Endpoint protection, including antivirus software, firewalls, and intrusion detection systems, is crucial for safeguarding devices. Endpoint detection and response (EDR) software takes this further by detecting and responding to threats in real time. However, EDR isn’t foolproof; it can miss sophisticated threats, relies heavily on timely updates and accurate threat intelligence, and cannot monitor several physical and virtual appliances that operate outside its scope of visibility. Some devices designed for efficiency may not be visible to EDR agents, and sometimes attackers can bypass endpoints altogether.
Imagine EDR as a sophisticated security camera system for your digital environment: it monitors extensively and captures a lot of activity, but a cunning intruder might still find a way in. While it is crucial, it represents just one component of your comprehensive security strategy.
The following blog analyzes three EDR-dodging threats identified in Beyond the Endpoint: Evading the Barrier of Endpoint Detection: email account takeover, adversary-in-the-middle attacks, and SaaS provider targeting.
The full version of Beyond the Endpoint contains more context on the attack types below, as well as comprehensive analysis of two other threat types—cloud storage abuse and insider threats.
Click here to access the full report.
Email Account Takeover
In email account takeover (ATO), an unauthorized individual assumes control of a legitimate user’s email account. The attacker can then sell the compromised credentials on cybercriminal platforms or exploit the account for various malicious activities, such as data theft, launching additional phishing attacks, or conducting business email compromise (BEC)—a rapidly growing attack type that surged by 246% between February 2023 and February 2024, according to our 2024 Annual Cyber-Threat Report.
The typical lifecycle of an email ATO attack is illustrated in 1.
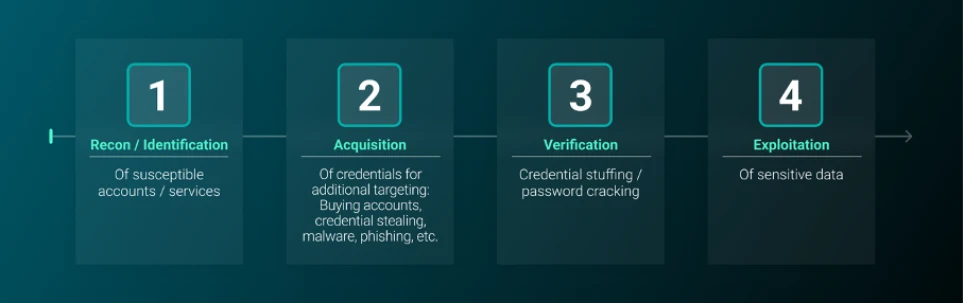
Figure 1: Typical email ATO attack lifecycle
Email ATO can affect both enterprise and home users, potentially compromising associated accounts like social media or banking. A study of ReliaQuest customer incidents in Q2 2024 revealed that 56% of initial access techniques involved phishing, underscoring the significance of email-related threats; you might remember some of our previous reporting identifying this threat.
Unlike traditional attacks, email ATO doesn’t involve compromising the endpoint itself, making it undetectable by EDR systems. Instead, attackers exploit user behavior and email service flaws, often through phishing, credential stuffing, or weak and brute-forceable passwords. Once they gain access, they can manipulate the account remotely, bypassing endpoint security measures.
Given the ubiquity of email in business operations, it remains a critical weak point that attackers frequently exploit; no matter your company size, from enterprise to a family-owned business, you will use email for coordinating daily operations. The ease of executing email ATO, often using prepackaged phishing templates from phishing-as-a-service (PhaaS) tools, makes it a preferred method for infiltrating networks while bypassing your EDR.
For email-based threats, multifactor authentication (MFA) will always be the most effective control. However, there’s much more that can be done: email monitoring tools can identify email rules and permissions, while Group Policy Object (GPO) rules stop users from saving their credentials in the browser, which greatly improves resiliency against threats like information-stealing malware and browser credential dumping.
Adversary-in-the-Middle
Adversary-in-the-middle (AITM) attacks are a subtype of man-in-the-middle (MITM) attacks, where an attacker uses compromised public Wi-Fi, spoofing techniques, or software vulnerabilities to intercept and manipulate communications between two parties who believe they are interacting directly. AITM attacks often aim to bypass MFA or steal sensitive information in real time by actively altering the communication or transaction process. MFA is often considered an infallible control for securing email, but there are methods of circumventing its protection.
Unlike endpoint-level attacks, AITM attacks occur at the network level, where EDR tools lack visibility to detect subtle manipulations. Without complementary tools like intrusion detection systems (IDS) or specialized network monitoring solutions, EDR alone cannot effectively identify and mitigate these sophisticated attacks, leaving opportunities for attackers.
Posts advertising AITM services and techniques are popular on cybercriminal forums. These include website cloning techniques, in addition to advanced attack frameworks like “EvilGinx.” These tools allow attackers to capture login credentials and MFA tokens in real time, emphasizing the ease with which even inexperienced cybercriminals can execute AITM attacks. The widespread sharing of these tools is dramatically lowering the barrier to entry for cybercrime.
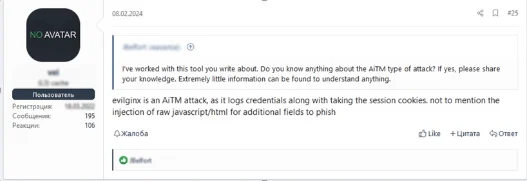
Figure 2: Cybercriminal forum user post alluding to use of EvilGinx AITM attacks
Remediating AITM attacks is crucial because they can intercept, manipulate, and exfiltrate sensitive data during transmission, resulting in severe consequences such as data breaches, credential theft, or unauthorized access to confidential communications. EDR solutions are typically not equipped to detect these network-level threats, leaving attackers able to conduct their activities undetected and potentially undermining your overall security posture.
You wouldn’t let your neighbors open or redirect your mail, so why let remote attackers do the same? Ensure that your websites use strong, up-to-date SSL/TLS certificates, while also mandating that employees only use approved corporate virtual private networks (VPN). This is particularly important when using public Wi-Fi networks, which are common hotspots for AITM attacks.
Targeting Software-as-a-Service (SaaS) Providers
Threat actors can also exploit customer-supplier relationships in SaaS platforms, often starting with phishing attacks to capture login credentials. Once inside, they establish persistence through attacker-controlled tenants or compromised administrative accounts, making it challenging for security teams to detect malicious activity amid legitimate operations.
EDR solutions often miss these threats because attackers use legitimate accounts and native tools within the compromised environment, blending in with normal user behavior. They can also exploit built-in automation tools like Microsoft Power Automate or Google Apps Script to execute tasks covertly, bypassing traditional EDR detection. This limited visibility into SaaS environments leaves organizations vulnerable to sophisticated attacks.
Without adequate oversight, organizations face a deluge of risks, from data breaches, compliance violations, legal penalties, and financial losses. Inadequate monitoring delays incident response and remediation, causing operational disruptions. The exploitation of built-in automation tools exacerbates these risks, enabling attackers to execute malicious tasks without raising alarms. Ultimately, insufficient SaaS monitoring erodes trust with customers and partners, compromising the organization’s reputation and stakeholder relationships.
A good example of this was observed recently in June 2024, with the “Scattered Spider” threat group executing a financially motivated attack by gaining initial access through SMS phishing, SIM swapping, and account hijacking. For further information, please see our other recent reporting on Scattered Spider.
In this campaign, Scattered Spider exploited Okta permissions to access cloud and SaaS applications, created new virtual machines on vSphere and Azure, and disabled security protections, including Microsoft Defender. This allowed them to download tools for lateral movement and use cloud syncing tools to transfer data to platforms like Google Cloud Platform and AWS.
Traditional EDR solutions often miss such activities due to limited visibility in cloud environments and the use of legitimate permissions, making malicious actions appear routine. Scattered Spider’s tactics of blending in with normal operations and disabling security measures helped them effectively evade EDR detection.
Implementing a cloud access security broker (CASB) can provide visibility and control over data and activities within SaaS applications by enforcing security policies, monitoring user behavior, and detecting anomalies that might indicate abuse.
Enhance Your Visibility and Speed of Response
While EDR tools excel at detecting endpoint threats in real time, they lack comprehensive visibility across network traffic and cloud environments. It’s also difficult to gain a unified and comprehensive view of the threats that can bypass EDR. Beyond the Endpoint identifies specific details of how threat actors are bypassing EDR in the wild, with actionable recommendations to minimize the risk.
To address these limitations, EDR must be supplemented with additional security measures. The ReliaQuest GreyMatter security operations platform enhances visibility across environments, automates playbooks through bi-directional integrations, and continuously monitors for gaps and improvements.
GreyMatter consolidates data from multiple sources to provide a unified view of the security landscape, allowing for more accurate detection of threats. By using AI, machine learning, and threat intelligence, GreyMatter improves the ability to identify and respond to complex attacks in real time, reducing the workload on security teams and enabling quicker remediation.