Note: This blog is taken from our recently published Exposed Credentials Solutions Guide, which includes a complete list of our mitigation strategies and free resources to begin monitoring for exposed credentials.
Preventing an account takeover (ATO) or data breach through compromised credentials has never been a small job nor easy job. Unfortunately for security teams, these sorts of breaches have been on the rise as the number of available exposed credentials and ease of access to these credentials increases.
Earlier in 2020, the Photon research team at ReliaQuest uncovered that account takeover has never been easier (or cheaper) for cybercriminals with brute-force cracking tools and account checkers available on criminal marketplaces for an average of $4. In addition to these cracking and credentials stuffing tools, it was found that more than 15 billion credentials are in circulation―up 300 percent since 2018 and coming from 100,000-plus discrete breaches.
In this blog, we’ll jump into the four essential steps to mitigate account takeover through exposed credentials and outline the ways in which threat intelligence can be applied to proactively prevent a breach in your organization.
Get our free research report on ATO prevention best practices, Exposure to Takeover here.
Collect Exposed Credentials
The first step is to identify employee credentials exposed on the open, deep, and dark web (ideally on a continual basis). Newly compromised credentials offer the best chance at access to valid employee accounts, so they fetch the highest prices of the cybercriminal forums. Often upon exposure, these credentials are immediately shared or posted for high prices to criminal forums, dark web marketplaces, Telegram channels, or IRC channels. Later on, these credentials become repackaged and shared more widely across more public forums and paste sites.
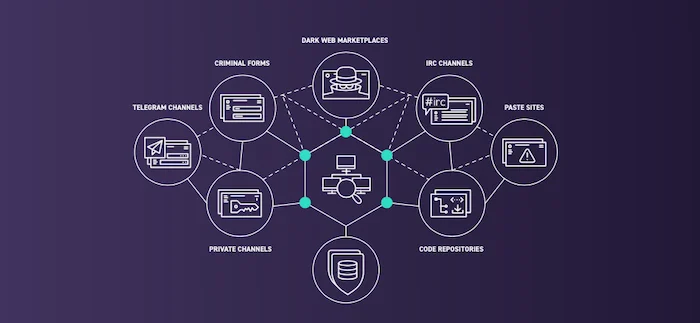
Collection sources for exposed or compromised credentials
Organizations that can detect their employees’ credentials within these breaches as early as possible stand the best chance of preventing access to valid employee accounts.
You can subscribe to a credential monitoring service for free, such as HaveIBeenPwned, to monitor for leaked credentials of your employees. It alerts you to instances of breaches including your organization’s email domain. Although HaveIBeenPwned doesn’t provide you with passwords, it’s a great place to start identifying which accounts are potentially compromised.
You can also sign up for a Test Drive of ReliaQuest GreyMatter DRP to search for recently exposed credentials across paste sites and criminal forums.
Validate the Exposed Credentials
Some organizations make it their policy to automatically reset user accounts, even if no password has been exposed or it’s still unknown if they do or do not provide valid system access. This approach as it can quickly snowball, creating unnecessary friction for users and ultimately leading to password fatigue.
Instead, work efficiently by prioritizing validation of breached credentials that contain both an email AND a password, which makes it easier to determine if they can provide genuine access.
Credential validation can be a winding, time-consuming process. There is no way to identify the age of credentials from the credential itself with many “new” data leaks including credentials from previous leaks, sometimes from a long time ago. Oftentimes, data leaks include partial credentials or credentials which do not even match the standard username and password format of your organization. With a focus on validity, you can reduce time investigating invalid credentials pairs and focus on the important matters.
You can read more about ReliaQuest’ own credential validation methods here.
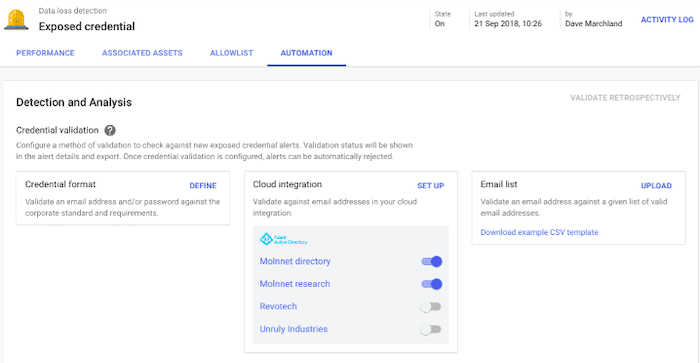
Validating with credential format, email list, or Azure AD integration in ReliaQuest GreyMatter DRP
Contain the Validated Exposed Credentials
There are three possible pathways after a pair has been validated:
Reset the Credential, reset passwords for the associate user.
Conduct Analysis, set up alerts in SIEM systems for unexpected behavior such as logging in to admin systems, moving large amounts of data outside of corporate systems, or going to suspicious domains.
Communicate Incident to the User, notify them of the credential exposure and guide them through resetting a new and secure password.
Once a credential pair has been validated to provide system access, speed to alert the user to reset their passwords becomes key. And not all accounts are equal: C-Level and accounting personnel should be addressed with higher priority. A staggering 33,000 of exposed credentials are for accounting inboxes—these credentials seemingly move faster on the cybercriminal market for the sensitive financial data they provide access to.
Educate the User
Once the initial fire has been put out and the affected credentials have been reset, there is a chance to step back and apply a second coating of security to the situation.
First, the user may still be at risk if they are reusing passwords across multiple other accounts. According to Google, more than 50% of people are suspected to reuse passwords, meaning the exposed credential could still provide access to other corporate systems, cloud services or other third parties. Educate the user of responsible password usage and verify the exposed password was not used for any other purpose.
Second, use data to tailor their training. Some security teams will prevent users from using passwords that are the most commonly used. Check out NordPass’ list of the most common passwords of 2020 for further information.
Lastly, combat password fatigue by applying technical solutions at your organization. The average person uses some 191 services that require them to enter passwords or other credentials. That’s a lot to keep on top of, and it presents a huge problem if compromise occurs, particularly if a person uses the same credentials across multiple services. You can consider technologies such as single sign-on (SSO) and hardware tokens or use multi-factor authentication to strengthen access control for sensitive systems.
For more mitigation strategies, download our Exposed Credentials Solutions Guide.