Organizations invest in a variety of best-of-breed security tools to analyze different threats and strengthen their defenses. However, despite their individual capabilities, these tools often fail to work together seamlessly. This lack of integration scatters critical data across the environment, leading to reduced visibility, manual and tedious processes, and fragmented workflows. Consequently, organizations face increased mean time to resolve (MTTR) and longer dwell times, giving adversaries an upper hand.
To address these challenges, organizations need to integrate their disparate technologies through a centralized security operations platform. This approach reduces manual effort and ensures comprehensive and streamlined TDIR for decreased MTTR. This blog demonstrates how integrating technologies can enhance each pillar of TDIR for an organization.
Detection
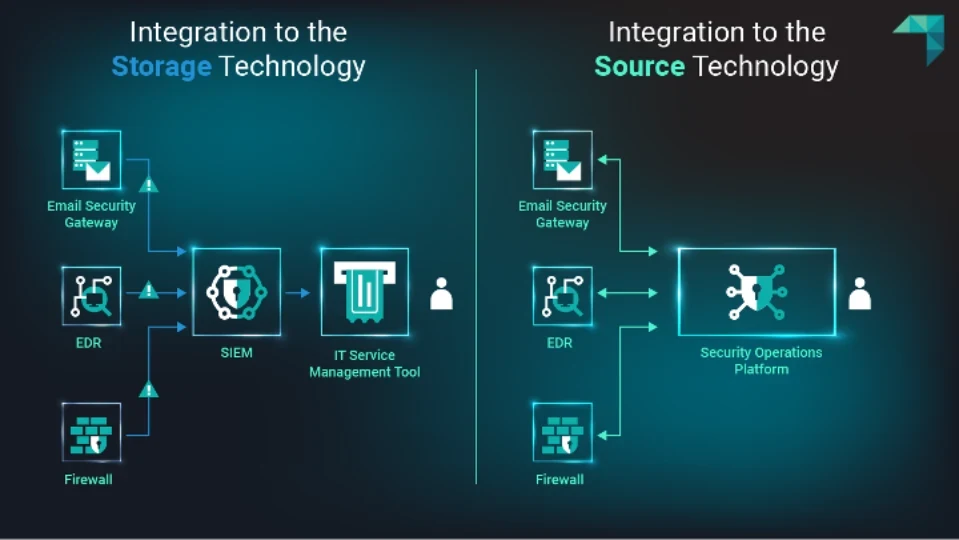
Organizations often rely on storage technologies like SIEMs to collect data logs and generate alerts when malicious activity is detected. However, this approach can lead to slower detection and data normalization challenges. In a traditional setup, where monitoring technologies like email gateways send their logs to a SIEM, the logs need to be appropriately processed and normalized. This process can sometimes affect data integrity and continuity. Additionally, the logs must be correlated with other data sources undergoing the same process before they reach the SIEM, which adds more time. Once an alert is generated, it is usually sent to an IT service management (ITSM) tool, adding another step that can further affect continuity and delays to the process before the alert reaches an analyst.
Instead of sending data out to one place for detection, use a security operations platform to integrate and detect threats directly at the source, providing faster and more dependable detection capabilities. This direct integration eliminates the intermediate step of sending logs to a SIEM, reducing latency and minimizing the delay between data collection and alert generation to ensure timely responses.
The image below compares a traditional detection workflow for an allowed-malicious-email alert, which is integrated with a storage technology, to a workflow that integrates directly with a source technology.
Investigation
After receiving a phishing alert, security teams typically need to use various security tools to investigate and determine the appropriate response actions. However, manually pivoting between multiple technologies often leads to fragmented analysis and inefficient processes and requires specialized expertise to piece together information. This not only slows down the investigation, but also makes it more challenging to respond effectively.
The integration of these tools allows security teams to access all relevant data for an effective investigation from one screen. Centralizing the information needed into a single location reduces the time and effort required to switch between tools, ensuring a swift, consistent, and accurate analysis.
For example, the image below illustrates a traditional workflow for investigating a phishing alert, which might involve navigating through specific security tools to understand the full scope of the alert. In contrast, it also demonstrates how integrating these tools together allows analysts to query all tools and perform analysis from one location.

Response
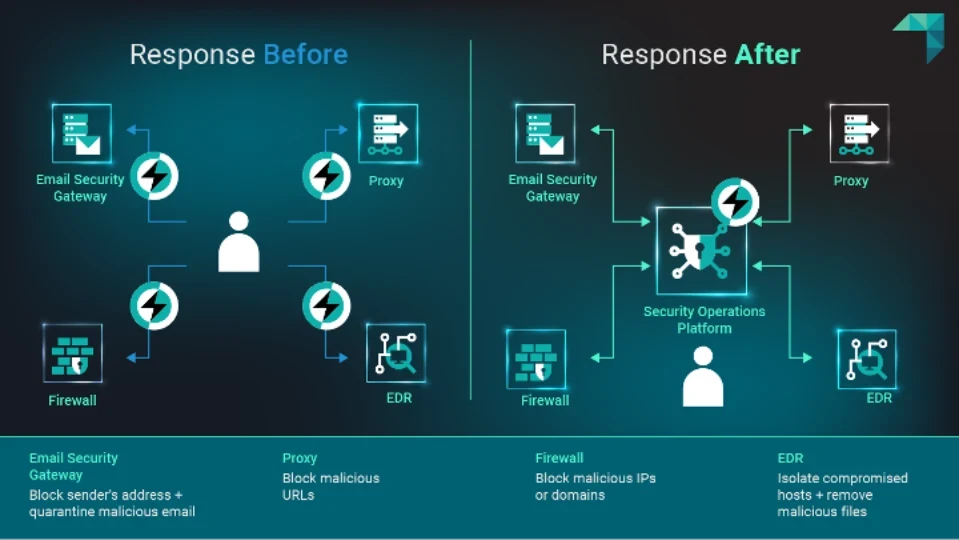
Similar to the investigation phase, if there’s a confirmed phishing threat, security teams manually pivot in and out of multiple tools to contain and remediate the threat. These could be different tools but often they are the same tools used during investigation, leading to more inefficiencies and further delays that provide more time for the adversary to compromise systems.
In contrast, integrating these tools together provides centralized security controls that allow all response actions to be executed from a single location. This integrated approach ensures faster and more efficient threat investigations, ultimately reducing MTTR.
The image below showcases the difference between typical responses to a phishing alert when manually navigating through various tools and when responding with integrated security tools.
Maximize Efficiency with Comprehensive Integrations
By integrating multiple technologies into a security operations platform, security teams can achieve more comprehensive end-to-end coverage. This holistic approach maximizes the effectiveness of security operations and reduces tool pivoting to ensure organizations are better equipped to detect, investigate, and quickly respond to any type of threat.
Consider another scenario involving compromised credentials. Without unifying their tools, security teams must manually navigate multiple tools at each step of the TDIR process. However, joining them together simplifies the entire TDIR workflow, as illustrated below:

Each integration significantly reduces the time spent in each phase of the TDIR workflow, decreasing dwell time and MTTR, and removing the headaches of managing multiple disparate tools.
Unify Security Tools with ReliaQuest GreyMatter
The ReliaQuest GreyMatter agentic AI security operations platform seamlessly integrates with any vendor solution—whether on-premises or in the cloud—to unify your TDIR workflows. With its bi-directional APIs, GreyMatter collects data for investigation and sends response actions for containment and remediation, eliminating tool pivoting between various technologies and significantly reducing MTTR. Additionally, the ReliaQuest Universal Translator normalizes outgoing queries to technologies and the data coming in, promoting automated data stitching across your security infrastructure. This normalization reduces the burden on teams to be experts in each native tool’s query language and provides unified visibility into diverse technology sources.







