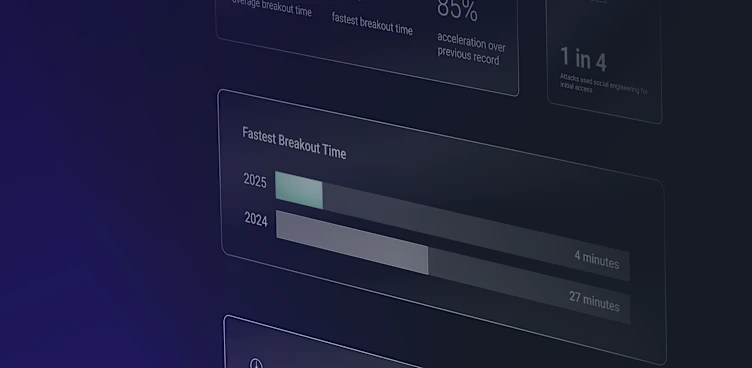
Key Points
A software supply-chain attack enables an adversary to bypass security controls and maintain persistence on target networks due to consumers’ inherent trust in the compromised software. Industries that are heavily dependent on third-party software are particularly susceptible to this attack type due to their larger attack surface.
ReliaQuest forecasts that nation-state–linked threat groups will continue to conduct software supply-chain attacks. Furthermore, this technique will likely be adopted by financially motivated threat actors in the long-term future.
Organizations should take proactive actions to reduce the likelihood of a supply-chain attack impacting their operations. Implementing a supply-chain risk management process can reduce the impact to business operations. Steps include communicating the need for the process, establishing a supplier inventory, documenting security requirements, vetting suppliers regularly, and creating supplier agreements.
The ReliaQuest Threat Research team monitors and reports on supply-chain attacks. We offer enhanced security and immediate notifications to Digital Risk Protection (DRP) customers. ReliaQuest provides detection rules and respond plays to identify and remediate malicious activities from supply-chain compromises.
Software supply-chain compromise involves manipulating a software, service, or delivery method before it reaches the end consumer. By infiltrating the development and distribution processes of a single software variant, threat actors can compromise multiple systems across various organizations, exploiting the inherent trust placed in vendors and deployed software. Organizations that rely heavily on third-party software for business operations are particularly susceptible; such industries and systems include:
Telecommunications: Network management systems, billing systems, data analytics.
Healthcare: Electronic health records, pharmacy management systems, practice management software.
Finance and insurance: Core banking systems, customer relationship management software.
Retail: Inventory management systems, payment processing, e-commerce platforms.
Manufacturing: Computer-aided design, quality management systems, maintenance management software.
Detecting software supply-chain attacks is challenging: These attacks bypass existing security controls and maintain persistence covertly. In addition, vendors may be unaware of the intrusion’s full extent or choose not to disclose it. Threat actors’ motivations for conducting supply-chain attacks vary; they may aim to achieve financial gain, conduct espionage, or destroy data.
This report will examine the reasons threat actors choose this attack methodology, detail various software manipulation techniques, provide real-world case studies, and offer practical mitigation advice to safeguard against this threat.
Advantages of Software Supply-Chain Compromise
There are multiple reasons why threat actors choose to compromise software before it reaches the end user.
Compromising a software supply chain allows attackers to potentially affect many downstream targets. By infiltrating a trusted software provider or a widely used third-party component, they can distribute malicious code to all the users of that software, maximizing the impact of the attack with minimal effort or resources.
Supply-chain attacks exploit the inherent trust that organizations place in their software vendors and third-party components. When a trusted source is compromised, the malicious code is likely to be executed without much scrutiny, bypassing traditional security defenses that might be in place for unknown or untrusted sources.
These attacks can be highly stealthy. Compromised software updates or packages can go unnoticed for long periods, allowing attackers to maintain persistence on target environments and subsequently exfiltrate data, manipulate systems, or prepare for further attacks. Detection and response actions are largely dependent on the impacted software vendor notifying customers.
High-value targets like government agencies, financial institutions, or large enterprises often use third-party software solutions. By compromising the supply chain of these solutions, attackers can gain access to these high-value networks more easily than penetrating through direct attacks.
Software Manipulation Techniques
Attackers gain access to software using common methods like compromised credentials or exploiting public-facing applications. They then employ stealth tactics to evade detection and move laterally across the network, eventually reaching code repositories—critical storage locations for software code and related files—where they can manipulate software in various ways.
Application Source Code or Update Manipulation
Also known as upstream server or code repository compromise, this technique involves injecting malicious code into legitimate files or replacing them entirely with malicious ones, then distributing these compromised software updates or applications to downstream users. As the most prevalent type of supply-chain attack, this technique is particularly difficult to detect, as adversaries ensure the compromised software still functions as expected.
Case Study: 3CX
In April 2023, . To access 3CX, the threat actor exploited a previous supply-chain attack against Trading Technologies’ “X Trader” software. A 3CX employee downloaded a compromised version of X Trader, allowing the new adversary to gain access to 3CX. The threat actor then modified a legitimate 3CX file to include malicious code that was delivered to downstream 3CX customers in an update. 3CX disclosed that its Windows and macOS desktop application were compromised, allowing the threat actors to download and run code on all devices with the app installed. More than 60,000 customers were affected by the supply chain attack, which was attributed to “,” a financially-motivated, North Korea-linked advanced persistent threat (APT) group known for operations that aim to gain revenue to attenuate sanctions against North Korea.
Mitigations and Recommendations
Suppliers: Use Windows AppLocker or Software Restriction Policies (SRP) to implement a whitelist of approved software. AppLocker and SRP can be used to create rules specifying allowed publishers, paths, and file hashes. In this case study, AppLocker or SRP could have blocked the use of X Trader that allowed for the supply chain compromise to occur.
Customers**:**Maintain an up-to-date inventory of software to proactively block applications when supply chain compromise events are announced. Set Windows Defender Exploit Guard Network Protection to proactively block connections to command-and-control servers (C2). This can be enabled in Group Policy Management Editor and by navigating to Microsoft Defender Exploit Guard, selecting Network Protection, and setting “Prevent users and apps from accessing dangerous websites” to block.
Open-Source Software and Dependencies
Instead of targeting vendor products directly, adversaries may compromise a component used to create the final product, such as a dependency (a software component or module that the final product relies on) or open-source software. Developers often incorporate these elements to save time and resources. Threat actors may gain access to repositories by infiltrating the organizations that maintain the software or by building trust with developers to make changes to the code directly. After gaining access, adversaries inject malicious code into the repository directly or include additional malicious files. A successful attack of this type could severely damage the reputation of the compromised organization and the affected developers. Trust in the software ecosystem is eroded, leading to potential loss of business, legal repercussions, and long-term damage to the organization’s credibility.
Case Study: XZ Utils
In April 2024, malicious code was discovered in the widely used compression library “XZ Utils” that could enable remote access. An engineer identified the backdoor after noticing unusually high CPU usage by the secure shell protocol (SSH). The backdoor enabled an attacker with a specific public key to execute commands on remote systems over SSH without authentication. A GitHub contributor with the username “JiaT75” built rapport with the XZ Utils developers and was granted “commit” access to the XZ Utils Github repository, allowing them to implant the backdoor. Although the backdoor’s impact was minimal due to the affected XZ Utils versions being limited to development or desktop versions of Linux, its potential severity was high if incorporated into products that utilize the XZ Utils software. The attack has not been attributed to any group, but its complexity led security experts to suspect a nation-state actor was responsible.
Mitigations and Recommendations
Suppliers: Implement a Secure Software Development Framework (SSDF) that includes verifying whether incorporated software meets security requirements and includes code review. A SSDF can reduce the risk of integrating compromised third-party source code into a final product.
Customers: Request a software bill of materials (SBOM) from vendors to obtain a list of dependencies in their software. This provides an organization with insight into all software in a final product, enabling a quicker response if a dependency is compromised.
Code Signing Compromise
Code signing keys enable developers to create digital signatures to prove the integrity of their software. By obtaining a private key, attackers can digitally sign and deliver malware that appears legitimate and can bypass security controls due to the inherent trust in signed files.
Case Study: Nvidia
In February 2022, “Lapsus$,” a financially motivated criminal group that focuses on data theft and extortion, claimed responsibility for an attack on the multinational chip and graphics processing unit (GPU) manufacturer Nvidia. Although the initial access method is not known, researchers identified that the group routinely purchases compromised credentials to authenticate to virtual private networks (VPNs). Lapsus$ obtained one terabyte of data from the breach, including two code-signing certificates used to verify Nvidia software. Various types of malware were subsequently signed with the Nvidia certificates, including Quasar RAT, Cobalt Strike beacons, and Mimikatz. The signed malware could slip past security controls like antivirus (AV) and endpoint detection and response (EDR) systems.
Mitigations and Recommendations
Suppliers: Follow the FIPS 140-2 standard recommended by the National Institute of Standards and Technology (NIST) requiring physically secure and tamper-evident storage that erases sensitive data if tampering occurs. Access to certificates should be restricted through role-based access control (RBAC). These measures mitigate the risk of sensitive data like certificates from being stolen.
Customers: Enable Windows User Access Control (UAC), which blocks files with revoked certificates from executing. After determining a certificate is compromised, it will be revoked, and security controls will no longer trust the file.
Threat Forecast
As organizations continue to adopt cloud services, microservices architectures, and third-party software, the attack surface for supply chain vulnerabilities expands. This trend is likely to continue, making it easier for attackers to find and exploit weaknesses. The use of open-source components in software development is widespread. While this accelerates innovation, it also introduces risks, as vulnerabilities in widely-used libraries can have a cascading effect across many applications.
Nation-state–affiliated threat groups have used software supply chain attacks to infiltrate vendors’ customers, showcasing their resourcefulness and sophistication. However, financially motivated threat actors continue to adopt advanced techniques used by nation-state–affiliated threat groups , as evidenced by (prior to this, zero-day vulnerabilities were more commonly exploited by nation-state–affiliated threat groups).
Looking ahead, cybercriminal groups will likely conduct supply chain attacks in the long-term (beyond one year), while nation-state actors will likely dominate these tactics in the mid-term (three months to one year). The impact of these attacks will hinge on the attackers’ motivations. For example, in 2017, the Russian GRU military unit 74455, aka “Sandworm,” deployed the “NotPetya” wiper malware via a supply chain attack on Ukrainian accounting software vendor M.E. Doc, causing widespread destruction. In contrast, the 2019 SolarWinds attack by “Cozy Bear” was likely motivated by espionage, targeting U.S. federal agencies without employing data destruction or encryption.
Cybersecurity Supply Chain Risk Management
In May 2022, the National Institute of Standards and Technology (NIST) published “Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations” (C-SCRM) guidance (SP 800-161). This publication describes how organizations can implement a C-SCRM program to make informed decisions about suppliers, helping them to proactively mitigate the risk of a supply-chain attack. The guidance features the following steps.
Implementing C-SCRM
Begin by clearly communicating the need for C-SCRM across the organization. Involve key stakeholders from departments like IT, security, executive management, and risk management.
Next, establish a comprehensive inventory of suppliers, contracts, and products, then evaluate the criticality of each software for business operations.
Lastly, document the security requirements a supplier must follow. Use questionnaires to gather detailed information from prospective suppliers, enabling more informed purchasing decisions.
Vetting Suppliers
After procurement, supplier vetting should be conducted regularly to validate whether current vendors meet acceptable risk standards. Engage directly with vendors to gain visibility into their upstream suppliers, software development lifecycle practices, and security standards. Key due diligence questions include:
Are security controls implemented throughout the software development lifecycle?
What procedures are in place for notifying customers in the event of a breach?
Are software dependencies documented?
How mature is the vendor’s security program?
Create Supplier Agreements
Once a vendor meets acceptable risk criteria, establish contractual requirements to ensure vendors’ compliance. Example requirements include:
Establish information sharing requirements.
Include security controls, such as access controls, principle of least privilege, and remote access controls.
Require a software bill of materials (SBOM), detailing all components incorporated in the final product.
Implement Failover Processes
A C-SCRM plan should incorporate assessments of software criticality for business operations and respective contingency plans for successful supply chain attacks. For critical software, identify alternative suppliers or workarounds and develop associated contingency plans to replace compromised software with minimal operational impact. Conduct software supply chain attack tabletop exercises to familiarize team members with failover procedures.
What ReliaQuest Is Doing
The ReliaQuest Threat Research team is dedicated to monitoring supply-chain attacks. We report on significant updates and share indicators of compromise (IOCs), if available, within the GreyMatter platform and on the ReliaQuest website. IOCs are enriched and incorporated into the GreyMatter threat feed for ReliaQuest customers. For our Digital Risk Protection (DRP) customers, we offer additional layers of security. They receive immediate notifications if a supply-chain attack affects their listed vendors or if a vendor appears on a ransomware data-leak site. Using IOCs, our experts identify abnormal behaviour in compromised software and initiate targeted threat hunts across customer environments. To detect malicious activities stemming from a supply-chain compromise, ReliaQuest offers detection rules. To remediate identified malicious activity, associated GreyMatter Respond Plays can be executed by ReliaQuest customers or by ReliaQuest on the customer’s behalf.