As phishing attacks continue to rise, the influx of reported emails has turned the abuse mailbox into a significant operational burden for security teams. The task of analyzing these emails is so time-consuming that it often pulls security teams away from more critical priorities, thereby exposing organizations to risk. Automation can streamline the email analysis process, enabling security teams to concentrate on more strategic initiatives. However, it’s essential to implement a comprehensive automation strategy to ensure all aspects of the problem are addressed and to prevent reverting to old patterns.
This blog will break down the process of responding to reported emails and discuss how a comprehensive phishing analysis tool can help ease the associated operational burden.
The Process of Analyzing and Remediating Reported Emails
While technologies and processes may vary across industries and businesses, the steps for analyzing and addressing reported emails are generally the same: analyzing the email, assessing the impact and scope, and taking appropriate response actions. Following these steps helps organizations maintain strong security and reduces the chances of successful phishing attacks.
1. Email Verdict Analysis
The first step is to determine whether the reported email is malicious or benign. Although most reported emails are benign, it’s crucial to consistently analyze each one to ensure that no malicious emails go undetected. This analysis usually involves security technologies that perform actions such as:
Action | Purpose | Technology |
Scanning links | Verify if the links lead to malicious sites or have been flagged in threat intelligence databases. | URL analyzer, threat intelligence |
Detonating attachments | Detect any harmful payloads and analyze for unusual file types or unexpected attachments that may indicate a payload to exploit vulnerabilities. | Sandbox, malware analyzer |
Analyzing the sender | Verify the sender's email address and domain, check their reputation, and look for spoofing signs to ensure the email is trusted. | Email threat protection, threat intelligence |
Reviewing verbiage | Examine the language and content of the email for any signs of social engineering tactics, financial requests, fraud, etc. | Visual inspection, artificial intelligence |
Analyzing headers | Inspect the email headers to trace the email’s origin and check for any anomalies, authentication failures or spoofing attempts. | Header analyzer |
2. Impact and Scope Assessment
If an email is determined to be malicious, further investigation is required to assess its impact and scope. This step helps reveal the extent of the threat, identify any compromised accounts or systems, and determine the appropriate remediation measures. The below chart lists some of the actions associated with this step and the corresponding technologies typically used:
Action | Purpose | Technology |
Identify additional email recipients | Assess the spread and potential impact of the malicious email within the organization. | Email client, email server |
Track traffic from clicked phishing links | Determine if users clicked the malicious URLs and identify subsequent actions, such as entering credentials or downloading malware. | Proxy, firewall, email security gateway, threat intelligence, URL sandbox |
Identify malicious activity from downloaded attachments | Uncover if users downloaded emails attachments that contain malware, ransomware, or other harmful payloads that could compromise hosts | Endpoint detection and response (EDR), antivirus, operating system |
3. Response Actions
The investigation results will determine the actions security teams should take for the final step. This step focuses on remediating the attack and closing the loop with employees, which often involves revisiting the same tools used in previous steps. It ensures that any damage caused by the email is properly addressed, typically using various security technologies to perform actions such as:
Action | Purpose | Technology |
Deleting the email | Purge email from all affected inboxes to prevent further interaction. | Email, email threat protection |
Blocking IoCs | Neutralizes active threats and minimizes the potential entry points for attackers across the entire network. | Firewall, proxy, EDR, email |
Responding to reporter | Keeps the reporting user informed about the outcome and encourages continued reporting. |
*All steps should not be limited to the actions and technologies outlined in the charts alone, as different types of phishing emails require different tools.
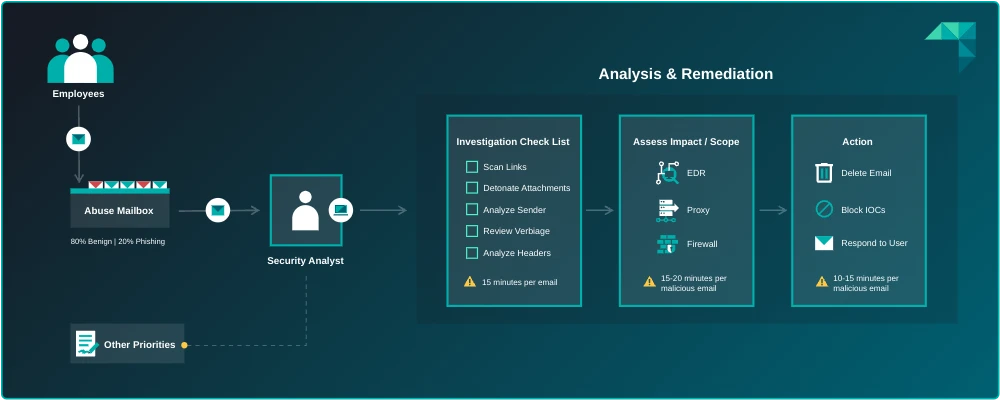
The Abuse Mailbox Process
Phishing Analysis Tools
While following this analysis and remediation process can help security teams better manage the abuse mailbox, doing it manually is extremely time-consuming and overwhelming, often leading to incomplete or skipped steps. It also creates organizational risks such as:
Deprioritized projects due to an overwhelmed security team.
Increased threat dwell time due to lack of interconnected security controls.
Decrease in employee engagement from inconsistent responses to reporters.
To relieve operational burden and reduce organizational risk, security teams should leverage a phishing analysis tool that automates all three steps.
Most abuse mailbox tools can classify an email and purge it from inboxes, but this alone is not enough to ensure comprehensive protection against phishing attacks and efficiently manage the abuse mailbox.
Security teams need a phishing analysis tool that streamlines the entire abuse mailbox process, including the steps outlined in the tables above. It should analyze each reported email, assess its impact, and take remediation actions across their entire technology stack. This not only eliminates the manual and time-consuming effort involved, but it also provides deeper visibility into these threats by providing a holistic approach.
ReliaQuest GreyMatter Phishing Analyzer
With the ReliaQuest GreyMatter Phishing Analyzer, organizations can achieve this holistic approach. The Phishing Analyzer automatically analyzes reported emails, takes remediation actions, and follows up with reporters in seconds. In addition, being a part of our comprehensive security operations platform, GreyMatter, it takes the abuse email inbox management process a step further, allowing security teams to see and act beyond just classifying the email.
For example, imagine a user clicks on a phishing link in an email, which leads to an automatic download of a malicious file. The user reports the email after noticing abnormal behavior on their computer. A typical phishing analysis tool might automatically confirm the email as malicious and remove it from inboxes. However, it often fails to provide a complete picture of the phishing link and the subsequent malware activity executing on the host. This gap usually requires manual investigation across multiple security tools, putting security teams back in the same challenging position.
The Phishing Analyzer, however, not only classifies the email and removes it from all inboxes but also identifies the phishing link and the associated malware activity. It then removes the malicious file, ensuring a streamlined resolution. Additionally, it can block the URL at the network edge using a firewall or proxy, preventing access to the phishing link from any network point, including messaging chats or direct browser entry.
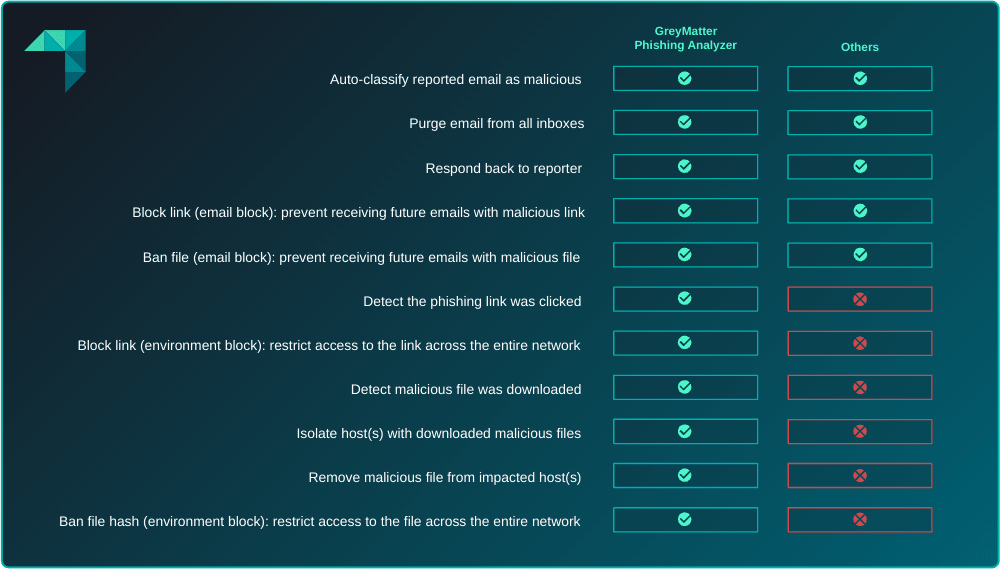
Beyond leveraging the integrations for investigation and responses, the Phishing Analyzer is enriched with curated insights by our ReliaQuest Threat Research team. Insights such as threat actor profiles, attack trends, industry targets, and more are provided for complete details of threats beyond standalone IOCs like email sender, URLs and hashes. GreyMatter reporting ties it all together, incorporating abuse mailbox metrics into overall performance metrics for enhanced visibility across security operations.
Conclusion
When managing the abuse mailbox, it’s crucial to implement automation to reduce the risks associated with manual efforts. While a phishing analysis tool can be helpful, it’s essential to choose a comprehensive solution, like the GreyMatter Phishing Analyzer, which automates the entire abuse mailbox process, from analyzing emails and responding to reporters to assessing impact and fully remediating threats. This end-to-end coverage frees up time for security teams, allowing them to focus on more strategic initiatives while effectively mitigating risk.







