Key Findings
The last quarter of 2024 proved to be a pivotal period for ransomware activity, marked by emerging threats and unexpected shifts among established groups. In this report, we’ll cover:
- “LockBit’s” resurgence
- Our original research into “Scattered Spider’s” domain creation methods
- Predictions for 2025
- Key recommendations to safeguard your data
Keep reading to learn about the driving forces behind these trends, gain insights from our in-depth analysis, and find out key takeaways to help your organization stay ahead of the curve in the fight against ransomware.
Ransomware Activity Hits All-Time High in December
Ransomware attacks have been climbing steadily over the past few years, despite some temporary dips along the way. In our Q3 2024 ransomware report, we predicted activity would reach its peak in the last quarter of the year. Unfortunately, December 2024 marked a grim milestone, with the highest number of victims we’ve ever recorded in a single month.
A key factor behind this surge is likely the growth of the ransomware ecosystem itself. In 2022, there were around 60 active ransomware groups, but by 2024, this had ballooned to almost 100. With so many more groups in the game, it’s no wonder we’re seeing record-breaking levels of activity.
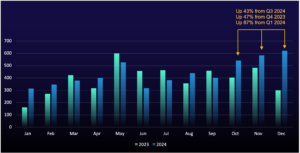
The increasing profitability of these attacks is likely luring more cybercriminals into establishing ransomware groups. Researchers reported that the median ransom payment rose from $199,000 in 2023 to $1,500,000 in 2024.
But it’s not just the money that’s driving this trend. Recent successful law enforcement actions against major ransomware gangs like LockBit and “ALPHV” have made joining the big groups increasingly risky for cybercriminals. As global takedowns target high-profile operations, many threat actors are shifting toward smaller, more decentralized groups that are more likely to fly under the radar. Law enforcement is less likely to dedicate the intense scrutiny and resources required to dismantle the ransomware gangs toward these smaller operations.
More active ransomware groups means a higher likelihood of being targeted, significantly increasing the threat to organizations of all sizes. The risk is further heightened by the wide range of tactics and techniques these groups employ, complicating defense efforts against potential attacks. A more crowded landscape will likely drive ransomware operators to demand higher ransoms and adopt more sophisticated attack strategies to ensure their market share. Beyond the immediate cost of a ransom payment, the financial burden of a ransomware attack can include regulatory fines, public relations and reputational damage, breach notification and identity protection costs for affected parties, as well as legal fees and potential lawsuits—turning a single cyber incident into a prolonged and costly ordeal that may take years to fully recover from.
RansomHub Holds the Lead as Akira’s Activity Surges
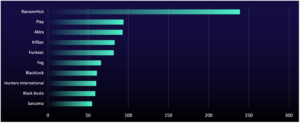
While many prolific groups increased their activity levels in Q4 2024, “Akira” stands out the most. The group more than doubled its Q3 count of 48 organizations and named a staggering 71 in December alone.
It’s realistically possible that this late surge in activity relates to Akira’s strategic exploitation of CVE-2024-40766, an access control flaw in SonicOS. To gain access to internal networks, Akira targeted local accounts with disabled multifactor authentication (MFA) and SonicOS firmware versions vulnerable to exploitation, often exposed to the internet for virtual private network (VPN) access. Once inside, the attackers moved laterally, stole data, deployed ransomware, and established backdoors for persistent access. Given the success of these tactics, it’s highly likely that Akira and other ransomware groups will continue to exploit similar weaknesses in future attacks.
| Group To Watch | |
|---|---|
| Name: | “BlackLock” (aka El Dorado) |
| Type: | Ransomware-as-a-service (RaaS) group |
| Emergence: | March 2024 |
| Victimology: | US-based real estate, manufacturing, PSTS, and health care organizations |
| Highlight: | Activity rose 1,425% from Q3 to Q4 2024 |
| Encryption: | Unique Go-based ransomware builder compatible with Windows and Linux. ChaCha20 for file encryption and RSA-OAEP for key encryption |
| File Impact: | Appends files with ".00000001" extension and leaves ransom notes with attacker contact instructions |
| Anti-Recovery Measures: | Deletes shadow volume copies to prevent recovery and auto-deletes itself after execution to evade forensic analysis |
Take Action
To mitigate these threats, organizations should ensure SonicWall and other VPN products are fully patched and up to date. Restricting firewall management access to trusted sources and, where possible, disabling internet access to the wide area network (WAN) management portal can further strengthen defenses. Additionally, Secure Sockets Layer (SSL) VPN usage should be limited to trusted sources or disabled if unnecessary.
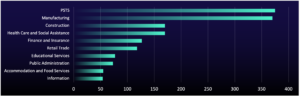
US, Manufacturing, and PSTS Remain Top Targets
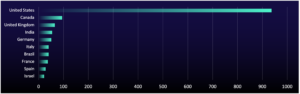
Over the past two years, ransomware groups have disproportionately targeted US organizations, driven by perceptions of strong financial capacity and cyber insurance coverage. In Q4 2024 alone, nearly half of the 1,110 initial access listings we collected—often the starting point for ransomware attacks—were related to US-based companies.
The sectors targeted by ransomware groups have also remained consistent: Professional services and technical services (PSTS) and manufacturing companies are primary targets because of their economic importance, low tolerance for operational downtime, and higher willingness to pay ransoms.
- Manufacturing firms depend on vulnerable industrial control systems (ICS), Industrial Internet of Things (IIoT) devices, and outdated legacy systems. When left unpatched, they become appealing targets to ransomware groups.
- The PSTS sector relies heavily on VPNs and remote monitoring and management (RMM) tools to support remote work. Without strict access controls, these tools can facilitate unauthorized lateral movement.
As long as this approach continues to generate financial returns, ransomware gangs are unlikely to change their focus.
Take Action
ReliaQuest customers can use hunt packages like “Remote Monitoring & Management (RMM) Software | Windows Service Installation” to assess the scope of RMM software in their environment and detect malicious use for backdoors or data exfiltration.
Key Developments in Q4

Highest Jump Yet of 2024: 13 New Groups Emerge in Q4
In Q4 2024, the emergence of new ransomware groups reached its peak. However, unlike their Q3 predecessors, which initially listed only a handful of victims, newcomers in Q4 like “SafePay” and “FunkSec” quickly ramped up their activity, claiming 45 and 82 victims, respectively. This surge has been fueled by the easy availability of leaked source code on cybercriminal forums. For example, in October, a user on the Russian-language forum XSS shared the source code for “Photon” ransomware, and researchers have identified multiple new groups reusing older code. This access allows newcomers to launch significant attacks with minimal investment, intensifying competition as groups rush to capture market share.
Even if many groups carry out only a few attacks, their growing numbers amplify the overall risk. It takes just one successful attack by a single group to cause significant disruption for an unlucky organization. While groups are still widely unknown, the lack of intelligence about them—their targets, methods, or IOCs—makes these attacks harder to predict and prevent.
Take Action
It’s realistically possible that the success of new ransomware groups in Q4 2024 will inspire a wave of fresh operations in 2025. Organizations can use threat hunting and behavioral analytics to spot early signs of ransomware attacks, such as unusual file encryption or lateral movement. Additionally, deception technologies like honeypots can divert attackers and provide valuable intelligence to refine response plans.
Arrests Slash Victim Count, But LockBit Teases a Resurgence
As part of “Operation Cronos,” an international law enforcement operation that took place in October 2024, four individuals were arrested and servers linked to LockBit were seized—marking the third major strike against the group in 2024. Once the world’s most prevalent ransomware, targeting industries like finance, health care, and energy, LockBit’s operations have been severely disrupted by these coordinated actions. As a result, their victim count has plummeted from 176 in May 2024 to just five in December.
Despite the recent setbacks, LockBit remains resilient, recently teasing its latest variant, LockBit 4.0, sending out the message that it’s not backing down. While there aren’t many details about the new variant, LockBit’s history of innovation—exemplified by the advanced evasion techniques of LockBit 3.0 and the introduction of the first macOS ransomware—shows its ability to adapt. Similar groups like “REvil” and “DarkSide” have also rebounded after law enforcement crackdowns.
Take Action
Preparing for novel malware is challenging, but focusing on security fundamentals is key. Educating users to prevent common phishing attacks and auditing external-facing assets for vulnerabilities can help block LockBit’s likely tactics. In addition, ReliaQuest’s Threat Research team is closely monitoring LockBit 4.0 to deliver timely detections for GreyMatter customers.
Scattered Spider Powers RansomHub’s Q4 Success
In November–December 2024, the US Department of Justice indicted five individuals and arrested another tied to Scattered Spider—a group accused of SMS phishing and exploiting corporate systems. Active since August 2023, Scattered Spider initially partnered with the ransomware-as-a-service (RaaS) group ALPHV (aka BlackCat) before shifting to “RansomHub” after ALPHV’s disbandment. By mid-2024, Scattered Spider’s hallmark tactics, including social engineering and SIM-swapping, were evident in RansomHub’s double extortion attacks, cementing their collaboration.
Despite recent arrests, Scattered Spider’s decentralized structure and vast network of over 1,000 members ensure that its operations will likely remain largely unaffected. The group’s adaptability—evident in its seamless transition to RansomHub—and its expertise in social engineering keep it highly valuable to ransomware partners. RansomHub’s emergence as the most active group in Q4 2024 also speaks to Scattered Spider’s uninterrupted influence.
Take Action
Since Scattered Spider’s tactics rely on human error rather than technical sophistication, we recommend organizations use phishing-resistant MFA such as WebAuthn or Public Key Infrastructure (PKI) based authentication. This technology leverages cryptographic techniques to strengthen security and avoid vulnerabilities in less-secure options like SMS-based MFA.
Untangling Scattered Spider’s Domain Creation Web
Scattered Spider typically starts its attacks with targeted social engineering, impersonating employees or executives to trick help desks into resetting credentials, thus bypassing MFA. Our research indicates that the group often registers lookalike domains 12-24 hours before an attack, mimicking the target organization or its services.
To better understand Scattered Spider’s targeting strategies and naming conventions, we analyzed the domains that the group registered between October 1, 2024 and January 1, 2025. We uncovered distinct patterns:
| Target Type | % of Domains | Group’s Likely Intention |
|---|---|---|
| Single Sign-On (SSO) and Identity Providers | ~30% | Domains like "organization-sso.com," “adfs-organization.com,” or "organization-okta.com" aim to impersonate identity management systems, critical for controlling access to internal applications. |
| Help Desk and IT Support | ~20% | Domains such as "organization-helpdesk.com," "organization-servicedesk.com," or “organization-hr.com” mimic IT portals to deceive employees and harvest credentials. |
| VPN and Secure Access | ~15% | Domains ending in "organization-vpn.com" target remote-access systems, allowing attackers to collect credentials from corporate VPN users. |
| Gateway and Network Infrastructure | ~20% | Domains like "organization-gateway.com" and “organization-internal.com” focus on network access points, facilitating authorization for internal systems. |
| Other | ~20% | These include domains designed to impersonate miscellaneous internal tools, cloud services, or other organization-specific platforms. These domains are tailored to exploit less common but critical aspects of an organization’s infrastructure, such as “organization-salesforce.com.” |
These domains are specifically designed to facilitate credential harvesting and are intentionally used for only a very brief period before being taken down. This short lifespan allows the domains to remain active just long enough to execute attacks but not long enough for defenders to identify, analyze, and block them as known IOCs.
So What?
Based on the patterns identified in our research, organizations should monitor for the registration of domains that mimic key systems, including SSO (e.g., “organization-okta.com”), help desks (e.g., “organization-helpdesk.com”), VPNs (e.g., “organization-vpn.com”), and internal infrastructure (e.g., “organization-gateway.com”). Detecting these lookalike domains early is crucial for disrupting phishing and social engineering campaigns before they begin.
These recommendations are based on key actionable findings from our research, as shown in the table below:
| 70% | of the domains imitate a specific organization | Indicates a targeted strategy to exploit trust and maximize social engineering success. Defenders should monitor for lookalike domains with solutions like GreyMatter Digital Risk Protection. |
| 30% | of the domains imitate hosts for common services such as Binance and Coinbase | Indicates a targeted strategy to exploit trust and maximize social engineering success. Defenders should monitor for lookalike domains with solutions like GreyMatter Digital Risk Protection. |
| 25–30% | of the group’s domains targeted manufacturing companies | Suggests a preference for high-income sectors. These sectors are lucrative targets given their involvement in critical infrastructure, operational dependencies, and access to valuable assets like intellectual property and financial data. |
| 20–25% | of the group’s domains targeted finance and insurance companies | Suggests a preference for high-income sectors. These sectors are lucrative targets given their involvement in critical infrastructure, operational dependencies, and access to valuable assets like intellectual property and financial data. |
| 50% | of the targeted domains in the information sector related to telecommunications providers | Reflects Scattered Spider’s continued emphasis on critical infrastructure. This persistent targeting of telecom providers may tie back to the group’s history in SIM-swapping, as access to these organizations would allow them to scale up their SIM-swapping operations. |
Step Up Your Defense Against Ransomware
ReliaQuest’s Approach
AI Agent: ReliaQuest’s GreyMatter platform now features an autonomous AI agent that enhances security operations by analyzing threat patterns, automating ransomware detection, and speeding up response times. This innovation cuts the mean time to contain (MTTC) threats and strengthens organizations’ cybersecurity defenses, allowing for more effective responses to ransomware attacks.
Threat Intelligence: ReliaQuest also actively tracks the ransomware landscape, identifying emerging groups, updating threat profiles, monitoring data-leak sites, and refining IOCs to equip organizations with the intelligence they need to anticipate and counteract ransomware threats.
Detection Rules: ReliaQuest recommends customers implement the following detections, built on the latest threat intelligence and original research, to strengthen defenses against both established and emerging ransomware strains.
By deploying detections together with GreyMatter’s Automated Response Playbooks, organizations can drive down their MTTC from hours to just minutes. Rapid responses are crucial in minimizing ransomware damage. We advise customers incorporate the following Automated Response Playbooks into their incident response plans for a more robust and efficient defense strategy:
- Terminate Active Sessions and Reset Passwords: Ransomware operators abuse stolen credentials to move laterally, gaining access to high-value data. This playbook cuts off an attacker’s access by terminating hijacked sessions and resetting compromised credentials.
- Delete File: This playbook automatically removes ransomware payloads from a host’s directory, halting the execution of ransomware files before they can encrypt critical systems and data, minimizing attack impact.
- Disable User: Ransomware operators often exploit compromised user accounts to use unauthorized PowerShell scripts for data theft. When suspicious PowerShell activity is detected, this playbook disables affected user accounts, immediately halting the attacker’s actions. In addition, aligning PowerShell policies with user roles further minimizes abuse.
Your Action Plan
This report is full of ransomware insights, but these three quick-win measures are key to implement right now.
- Adopt risk-based authentication to dynamically adjust access requirements based on user behavior, device, and location. Set policies to flag unusual activity, like logins from unknown locations, to prevent breaches before they escalate.
- Implement and regularly review immutable backups to protect critical data from tampering or deletion. Test these backups frequently and store them offline or on a separate network to ensure quick recovery during a ransomware attack.
- Enforce password policies based on users’ roles and access levels and ensure regular password updates. Frequently changing passwords renders stolen credentials useless, reducing the risks of unauthorized access that lead to ransomware deployment and enhancing security for high-access roles.
Top Lessons and What’s Next
Ransomware attacks reached record highs in Q4 2024, with 13 new groups, including SafePay and FunkSec, rapidly scaling their operations. This report highlights the growing sophistication and variety of tactics used by ransomware groups, as well as their resilience and adaptability, even when set back. Together, these trends reveal an increasingly volatile and advanced threat landscape that demands proactive and cutting-edge defenses. Looking ahead, ransomware tactics will likely evolve even further throughout 2025.
Smarter and Faster Ransomware, Powered by AI: In 2025, we expect ransomware groups to adopt generative AI (GenAI) and large language models (LLMs) more in their operations to automate and enhance critical tasks, such as crafting convincing phishing emails, creating realistic deepfakes, and identifying zero-day vulnerabilities. Activity on cybercriminal forums where ransomware groups operate reveals growing interest in using AI-driven tools, with discussions around deepfakes and AI-generated malware gaining traction. To counter these advancements, organizations must train end users to critically evaluate communications and verify identities, as AI-generated phishing attempts and deepfakes become more deceptive and sophisticated. As AI accelerates malicious activities, security teams must embrace equally efficient and adaptive strategies, using AI-driven defenses to keep pace with evolving threats.
BlackLock’s Explosive Trajectory Will Eclipse RansomHub: We predict that by the start of Q3 2025, BlackLock will overtake RansomHub as the most active ransomware group. In the last quarter alone, BlackLock’s victim count skyrocketed by over 1,000%, and we’ve already seen before in similar groups—including RansomHub—how rapid growth can propel a group from obscurity to dominance in just a few months. Of course, it’s realistically possible that BlackLock’s trajectory could also mirror the rise-and-fall pattern seen with other groups. “PlayBoy,” for example, collapsed shortly after launching its RaaS platform in October 2024 due to financial and internal challenges, highlighting how even promising groups can falter. Given that BlackLock commonly targets ESXi servers, organizations should keep virtualization systems updated, implement vCenter network access control with an allowlist, and enforce ESXi smart-card authentication to restrict unauthorized access and prevent ransomware deployment.




