This is especially critical for high-risk tactics like phishing delivery methods and remote code execution (RCE) exploits, which Black Basta frequently uses to gain initial access. Beyond initial access, Black Basta’s focus on data theft and double extortion underscores the need for targeted defenses. The group uses tools like “Stealc” malware and Masscan to steal sensitive data and scan networks for high-value repositories. To counter these tactics, organizations should prioritize strong encryption for sensitive files, monitor network traffic to detect reconnaissance activity, and deploy tools capable of identifying unauthorized exfiltration. By zeroing in on these specific techniques, defenders can disrupt Black Basta’s operations and minimize the impact of their campaigns.
Step Up Your Defenses Against Ransomware
Your Action Plan
This report is full of valuable ransomware insights, but here are three quick-win measures that organizations should prioritize and implement immediately.
Introduce ransomware drills with live attack simulations to mimic real-world scenarios, including encryption tests on non-critical systems. These drills help teams practice and refine containment strategies, recovery protocols, and decision-making under pressure.
Perform regular data backups using immutable storage to ensure critical files cannot be tampered with during an attack. Test restoration processes frequently to guarantee rapid recovery in the event of ransomware infection.
Audit third-party access to sensitive systems and restrict vendor and partner access. Enforce strict cybersecurity standards, as third-party vulnerabilities are a common attack vector for ransomware campaigns.
Top Lessons and What’s Next
Q1 2025 set a record for ransomware victims listed on data-leak sites, driven heavily by Clop’s Cleo campaign. Ransomware groups are scaling rapidly, adopting new tactics, and using cybercriminal forums to access tools and exploits that expand their reach. As the year progresses, emerging groups and increasingly sophisticated techniques will likely challenge defenses further.
Smaller Groups, Frequent Rebranding: We expect law enforcement efforts to intensify throughout 2025, causing major ransomware players to splinter into smaller, agile entities to evade detection and prosecution. For instance, the group “Eldorado” rebranded to “BlackLock” and later to “Mamona R.I.P.,” shedding scrutiny while maintaining operational continuity. This trend reflects a broader shift toward stealth and flexibility, which we anticipate will be reflected in innovative tactics and techniques to help groups stay under the radar. Tracking rebrands, shifts in group structures, and changes in tactics and attack patterns—such as new naming conventions or updated ransomware payloads—will be essential for predicting and mitigating threats from these smaller, more agile groups.
Geopolitics and Ransomware: It’s realistically possible that by December 2025, geopolitical shifts—like changes in US-Russia relations post-election—could reshape the ransomware landscape. Historically, strained relations have allowed ransomware groups operating in Russia, including state-linked actors, to thrive under tacit government approval. Improved diplomatic ties, however, may prompt Russian authorities to crack down on these groups, particularly those benefiting from unofficial political protection. While this might reduce attacks from certain actors, it could also push groups to adapt by relocating, rebranding, shifting tactics, or even targeting new industries or regions to avoid crackdowns.
Ivan Khamenka is the primary author of this report.